Error: Windows device status: Access denied
Issue Description
Windows device status displays Access Denied post adding the device or while attempting to collect logs. The Access denied error indicates an issue with permissions or security settings preventing access to WMI (Windows Management Instrumentation) on a remote computer. This can be due to incorrect DCOM (Distributed Component Object Model) security settings, firewall rules, or insufficient user rights.
Possible cause
- Insufficient User Rights: The user account used, might not have the necessary permissions to access WMI on the remote machine.
- Incorrect Credentials: An incorrect username or password can result in access denial.
- Firewall Blockage: Firewalls can block communication between the client and server, preventing WMI connections. Ensure the necessary ports are open.
- DCOM access or security issues: The user does not have remote access to the computer through DCOM or machine DCOM security hardening does not allow the connection.
- WMI Service issues: WMI service related issues may impact the log collection process which needs attention on the service running on affected machine.
Prerequisites
1. Provide a Domain admin privileged user account or create a Service account with minimum privileges
2. Ensure the Ports and Firewall rules are enabled as per recommendation.
3. Ensure that both EventLog Analyzer and monitored computer are patched with latest WIndows updates.
2. Ensure the Ports and Firewall rules are enabled as per recommendation.
3. Ensure that both EventLog Analyzer and monitored computer are patched with latest WIndows updates.
4. All of the following services should be running and set to an “Automatic” startup type for WMI monitoring on a Windows host:
- DCOM Server Process Launcher
- Remote Procedure Call (RPC)
- RPC Endpoint Mapper
- Windows Management Instrumentation
And the following service(s) may be set to a “Manual” startup type:
- WMI Performance Adapter
Resolution
1. Verifying WMI Connectivity with WBEMTEST tool: This helps in narrowing down where the issue occurs and to isolate if the issue is caused in native or in EventLog Analyzer.
Follow the below steps to check WMI connectivity.
ii. Choose Connect
iii. Enter namespace as: \\<device_name>\root\cimv2 where <device_name> should be Device name value as identified by EventLog Analyzer. Screenshot below
iv. Provide credential that you use is EventLog Analyzer for log collection and click Connect.
NOTE:
- For Domain joined machines, provide username value as "Domain\username"
- If you are unable to connect using Namespace with Device name value, try with a different format(IP address/Hostname/FQDN) to see if it a DNS related issue.
- Connect using a different credential (say domain admin) to check if it is related to user rights.
Solution:
If either one of the Device name value connects, review the DNS setup and ensure the DNS resolution happens among the Name Resolution Elements for having the connection using the Device name value in WBEMTEST tool.
If you are able to connect with Domain admin credential but not the service account, check the privilege provided for the service account in as per ManageEngine's recommendation.
If the above solution does not resolve, following are the cases and steps to resolve.
Case 1: If you are able to connect using WBEMTEST, however the device status is marked as "Access Denied" in EventLog Analyzer console, check User rights and Incorrect credentials
If the above solution does not resolve, following are the cases and steps to resolve.
Case 1: If you are able to connect using WBEMTEST, however the device status is marked as "Access Denied" in EventLog Analyzer console, check User rights and Incorrect credentials
Case 2: If you are unable to connect using WBEMTEST, this indicates this is related to native connectivity.
2. User rights and Incorrect credentials: Check if the error is due to Insufficient User Rights or Incorrect credentials in EventLog Analyzer, update the user credential with a domain admin account or a Service account with minimum privilege for the respective device to start/resume log collection.
For domain joined machines:
ii. Navigate to Settings >> Device >> Windows device. Update the respective device to enable check box to choose "Use domain credentials" .
You can also enter the domain credentials manually for the device.
You can also enter the domain credentials manually for the device.
iii. You can perform bulk update or update credential on multiple devices. You can use the filter option to filter the devices based on Device status, Device State, Device Group, and Device Type. The best option here would be Filter based on Device State and set the State as "Inactive" to identify the devices which do not collect events. Enable check box for those devices >> Select more option >> Credentials. You can enter the domain credential manually or enable the check box to choose "Use domain credentials" which uses the credentials used in Domains & Accounts. Save the selection to take effect.
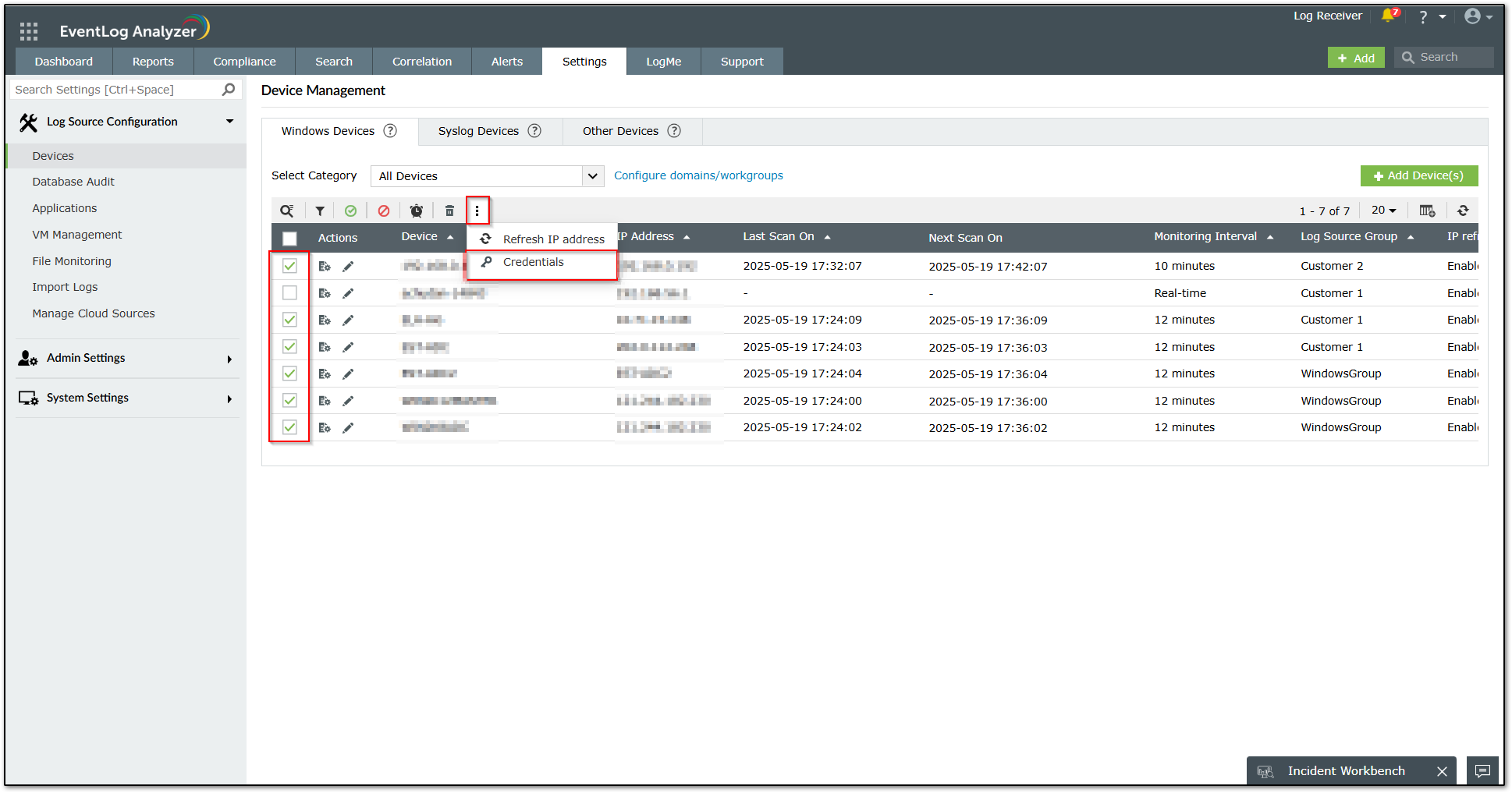
If you are able to connect using WBEMTEST using Device name value and user account but the same credentials does not work in EventLog Analyzer, contact support for further assistance.
For Workgroup Machine:
Navigate to Settings >> Device >> Windows device. Update the credential for the respective device. Choose "Verify Credential" to validate the connection and save it.
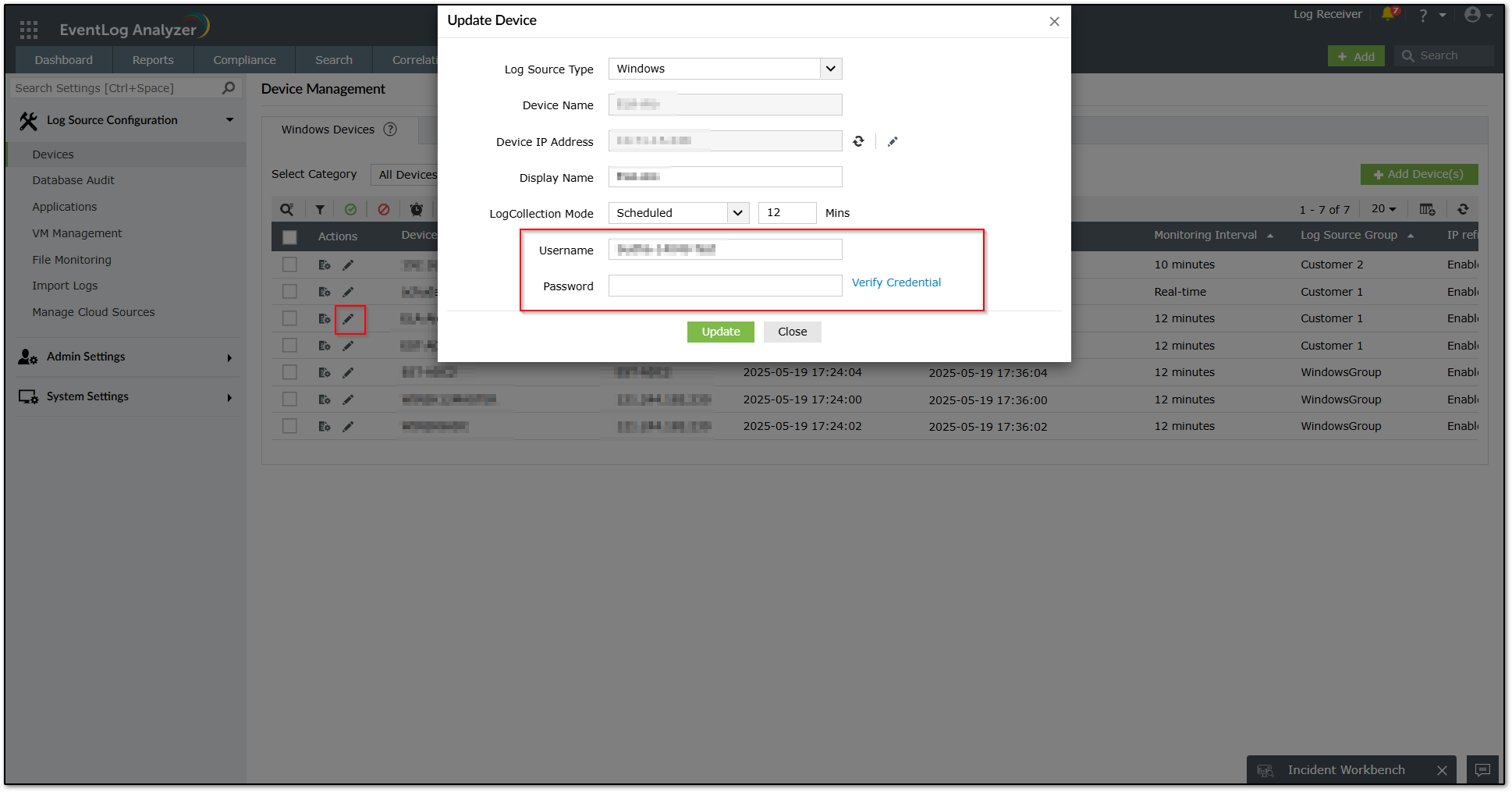
Navigate to Settings >> Device >> Windows device. Update the credential for the respective device. Choose "Verify Credential" to validate the connection and save it.
Once updated, wait for 5 - 10 minutes to see the status getting updated to success.
If you are able to connect using WBEMTEST using Device name value and user account used in application but the same credentials does not work in EventLog Analyzer, contact support for further assistance.
If you are able to connect using WBEMTEST using Device name value and user account used in application but the same credentials does not work in EventLog Analyzer, contact support for further assistance.
3. Native Possibilities :
Access denied error may occur due to various environmental factors which are to be validated in the native end. Below are a few possibilities and solutions for the same.
Ports & Firewall:
Ports & Firewall:
EventLog Analyzer and monitored computer communication play a key role in the remote access connection. Check and ensure if all the ports and firewall rules are allowed in the network as recommended in Windows Log collection - Prerequisites
DCOM Access & Security Issues:
Check if the user has remote access to the computer through DCOM. Open Run, type DCOMCNFG, and then click OK.
Check if the user has remote access to the computer through DCOM. Open Run, type DCOMCNFG, and then click OK.
i. Check if Distributed COM is enabled on the monitored computer.
- In the Component Services dialog box, expand Component Services, expand Computers, and then right-click My Computer and click Properties.
- In the My Computer Properties dialog box, select Default Properties and ensure if "Enable Distributed COM on this computer is enabled"
ii. Check if 'Remote DCOM' is enabled in the monitored computer. If it is not enabled, enable it as follows:
- In the My Computer Properties dialog box, click the COM Security tab.
- Under Access Permissions, click Edit Limits.
- In the Access Permission dialog box, select/add the user account used in EventLog Analyzer in the Group or user names box. In Permission for DistributedCOM Users, enable check box under Allow for Remote Access and click Ok.
- In the My Computer Properties dialog box, click the COM Security tab.
- Under Launch and Activation Permissions, click Edit Limits.
- In the Access Permission dialog box, select/add the user account used in EventLog Analyzer in the Group or user names box. In the Allow column under Permissions for User, select Remote Launch and Remote Activation, and then click OK.
WMI Vulnerability: DCOM Hardening & Event ID 10036
Microsoft released security updates for WMI DCOM communication (CVE-2021-26414) which may break existing WMI connections. You may see Event ID 10036 and errors like "Access is denied" post-patch.
Event ID: 10036
Event Type: System Event
Event Source: DistributedCOM
Message:
Event ID: 10036
Event Type: System Event
Event Source: DistributedCOM
Message:
"The server-side authentication level policy does not allow the user %1\%2 SID (%3) from address %4 to activate DCOM server. Please raise the activation authentication level at least to RPC_C_AUTHN_LEVEL_PKT_INTEGRITY in client application."
(%1 – domain, %2 – user name, %3 – User SID, %4 – Client IP Address)
When the relevant patch is applied on the server, the RequireIntegrityActivationAuthenticationLevel registry value is disabled by default.
If this value is enabled on the server without updating the client system (either by not applying the corresponding patch or making necessary configuration changes), it may disrupt DCOM RPC communication between the server and client. This results in an “Access Denied” error during remote operations.
Solution:
- Update the EventLog Analyzer server OS with latest windows update.
- Update the monitored Windows devices OS with the windows update.
This ensures that both systems use the updated DCOM settings (RequireIntegrityActivationAuthenticationLevel and RPC_C_AUTHN_LEVEL_PKT_INTEGRITY), restoring secure WMI communication.
As of March 14, 2023, Microsoft enforces DCOM hardening by default with no rollback. Refer to Microsoft documentation for detailed guidance: Windows DCOM Server Security Feature Bypass (CVE-2021-26414)
Other WMI Errors:
Check if this is related to WMI error in EventViewer of the monitored computer and resolve it. Refer Core WMI provider error codes to know more.
Validation and testing
- Check device status in EventLog Analyzer Console in the Manage Devices page.
- Confirm logs are ingested correctly.
- Perform WBEMTEST to test connection.
Tips
- Initially test with domain admin credentials
- Confirm firewall/ports are open
- Review service account privileges are managed, and credentials are updated regularly.
- If you find the steps as tedious process, you can install EventLog Analyzer - Windows Agent for log collection.
- Check Windows Event Viewer errors while performing WBEMTEST in monitored computer to understand Windows internal errors.
Related topics and articles
Windows device status: RPC server is unavailable
How to reach support
- Error screenshot in console.
- Observation based on the above steps.
- WBEMTEST result with device name value and credential used.
- Window Event Viewer errors (if applicable)
New to ADSelfService Plus?
Related Articles
Windows device status: RPC server is unavailable
The RPC server is unavailable error will be displayed in the device status field if there isn’t any communication between the EventLog Analyzer server and the respective machine from which the logs should be collected. This lack of communication ...Network device status shows 'Device not Reachable'
Issue description A network device in EventLog Analyzer will display the status "Device not Reachable" if the last message received by the EventLog Analyzer server from the device is greater than 24 hours. This message will display in the log sources ...How to use a Device Group in EventLog Analyzer to update credentials for Windows devices
Objective This article offers detailed information on how to use a Device Group in EventLog Analyzer to update credentials for Windows log sources. Prerequisites You'll need administrator access to EventLog Analyzer. Steps to follow Step 1: Log in to ...No data or logs collected from syslog device
Issue description During the initial setup or while using EventLog Analyzer, you might notice that logs are not being collected from a syslog device or that syslog device reports do not show any recent data. EventLog Analyzer uses device status ...How to migrate EventLog Analyzer standalone edition to different server or drive [Windows to Windows]
Objective This article provides a detailed step-by-step guide to migrate EventLog Analyzer Standalone instance (not integrated with Log360) to a new server or different server or drive. Prerequisites Refer to the System Requirement to plan the new ...