How to enable multi-factor authentication for RDP
Generally, remote employees use Microsoft Remote Desktop Protocol (RDP) to connect to their work devices from an external network, using only a password to authenticate their devices. This makes RDP-based access highly vulnerable to password-based attacks like brute-force attacks.
Implementing multi-factor authentication (MFA) helps thwart unauthorized remote access attempts to employee devices. ADSelfService Plus' MFA feature can secure local and remote access to Windows, macOS, and Linux machines and help secure logins via RDP.
How to enable MFA for RDP using ADSelfService Plus
Prerequisites:
- ADSelfService with Endpoint MFA is required to configure this feature. Visit the store to purchase Endpoint MFA.
- SSL must be enabled in ADSelfService Plus.
- The Windows logon agent that comes bundled with ADSelfService Plus must be installed on the machines that are going to be secured via RDP MFA.
- Access URL must be set to HTTPS: Navigate to Admin > Product Settings > Connection > Connection Settings > Configure Access URL and set the Protocol option to HTTPS.
Steps involved:
- Log in to the ADSelfService Plus admin portal.
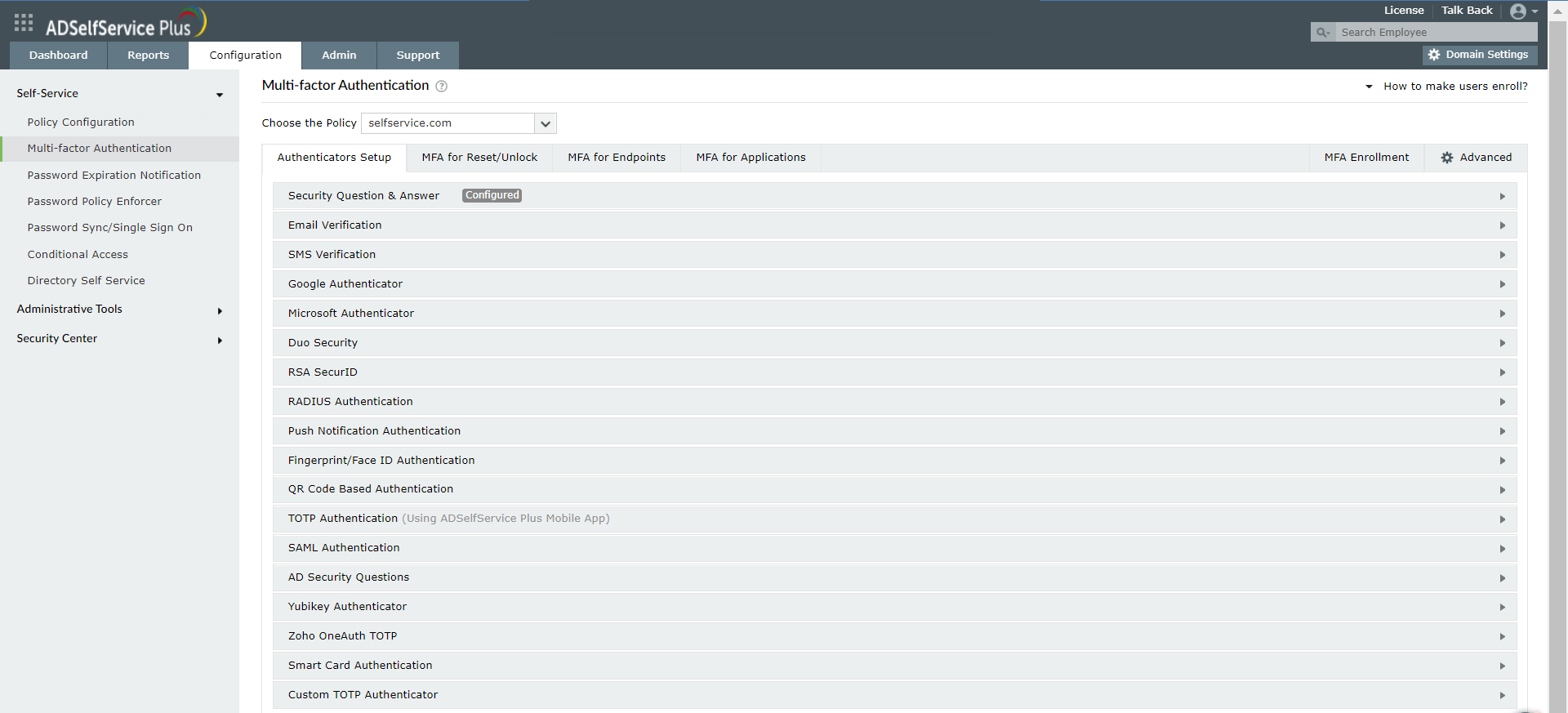
- Navigate to Configuration > Multi-factor Authentication > Authenticators Setup.
- Click the Choose the Policy drop-down, and select the policy for which you wish to enable MFA. This policy will determine which users will have MFA for RDP logins enabled.Note: ADSelfService Plus allows you to create OU- and group-based policies. To create a policy, go to Configuration > Self-Service > Policy Configuration > Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- Configure any of the authenticators present according to organizational preference. ADSelfService Plus supports 19 authentication methods.
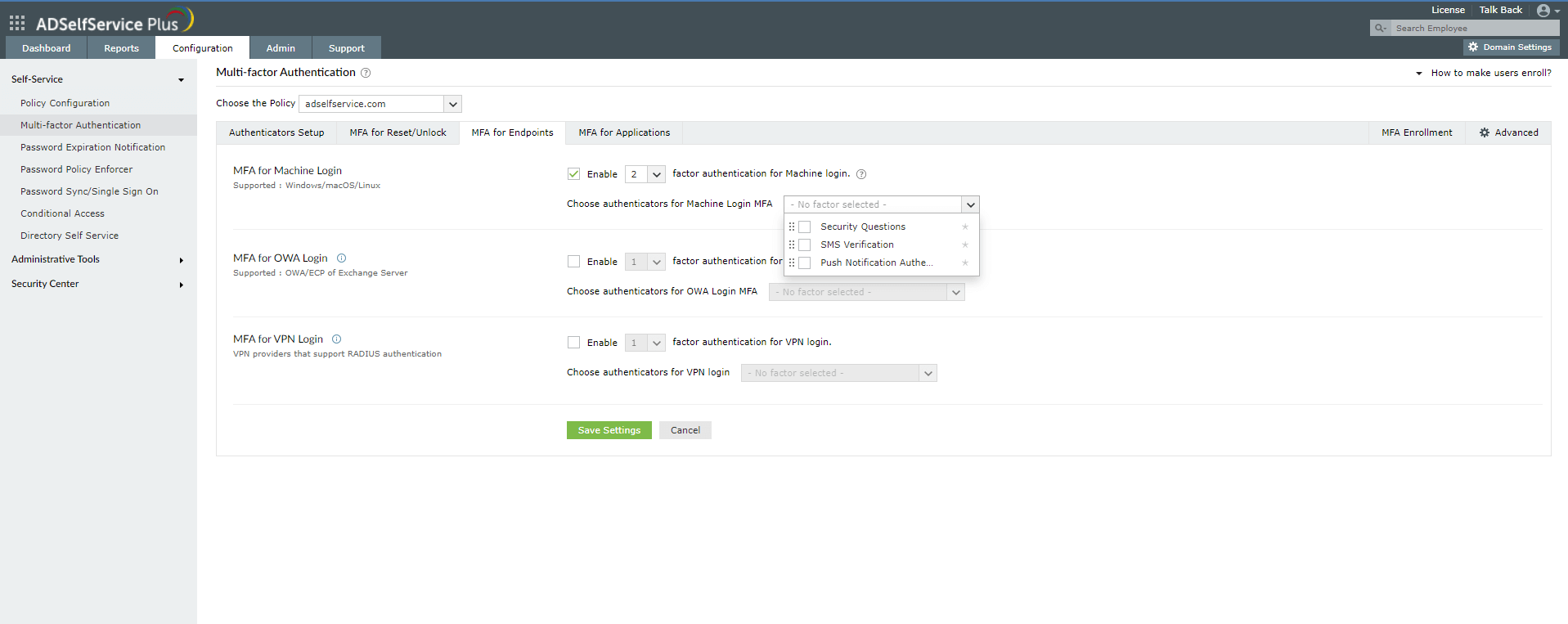
- Navigate to Configuration > Multi-factor Authentication > MFA for Endpoints.
- In the MFA for Machine Login section, check the box next to Enable _ factor authentication for machine login, and choose the number of authentication factors you'd like to implement.
- Choose the authentication methods you would like to implement.
- Click Save Settings.
Benefits of using MFA for RDP logins using ADSelfService Plus
- Customized configuration: Enforce MFA for RDP and use different sets of authentication techniques for different users based on domain, OU, and group memberships.
- Ensure user adoption: Automate user enrollment for MFA for RDP by importing domain information of users through CSV files or force enrollment using login scripts.
- Get detailed reports: Gain comprehensive insights on user activities such as identity verification failures and login attempts, and find users with weak passwords.
- Simplify authentication: Use authentication techniques like fingerprint authentication, push notification authentication, YubiKey, and QR-code-based authentication to help users complete the RDP MFA process with minimal effort.
New to ADSelfService Plus?
Related Articles
How to enable offline MFA in ADSelfService Plus
ManageEngine ADSelfService Plus supports offline multi-factor authentication (MFA) for Windows machine logins, User Account Control (UAC) prompt elevation, and Remote Desktop Protocol (RDP) server authentication when the product server is ...Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...How to enable smart card authentication in ADSelfService Plus?
ADSelfService Plus supports smart card authentication which enables users to access the self-service portal securely, without having to enter a password. If your organization already utilizes smart cards, PKI, or certificates as an authentication ...How to safeguard local and remote Windows logons via ADSelfService Plus' endpoint multi-factor authentication
With cyberattacks on the rise, having only passwords as a defense mechanism is no longer safe. An additional filter is required to restrict unauthorized users. ADSelfService Plus handles this situation by supporting multi-factor authentication (MFA) ...How to enable Zoho OneAuth TOTP for MFA?
In enterprise networks, user identity verification is no longer carried out simply through usernames and passwords. This is because without additional authentication layers, i.e., multi-factor authentication, enterprise networks and resources become ...