Discovering Root Jail in ISC BIND servers
Discovering Root Jail In ISC BIND Servers
What is root jail?
A root jail in ISC BIND refers to a security mechanism used to limit the access of the BIND process to a specific portion of the file system. This is done by just changing the root directory to a subdirectory creating a "chroot jail" (change root jail), which confines the BIND service to a designated directory tree. For example, '/var/named/chroot'becomes the root directory '/ '.
How root jail works:
- Chroot Environment: When BIND is run inside a chroot jail, it is restricted to operating within a specific directory (for example, /var/named/chroot). From BIND's perspective, this directory becomes the root (/) directory, meaning it cannot access files or directories outside of this jail.
- In a root jail, you are effectively "jailed" within the directory structure, as you cannot move higher than the root (/). This means you cannot access directories that are higher in the system's hierarchy (such as /usr, /var, /lib, etc.). Your view of the file system is limited to the specific directory that has been set as the root in the chroot environment.
- For a root jail to function correctly, all necessary paths and library directories must be accessible within the jailed environment. For example, since libraries are typically located in /usr/lib, and if you are jailed in /home, you won't have access to /usr/lib. Therefore, you must recreate the directory structure within the jail, such as /home/usr/lib, which appears to the jailed process as /usr/lib.
- Additionally, any files, directories, and configuration files required by the application must be placed in the correct locations within the jail. While setting up a chroot jail is straightforward, building a functional jail that meets all the application's dependencies is more complex, as it involves ensuring that all necessary libraries and files are available within the confined environment, tailored to the specific requirements of each daemon.
- Enhanced security : This isolation enhances security because even if the BIND service is compromised, the attacker would only have access to the files within the chroot environment and not the entire file system of the server. This minimizes the potential damage an attacker can cause.
Discovering chroot jail while adding servers in DDI Central
To successfully integrate all the contents in the chroot directory into the DDI Central UI, all you have to do is inform DDI Central whether you want to discover the chroot directory or not by selecting or No . Choosing Yes, DDI Central prompts you to enter the relative path of the CHROOT directory. Enter all the other essential details for the discovery and click Save.
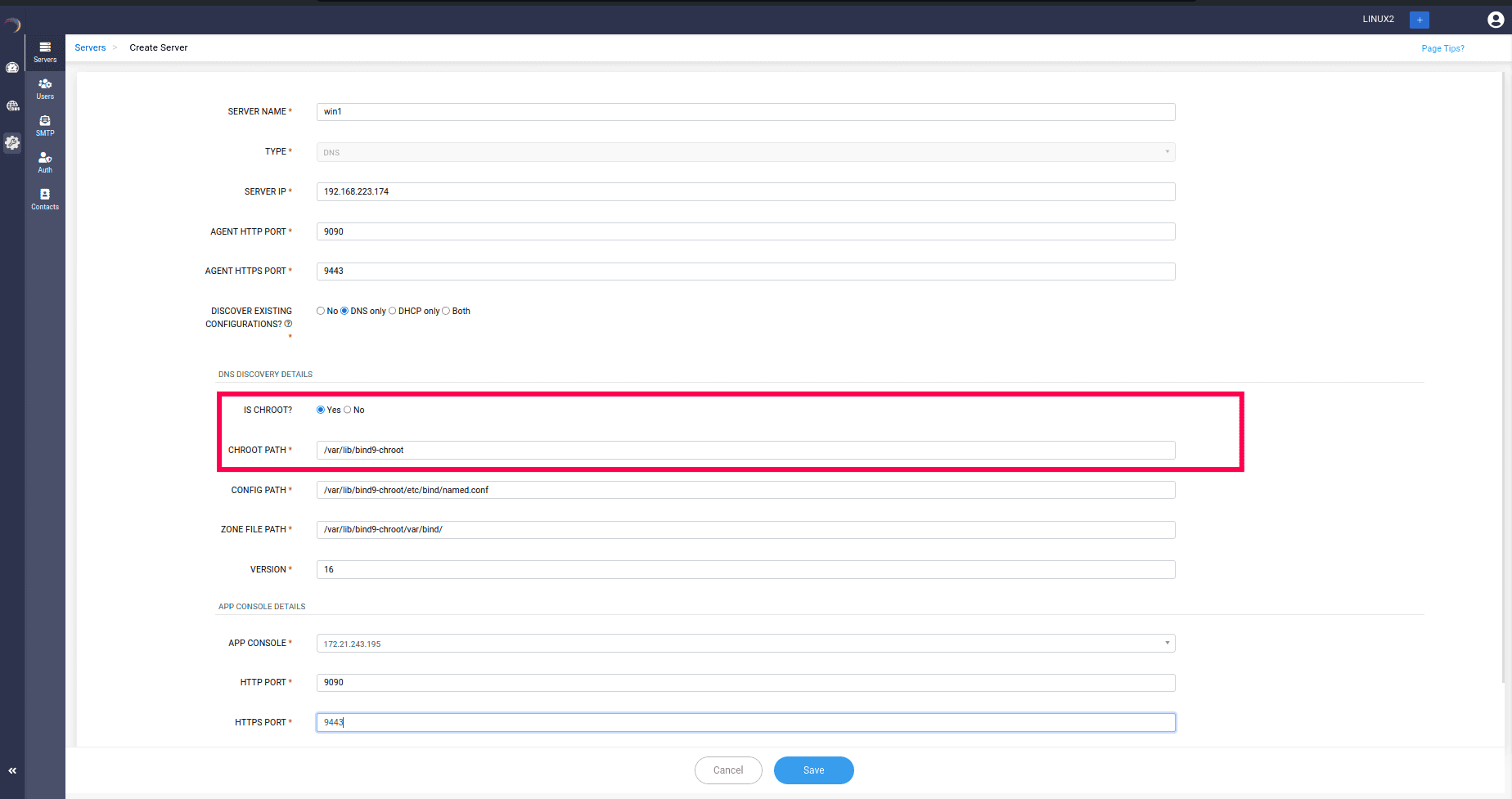
After successful discovery of DNS configurations
Once DDI Central has completed discovering all the necessary configuration files, zone files, and libraries within the chroot directory, it converts all relative paths within the service directory to absolute paths. Therefore a DDI Central admin, should ensure the following steps are followed:
- Remove the root directory from the service file.
- Deploy the following command: systemctl daemon-reload
- Restart the BIND service.
New to ADSelfService Plus?
Related Articles
FAQs for Linux ISC BIND
FAQ for the Linux based ISC-BIND and ISC-DHCP Which Linux distributions are supported? DDI Central supports major distributions such as Ubuntu 16–20.04, CentOS 8, Fedora Linux 31, Red Hat Enterprise Linux 7–9.1, and Debian. Do I need root access to ...Adding Windows DNS-DHCP servers
Note: PowerShell version 5.1.2 or higher is required for a successful setup. Ensure that Windows Remote Management services are running on the Windows DNS and DHCP servers you plan to onboard into DDI Central's Management UI Console. Step 1. WinRM ...Adding servers
Adding Servers Creating Servers Once the cluster is created, you'll be immediately directed to the Servers page to add your DNS and DHCP servers. If not, you can add servers by selecting the Settings menu from the menu bar along the left side of the ...Monitoring servers
Monitoring servers To monitor the load and performance of your DNS and DHCP servers: Select Settings-> Servers. The Servers page appears listing the servers added. First it displays the status of the DNS, DHCP4, and DHCP6 services of the cluster. DDI ...Rsyslogs and Live logs for Linux based DNS and DHCP servers in DDI Central
Rsyslog and Live Logs for Linux-based DNS and DHCP Servers in DDI Central What is Rsyslog? Rsyslog is an advanced and high-performance logging system used primarily in Linux and Unix-based operating systems that enables administrators to collect and ...