Configuring YubiKey authentication for Active Directory password resets and logins
YubiKey Authenticator is a hardware authentication device that is widely used as a multi-factor authentication (MFA) method. Authentication using this method involves plugging the YubiKey device into a user's machine or tapping it against the user's mobile device. A code is generated on the device and is automatically entered on the authentication screen and the user is authenticated into the service.
Since the code is generated and automatically entered in mere seconds, there is no chance of attackers figuring out the passcode and using it to breach the user's account.
Active Directory-based user actions like domain logins have for long been secured only by the rudimentary username and password. While the purpose of these credentials is to verify user identity, the advancement of technology has left them prone to breaches. Implementing an MFA method like YubiKey Authenticator in addition to the default username-password authentication during Active Directory domain logins can be extremely beneficial to an organization's domain network security. Another useful application is during self-service Active Directory password resets and account unlocks.
ADSelfService Plus, an Active Directory self-service password management and single sign-on solution, supports MFA using YubiKey Authenticator and 18 other methods. MFA is used by ADSelfService Plus to secure the following actions:
- Active Directory self-service password reset or account unlock actions via the ADSelfService portal, ADSelfService Plus mobile app, and native Windows/macOS/Linux login screen.
- Windows, macOS, and Linux logins.
- Enterprise application logins through single sign-on (SSO).
- Self-update of Active Directory profile information, subscription to mail groups, and employee search using ADSelfService Plus.
Prerequisite
- The firewall should have the outbound connections listed below:
- Get the Client ID and Secret Key from the YubiKey website by following the steps below:
- Go to https://upgrade.yubico.com/getapikey.
- Enter your email address. Connect the YubiKey to your workstation or server and enter the YubiKey OTP.
- Select the I've read and accepted the Terms and Conditions option. Click Get API Key.
- Copy the displayed Secret Key.
Steps for YubiKey Authenticator verification
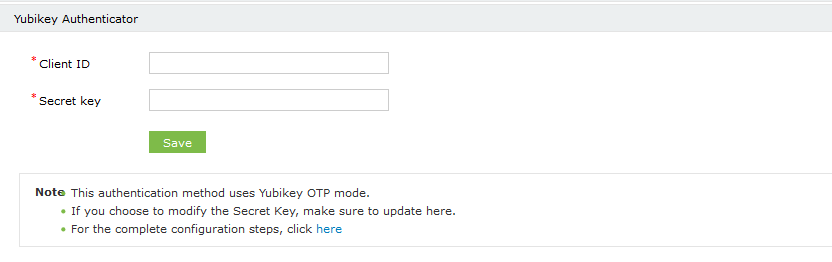
- Go to Configuration > Self-Service > Multi-factor Authentication > Authenticators.
- Select the policy for which YubiKey Authenticator is to be configured from the drop-down.
- Click the YubiKey Authenticator section.
- Enter the Client ID and the Secret Key from step 2 of the prerequisites.
- Click Save.
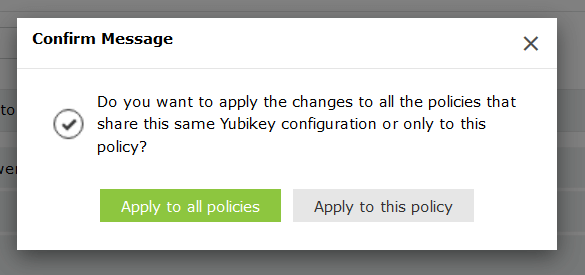
Note: You can choose to enforce multiple configurations for different users based on their domain, group, or OU membership, or simply apply one YubiKey Authenticator setting for all users.
Enable YubiKey Authentication for Active Directory password resets
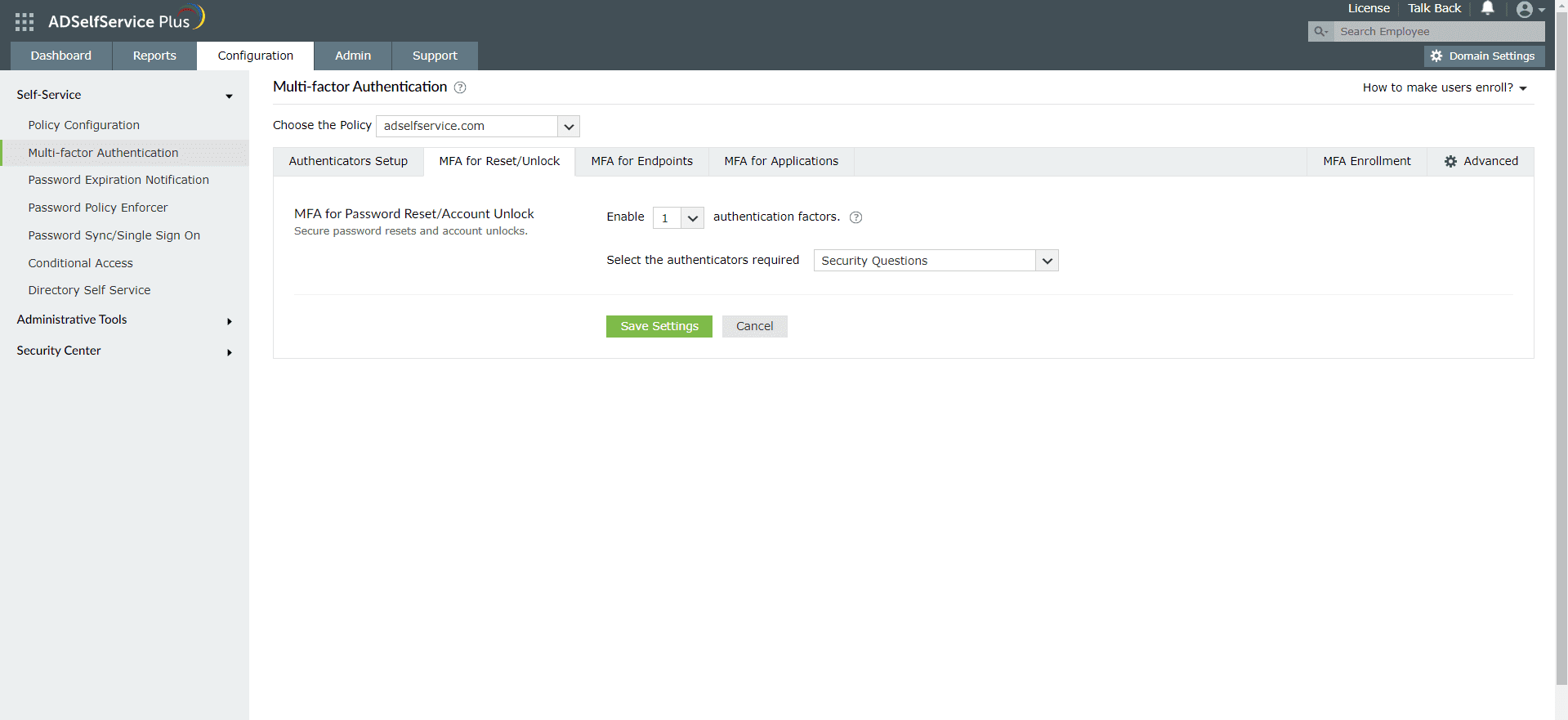
- Go to Configuration > Self-Service > Multi-factor Authentication > MFA for Reset/Unlock. In the MFA for Reset/Unlock section, enter the number of authentication factors to be enforced, and select YubiKey Authentication along with the other authentication techniques to be used.
- Click Save Settings.
Enable YubiKey Authentication for Active Directory domain logins
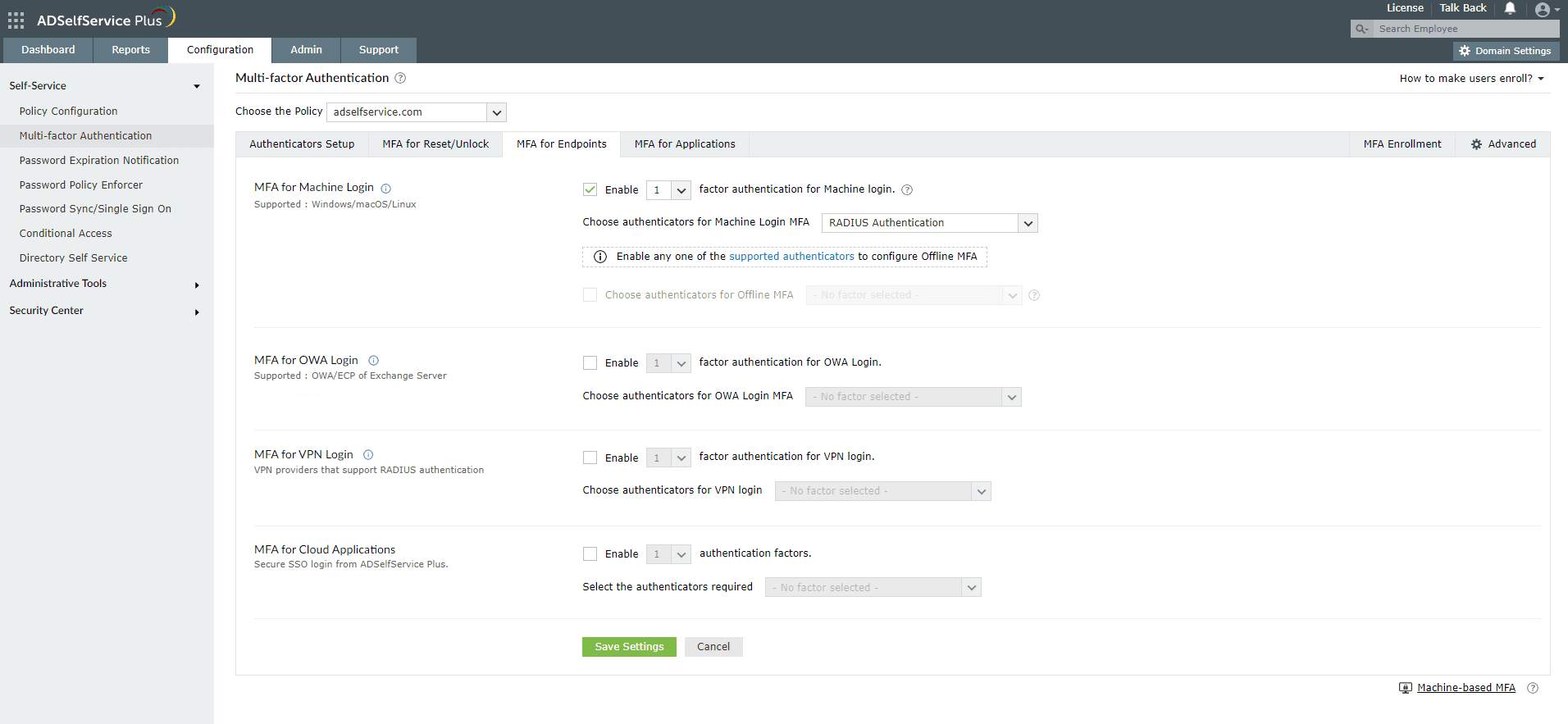
- Go to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for which sets of users.
- In the MFA for Machine Login section, check the box to enable MFA for Machine Login and select the number of authentication factors to be prompted. Select the YubiKey Authentication and other required authenticators from the drop-down.
- Click Save Settings.
New to ADSelfService Plus?
Related Articles
Configuring fingerprint authentication for Active Directory password resets and logins
Fingerprint authentication is an identity verification method that is widely used in recent times. The fact that everyone has a unique fingerprint makes it one of the more secure methods of authentication. Fingerprint authentication is also simple ...Configuring Google Authenticator for Active Directory password resets and logins
Google Authenticator is an authentication method developed by Google that uses a time-based one-time-passcode (TOTP) in order to verify users' identities. It is often used as one of the multi-factor authentication (MFA) methods along with others in ...Configuring TOTP authentication for Active Directory-based actions
Time-based one-time-password or TOTP is one of the most common methods used in multi-factor authentication (MFA). With this method, users are required to enter a passcode within a specific time from its generation. When users prove their identity in ...Configuring Duo Security for Active Directory password reset
Duo Security is an access security focused application that is primarily used for multi-factor authentication. One of the ways Duo Security can be used to verify users identities is using passcodes. Here, once the user has provided their username and ...Configuring QR code-based authentication for Active Directory-based actions
QR code-based authentication is a type of multi-factor authentication method that involves scanning a QR code with an app in order to verify one's identity. When authenticating into a service using MFA, users need to provide their account credentials ...