How to enable smart card authentication in ADSelfService Plus?
ADSelfService Plus supports smart card authentication which enables users to access the self-service portal securely, without having to enter a password.
If your organization already utilizes smart cards, PKI, or certificates as an authentication system, the sensible choice would be for you to use the smart card authentication option in ADSelfService Plus to verify users' identities. This option enables ADSelfService Plus to authenticate users by comparing the certificate file in their machine with that in Active Directory. The authenticated users will then be automatically logged in to the ADSelfService Plus web console by clicking the Smart Card link.

This article gives you the step-by-step instructions to enable smart card authentication in ADSelfService Plus.
Prerequisites
- Navigate to Admin > Product Settings > Connection. Select the HTTPS Mode radio button, and enter the port number. Click Save.
- Obtain the CA Root Certificate from a certificate authority (CA). Keep this certificate safe as you will need this file while configuring the smart card authenticator. If you are using a Windows server as your CA, download the certificate file from: http://<CertificateAuthorityServerName>/certsrv/.


- Smart Card Authentication can be used only for ADSelfService Plus web portal login.
- When Smart Card Authentication is enabled, load balancing cannot be enabled.
- Smart Card Authentication will not work when reverse proxy is enabled.
- The Trust this browser option is not supported in Smart Card Authentication.
Configuration steps
- Log into the ADSelfService Plus web portal with Admin credentials.
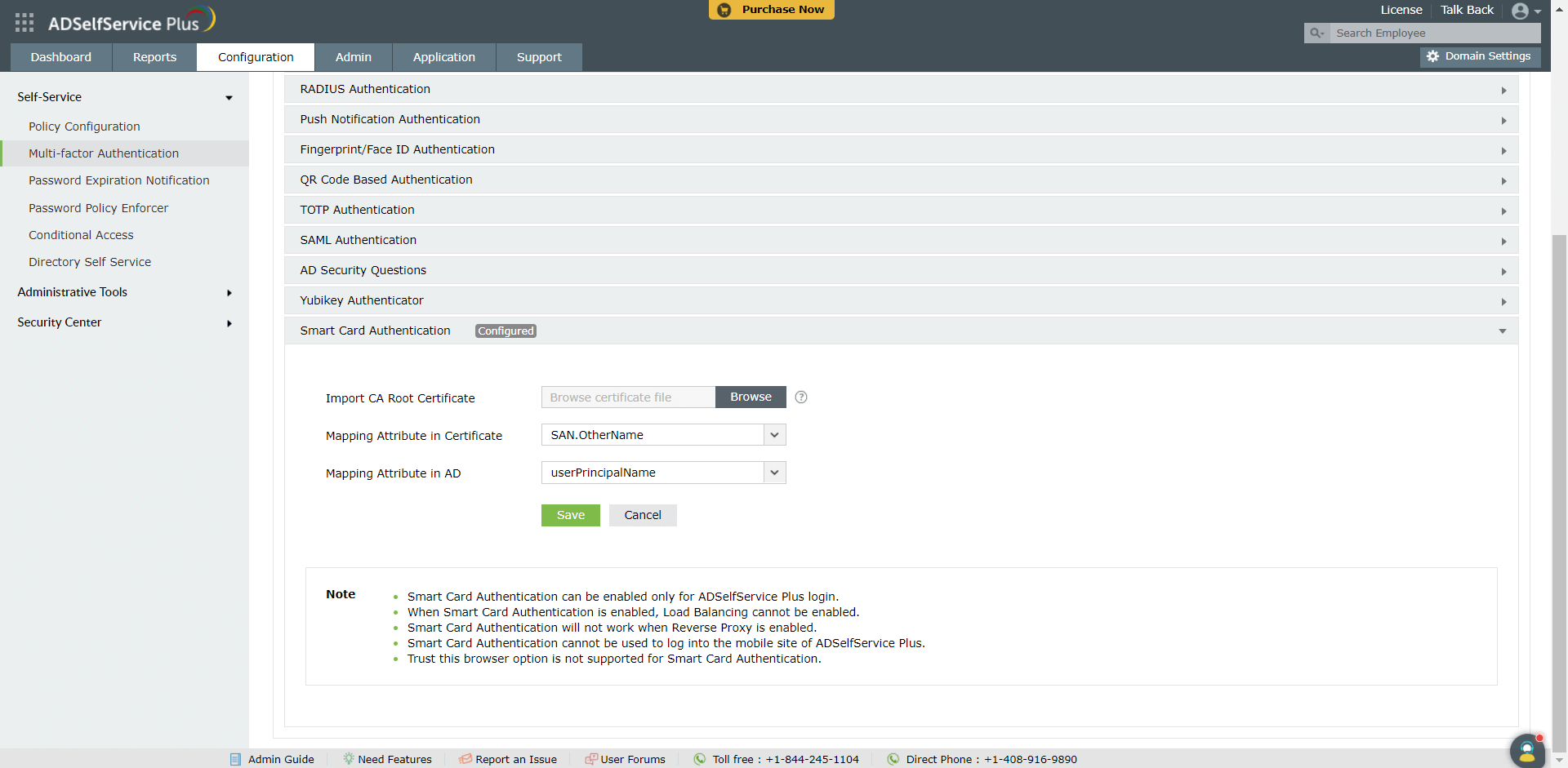
- Navigate to Configuration > Multi-factor Authentication > Smart Card Authentication.
- In the Import CA Root Certificate field, click Browse to import the required root certification file (X.509 certificate). (To obtain a CA Root Certificate, refer to step 2 in the Prerequisites section above.)
- Select a unique attribute in the certificate for mapping from the Mapping Attribute in Certificate drop-down list.
- Ensure that a unique attribute from the certificate is mapped to a unique attribute in AD. Both attributes must have the same value.
- ADSelfService Plus allows you to select any attribute of the smart card certificate that uniquely identifies a user. The available attributes are SAN.OtherName, SAN.RFC822Name, SAN.DirName, SAN.DNSName, SAN.URI, emailaddress, DN, and CommonName. You can also add other attributes that are used to uniquely identify the user in your environment by entering the attribute name in the text box provided and clicking the + icon.
- Specify the LDAP attribute that should be matched with the specified certificate attribute from the Mapping Attribute in AD drop-down list. You need to specify the particular LDAP attribute that uniquely identifies the user in AD (for example sAMAccountName).
- During authentication, ADSelfService Plus compares this value and the certificate attribute that you specified in the certificate's mapping attribute to verify the user's identity.
- Click Save.
- Restart ADSelfService Plus for the changes to take effect.
New to ADSelfService Plus?
Related Articles
Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...How to enable offline MFA in ADSelfService Plus
ManageEngine ADSelfService Plus supports offline multi-factor authentication (MFA) for Windows machine logins, User Account Control (UAC) prompt elevation, and Remote Desktop Protocol (RDP) server authentication when the product server is ...How to enable Zoho OneAuth TOTP for MFA?
In enterprise networks, user identity verification is no longer carried out simply through usernames and passwords. This is because without additional authentication layers, i.e., multi-factor authentication, enterprise networks and resources become ...Configuring fingerprint authentication for Active Directory password resets and logins
Fingerprint authentication is an identity verification method that is widely used in recent times. The fact that everyone has a unique fingerprint makes it one of the more secure methods of authentication. Fingerprint authentication is also simple ...How to enable multi-factor authentication for RDP
Generally, remote employees use Microsoft Remote Desktop Protocol (RDP) to connect to their work devices from an external network, using only a password to authenticate their devices. This makes RDP-based access highly vulnerable to password-based ...