How to safeguard local and remote Windows logons via ADSelfService Plus' endpoint multi-factor authentication
With cyberattacks on the rise, having only passwords as a defense mechanism is no longer safe. An additional filter is required to restrict unauthorized users. ADSelfService Plus handles this situation by supporting multi-factor authentication (MFA) for all Windows login attempts.
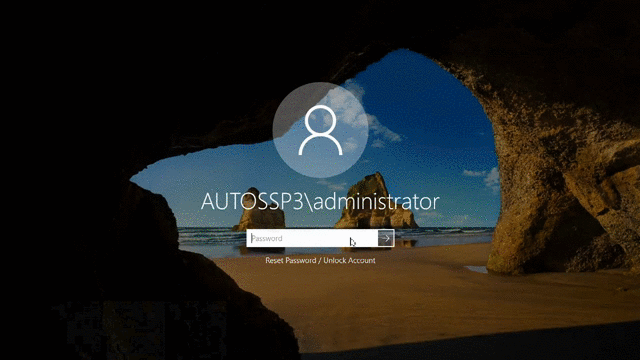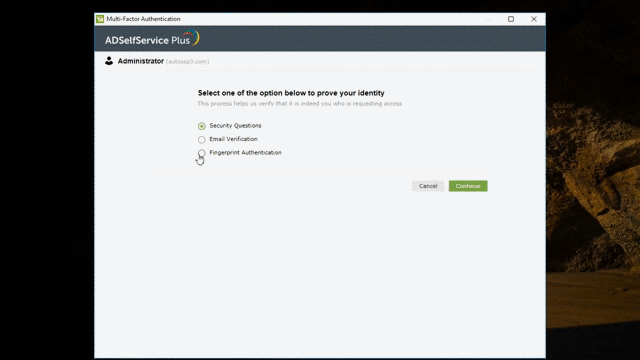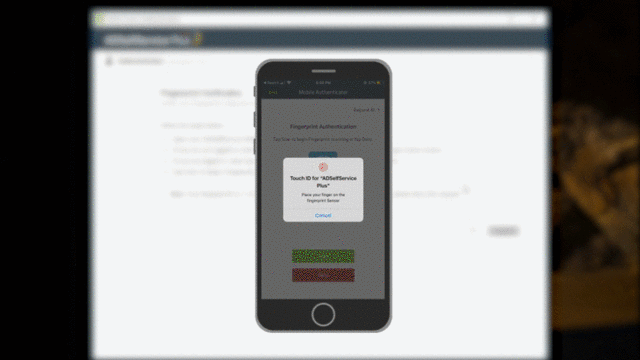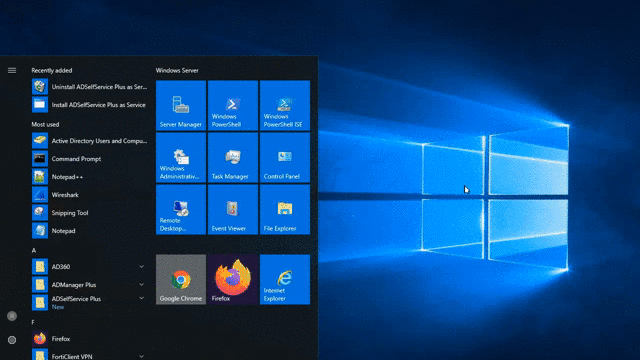
Once this feature is enabled, users will be authenticated once using their Active Directory domain credentials and again through any one of the eighteen authentication methods available in ADSelfService Plus.
Prerequisites:
- SSL must be enabled: Log in to the ADSelfService Plus web console with admin credentials. Navigate to the Admin tab > Product Settings > Connection. Select the ADSelfService Plus Port [https] option. Refer to this guide to learn how to apply a SSL certificate and enable HTTPS.
- Access URL must be set to HTTPS: Navigate to Admin > Product Settings > Connection > Connection Settings > Configure Access URL and set the Protocol option to HTTPS.
- Enable the required authentication methods.
- Install ADSelfService Plus login agent for Windows, macOS, and Linux on the machines where you want to enable MFA.
Steps involved:
- Log in to the ADSelfService Plus web console with admin credentials.
- Navigate to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for which sets of users.
 Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy. - In the MFA for Machine Login section, check the Enable __ factor authentication box, select the number of authentication methods, and specify which ones you'd like to use from the drop-down.
- Click Save Settings.
 Note: Under Advanced → Endpoint settings, ADSelfService Plus offers the Skip MFA when ADSelfService Plus server is down or unreachable option. If this option is not selected, users will not be able to access their machines when ADSelfService Plus is not accessible. However, enabling this option is not recommended, as ADSelfService Plus offers features that ensure constant availability of the product: High Availability and Load Balancing.
Note: Under Advanced → Endpoint settings, ADSelfService Plus offers the Skip MFA when ADSelfService Plus server is down or unreachable option. If this option is not selected, users will not be able to access their machines when ADSelfService Plus is not accessible. However, enabling this option is not recommended, as ADSelfService Plus offers features that ensure constant availability of the product: High Availability and Load Balancing.
With high availability, two instances of the product are created and the secondary instance takes over when the primary instance is down. Load balancing splits the incoming requests to the ADSelfService Plus server among multiple instances to ensure better performance of the product. These features ensure that users have continuous access to the MFA feature and therefore constant access to their machines.
Here's how Windows Logon MFA works:
New to ADSelfService Plus?
Related Articles
Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...Sequential ADSelfService Plus Windows agent login installation process
This article highlights the process sequence for the ADSelfService Plus Windows login agent installation via the admin portal and the prerequisites to be addressed to successfully complete each step. Additionally, we're also discussing some common ...How to enable offline MFA in ADSelfService Plus
ManageEngine ADSelfService Plus supports offline multi-factor authentication (MFA) for Windows machine logins, User Account Control (UAC) prompt elevation, and Remote Desktop Protocol (RDP) server authentication when the product server is ...Updating the ADSelfService Plus Login Agent in Windows
The ADSelfService Plus login agent can be installed on machines running Windows manually, through the ADSelfService Plus admin portal, via GPOs, SCCM, and tools like Endpoint Central. You can update the Windows login agent to its latest version in ...Configuring the ADSelfService Plus login agent for machine MFA and password self-service in Linux
Securing data and resources on the corporate network is of paramount importance to organizations. In a world where most corporate attacks originate at an endpoint, ADSelfService Plus offers 20 MFA factors to protect endpoints by allowing access only ...