Configuring Duo Security for Active Directory password reset
Duo Security is an access security focused application that is primarily used for multi-factor authentication. One of the ways Duo Security can be used to verify users identities is using passcodes. Here, once the user has provided their username and password successfully, they have to authenticate themselves with Duo Security in one of three ways:
- By entering the passcode they receive via a push notification in the Duo Mobile app,
- By entering the passcode they receive through SMS,
- By answering a phone call received from Duo Security and following the instructions provided.
When an organization implements solutions for self-service actions like Active Directory password reset and account unlock, it intends to increase the users' productivity by allowing them to reset their own password without having to depend on the help-desk. It also aims at reducing the help-desk's workload by exempting them from the huge number of password reset and account unlock tickets that would have been raised otherwise.
While improved user productivity and reduced help-desk workload are results organizations should work towards, security should always be of prime importance. Self-service password resets and account unlocks can turn perilous for user accounts if they aren't completely secure. Implementing MFA with Duo Security and other methods ensures a user's identity is verified before they engage in resetting their password or unlocking their account.
ADSelfService Plus, an Active Directory self-service password management and single sign-on solution, offers self-service password reset along with multi-factor authentication (MFA) along with other features like self-service account unlock, enterprise single sign-on and password synchronization, password and account expiration notifications, and directory self-update
Aside from self-service password reset and account unlock ADSelfService Plus's MFA feature can also be used to secure:
- Windows, macOS, and Linux logins.
- Enterprise application logins through single sign-on (SSO).
- Self-update of Active Directory profile information, subscription to mail groups, and employee search using ADSelfService Plus.
The solution supports over 17 MFA methods including Duo Security, Google Authenticator, fingerprint authentication, RSA SecurID, and YubiKey Authenticator. Learn more about ADSelfService Plus and its Multi-factor Authentication feature.
Instructions to configure Duo Security for MFA in ADSelfService Plus
Prerequisites
- Add the API hostname and admin console (for example, https://********.duosecurity.com) as a trusted site or intranet site in the users' machine if they are using older versions of Internet Explorer.
- Please follow these steps in the Duo Admin Panel to migrate from Web v2 SDK, which uses the traditional prompt, to Web v4 SDK, which employs the new Universal Prompt.
Web v4 SDK configuration steps

- Log into your Duo Security account (for example, https://********.duosecurity.com) or sign up for a new account and log in.
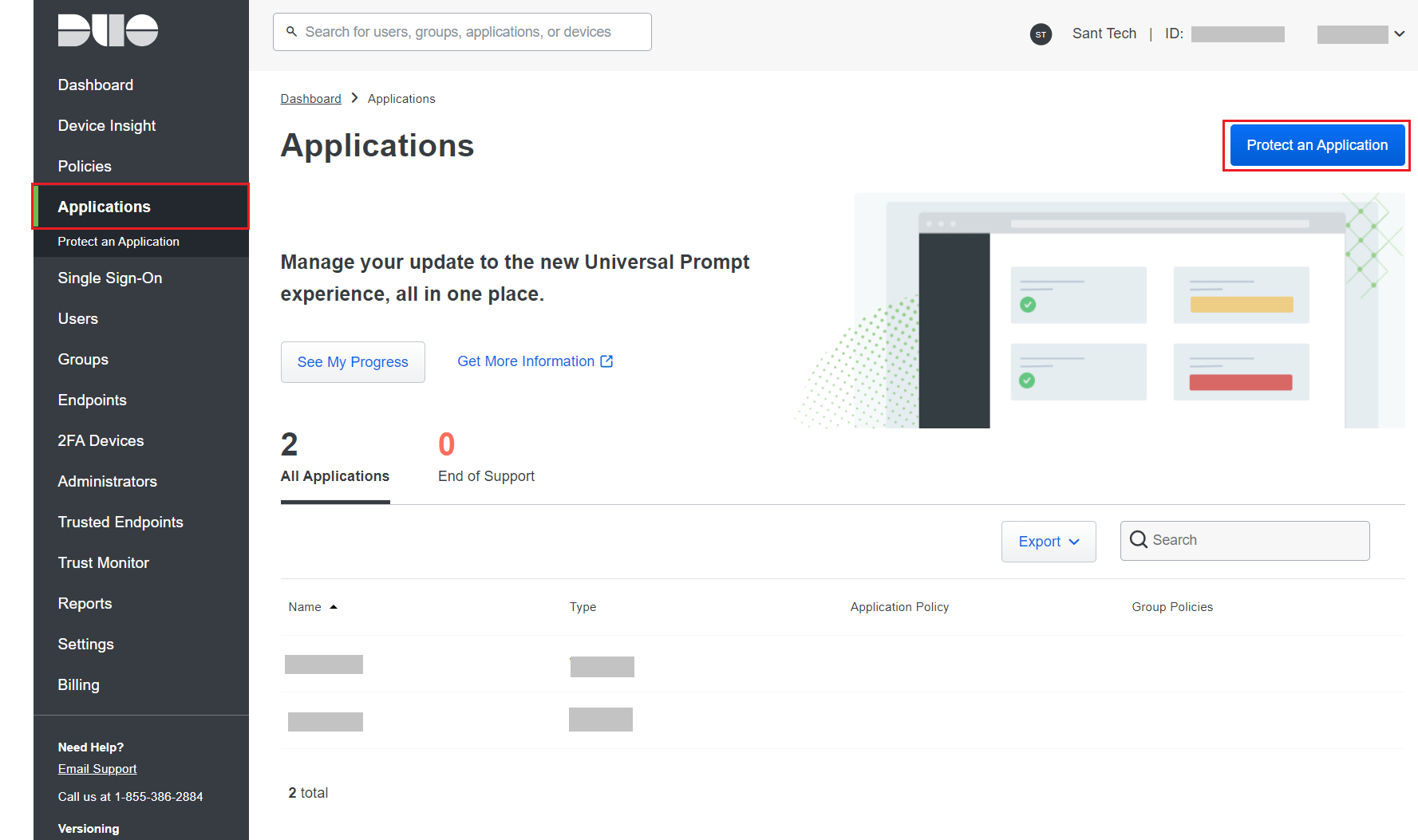
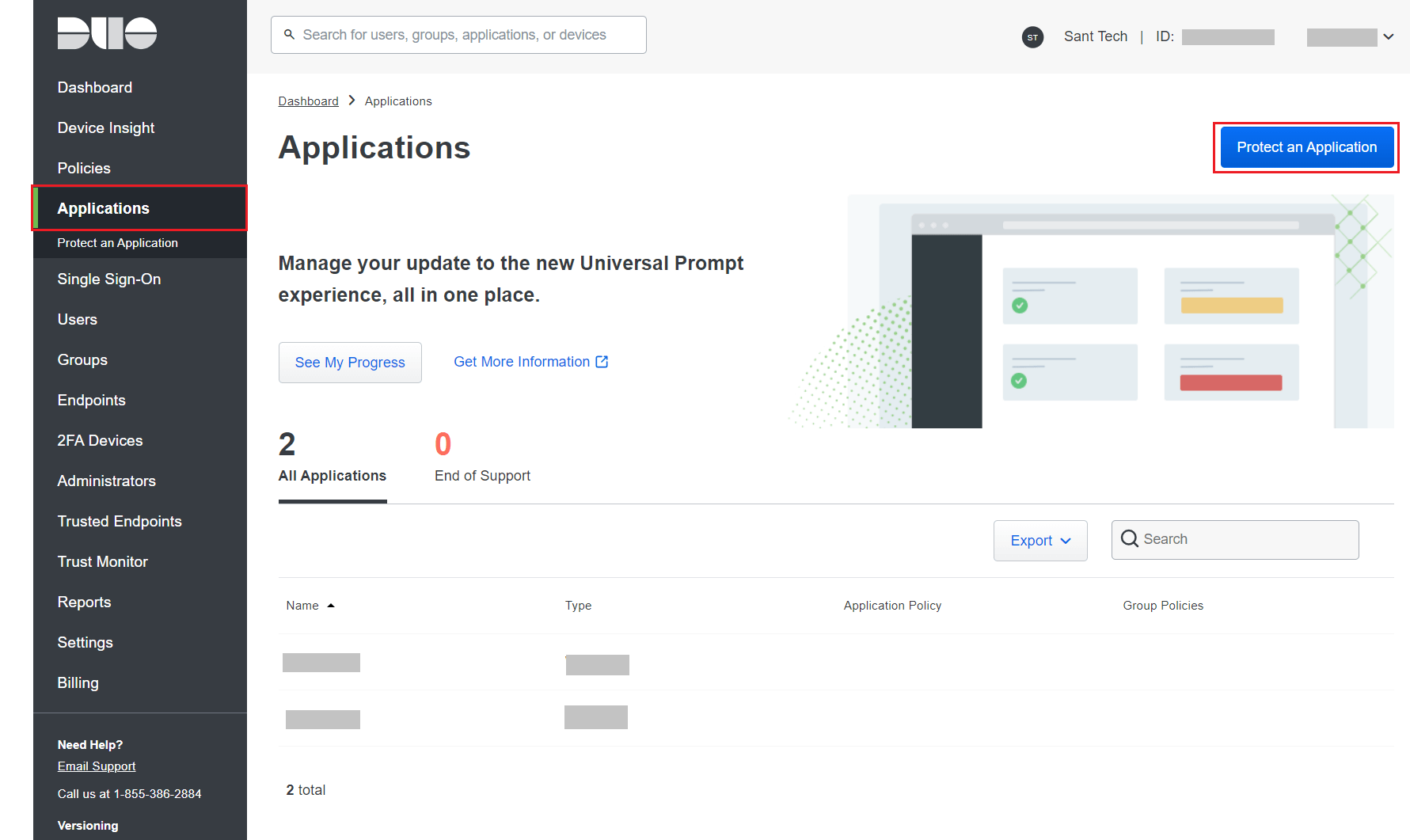
- Go to Applications and click Protect an Application.
- Search for Web SDK and click Protect.
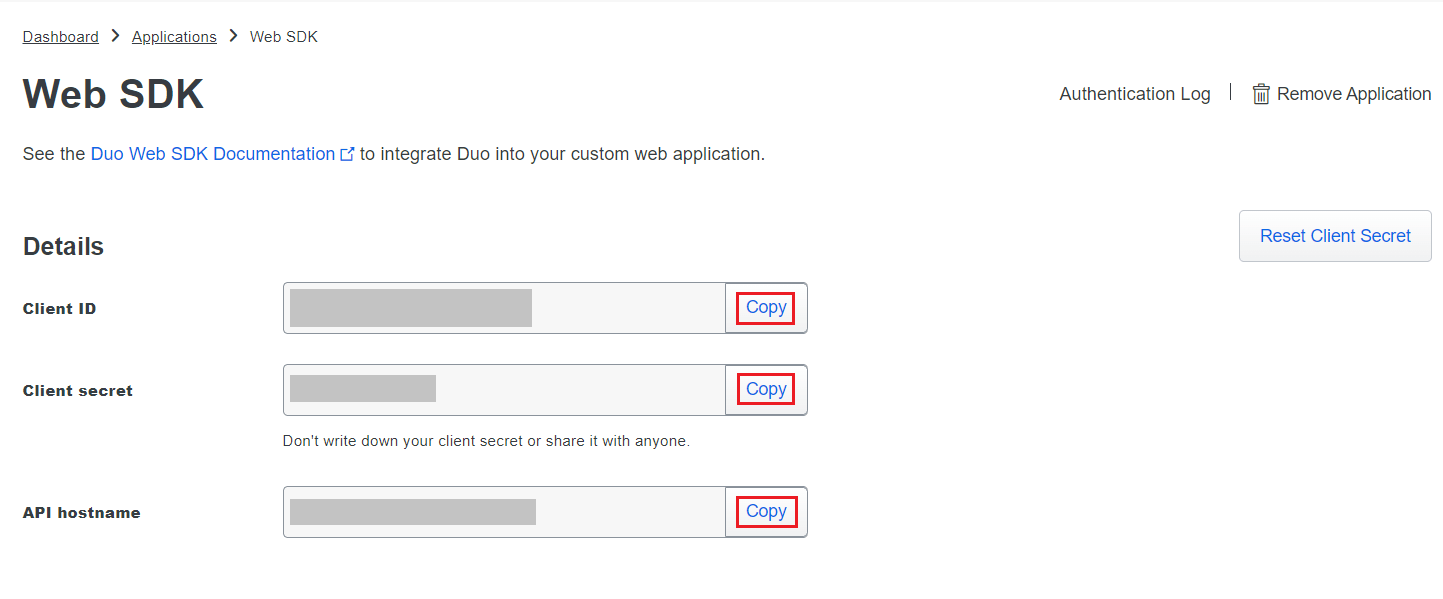
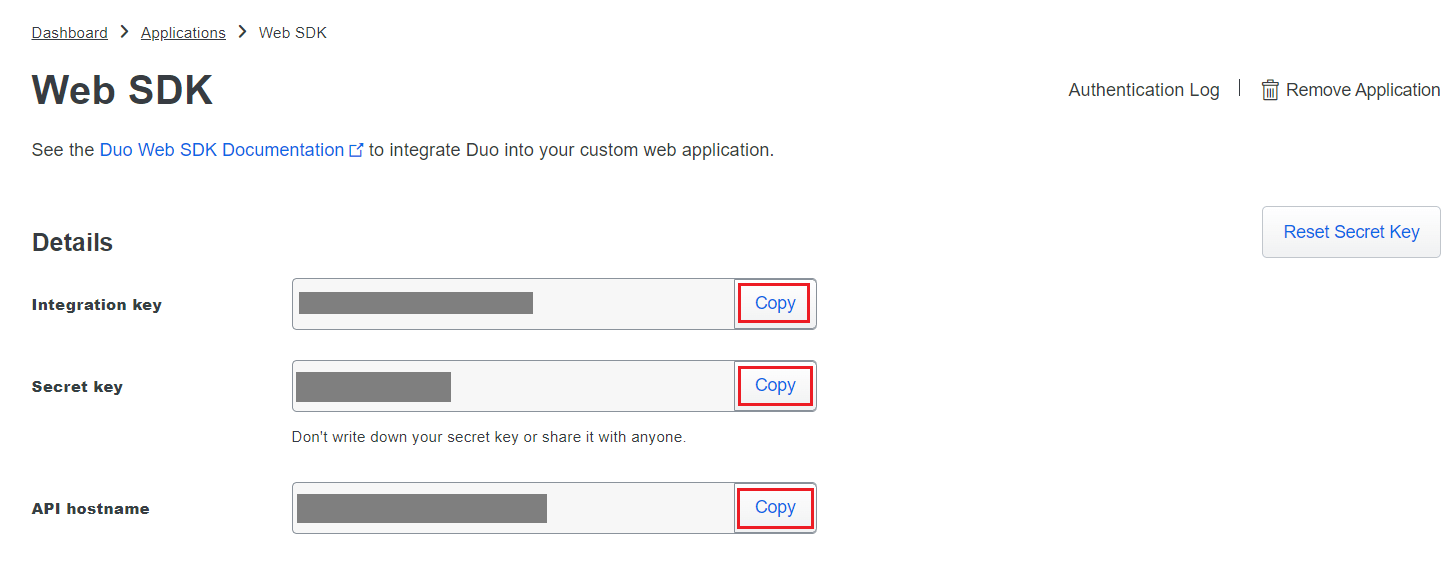
- Copy the Client ID, Client secret, and API hostname values.
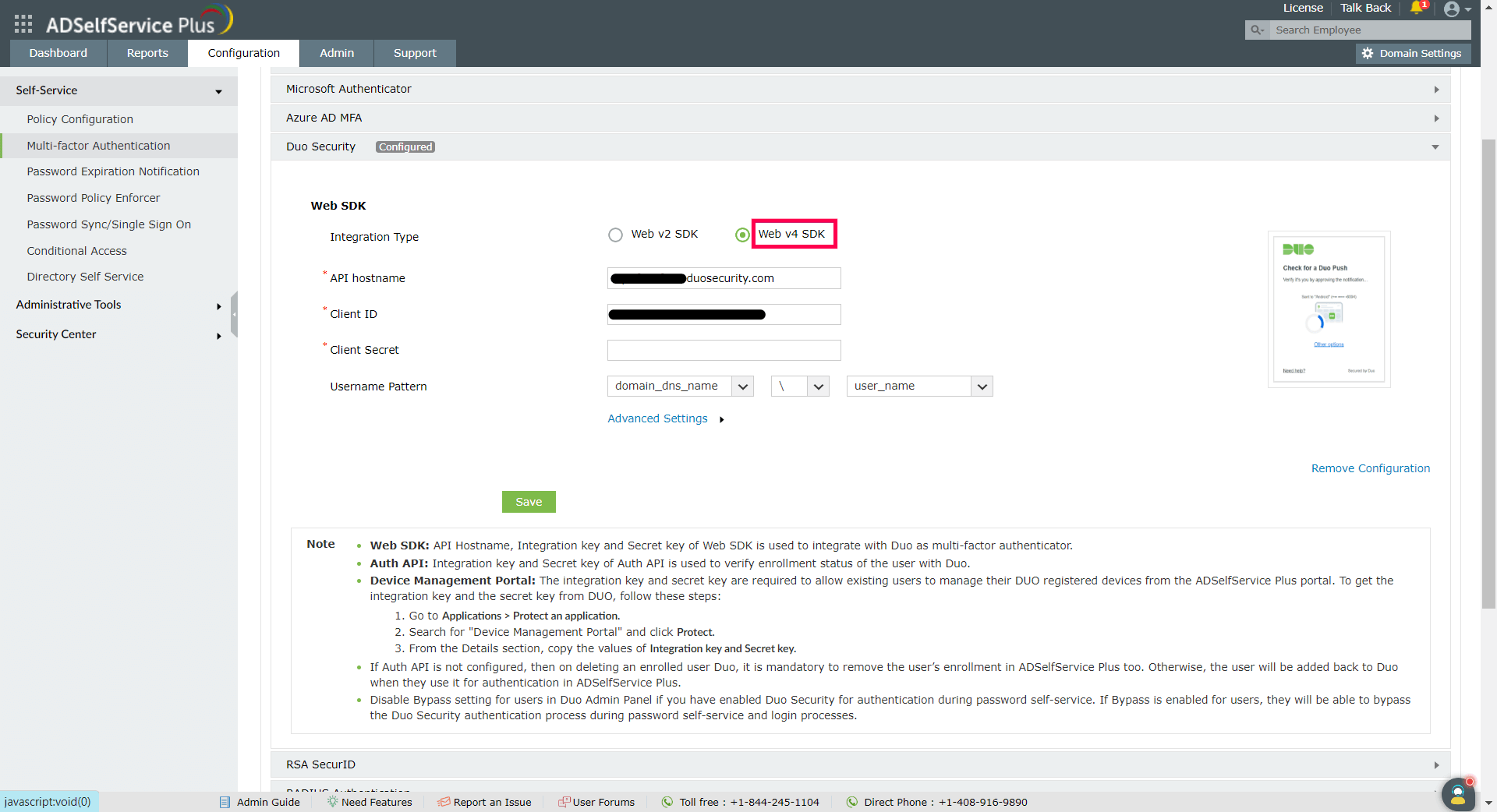
- From the ADSelfService Plus admin portal, navigate to Configuration > Multi-factor Authentication > Duo Security.
- Select Web v4 SDK for Integration Type.
- Paste the Client ID, Client secret, and API hostname obtained from the Duo Admin Panel in the respective fields.
- Enter the same username pattern used in Duo Security in the Username Pattern field.
- Click Save.

Configuring Auth API for Web v4 configurations of Duo Security
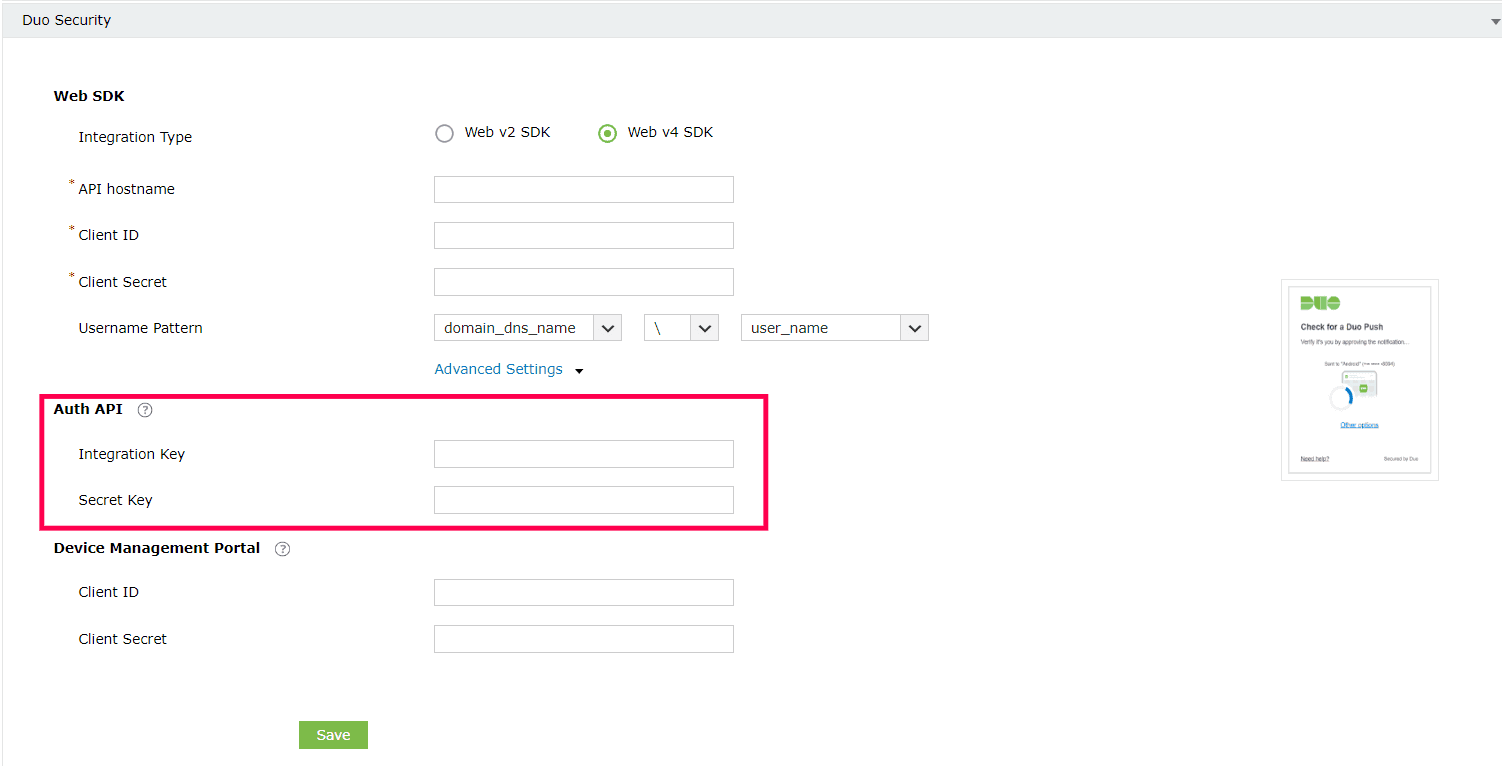
- If configuring Auth API, follow these steps and obtain the Integration Key and Secret Key from the Duo Security portal.
- Under the Web v4 SDK configuration settings for Duo Security, click Advanced Settings to open up the Auth API configuration settings.
- Paste the Integration Key and Secret Key into the relevant fields, and click Save.
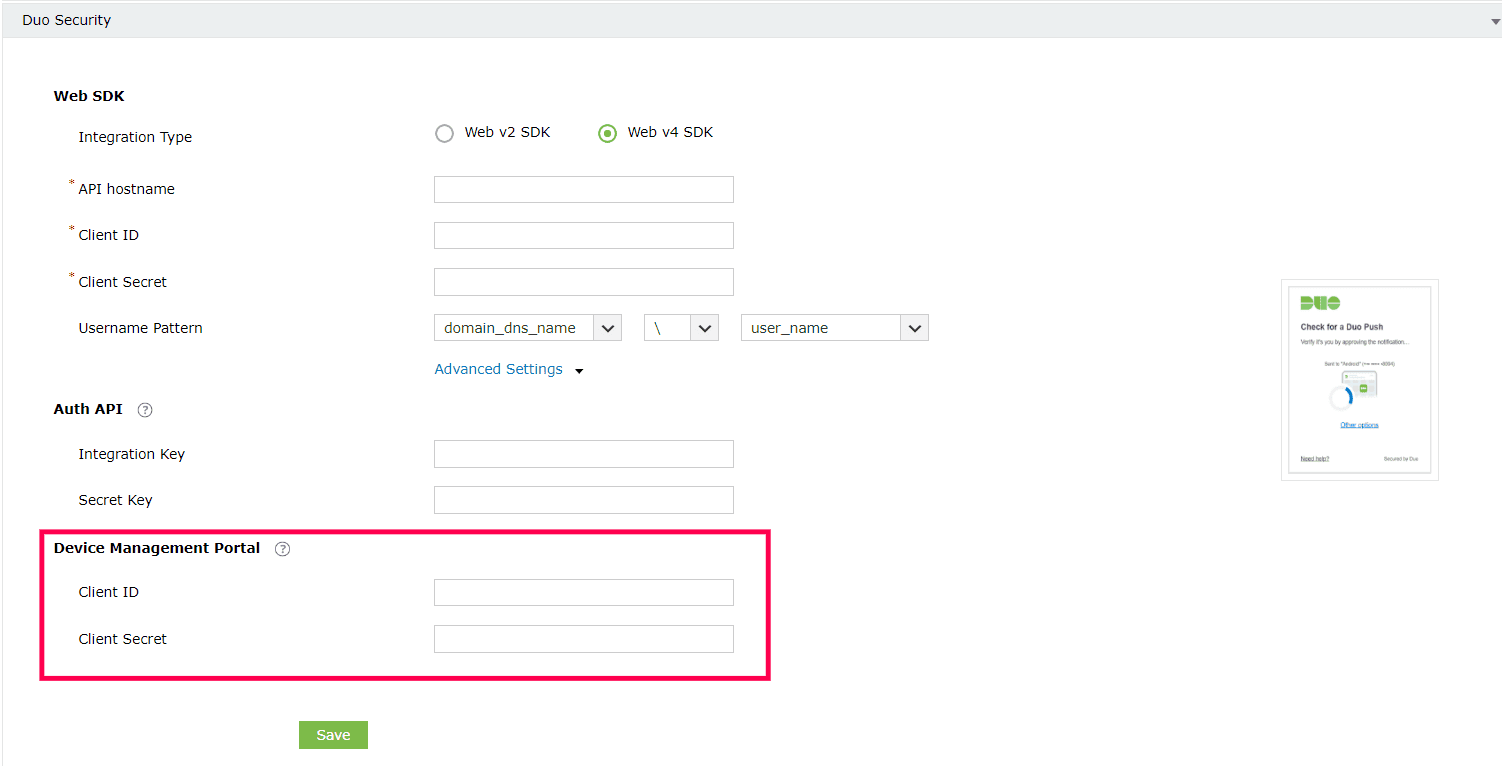
Configuring Device Management Portal settings for WebV4 configurations of Duo Security
The Duo Device Management Portal enables users to add or remove Duo-registered devices from the self-service portal. The Device Management Portal for Web v4 uses Duo's OIDC-based universal prompt with a redesigned UI that redirects users to Duo on a new tab. Here are the steps to configure the Duo Device Management portal:
- Log into Duo Security and go to Applications > Protect an Application.
- Search for Device Management Portal. Click Protect.
- Copy the Client ID and Client Secret from the Details section.
- Under the Web v4 SDK configuration settings for Duo Security, Click Advanced Settings to open the Device Management Portal settings.
- Paste the Client ID and Client Secret into the relevant fields and click Save.
Web v2 SDK configuration steps
- Log in to your Duo Security account (for example, https://********.duosecurity.com) or sign up for a new account and log in.
- Go to Applications and click Protect an Application.
- Search for Web SDK and click Protect.
- Copy the Integration key, Secret key, and API hostname values.
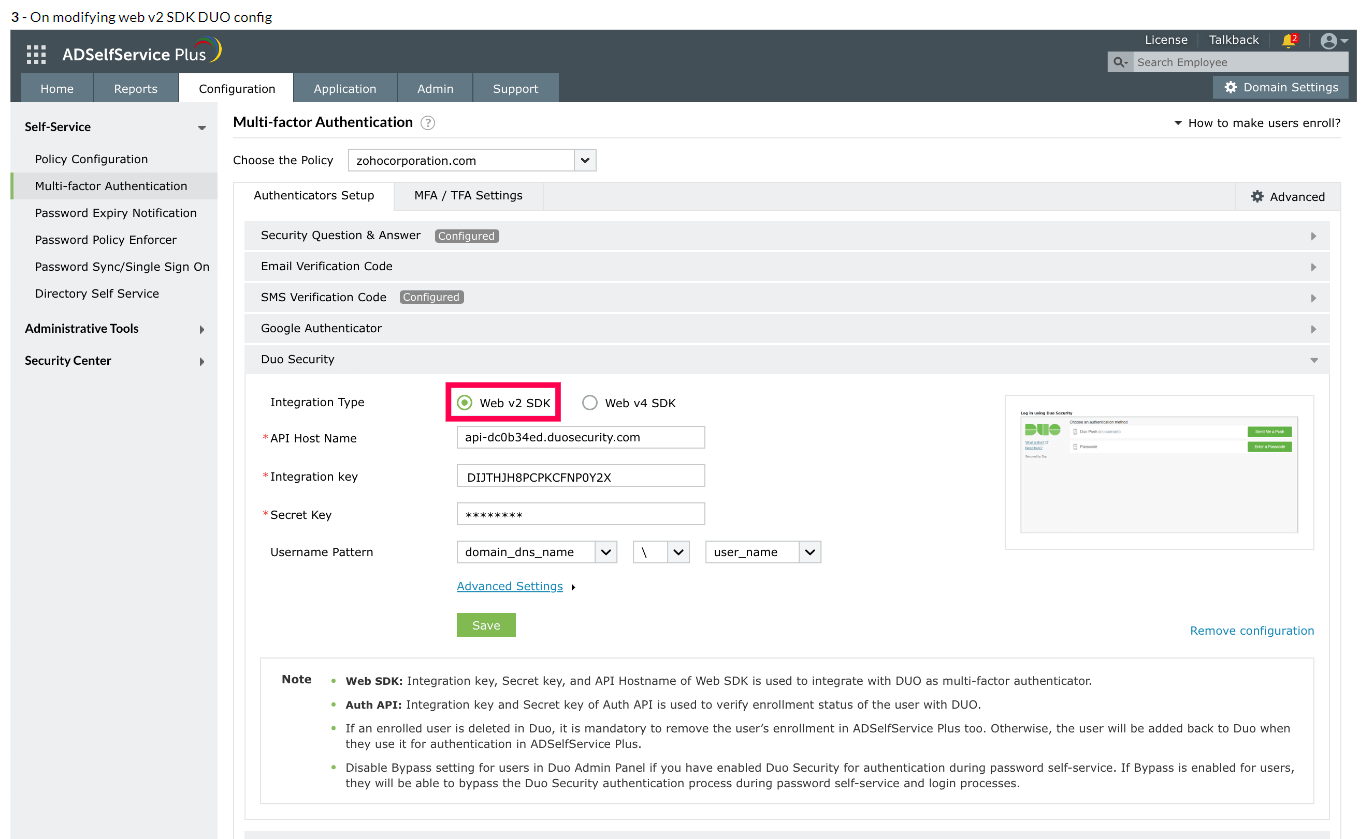
- In ADSelfService Plus, navigate to Configuration > Multi-factor Authentication > Duo Security.
- Select Web v2 SDK for Integration Type.
- Paste the Integration key, Secret key, and API hostname obtained from the Duo Admin Panel in the respective fields.
- Enter the same username pattern used in Duo Security in the Username Pattern field.
- Click Save.

Configuring Auth API for Web v2 configurations of Duo Security
- If configuring Auth API, follow these steps and obtain the Integration Key and Secret Key from the Duo Security portal.
- Under the Web v2 SDK configuration settings for Duo Security, click Advanced Settings to open the Auth API configuration settings.
- Paste the Integration Key and Secret Key into the relevant fields and click Save.
Configuring Device Management Portal settings for WebV2 configurations of Duo Security
The Device Management Portal for Web v2 uses a traditional Duo prompt which will be displayed in an iframe in ADSelfService Plus.
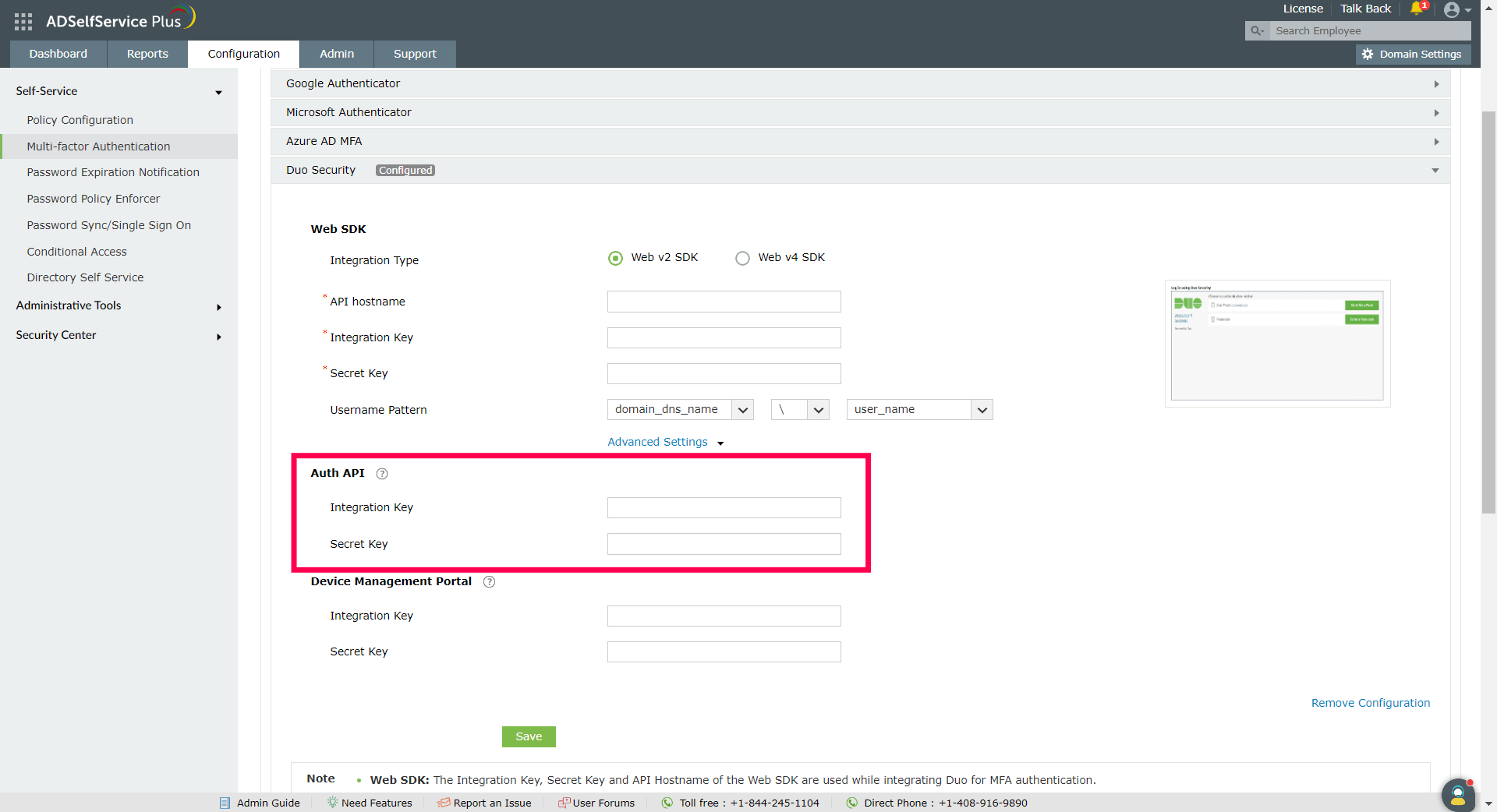
- Log into Duo Security and go to Applications > Protect an Application.
- Search for Device Management Portal. Click Protect.
- Copy the Integration key and Secret key from the Details section.
- Under the Web v2 SDK configuration settings for Duo Security, click Advanced Settings to open the Device Management Portal settings.
- Paste the Integration Key and Secret Key into the relevant fields and click Save.
Configuring Auth API in Duo Security
Configuring the Auth API in Duo Security is optional. Auth API configuration is used to verify the user's enrollment with Duo Security. If Auth API is not configured, then on deleting a user's enrollment in Duo Security, it is mandatory to manually remove the user's enrollment in ADSelfService Plus too. If not, the user will be added back to Duo Security when it is used for authentication in ADSelfService Plus.
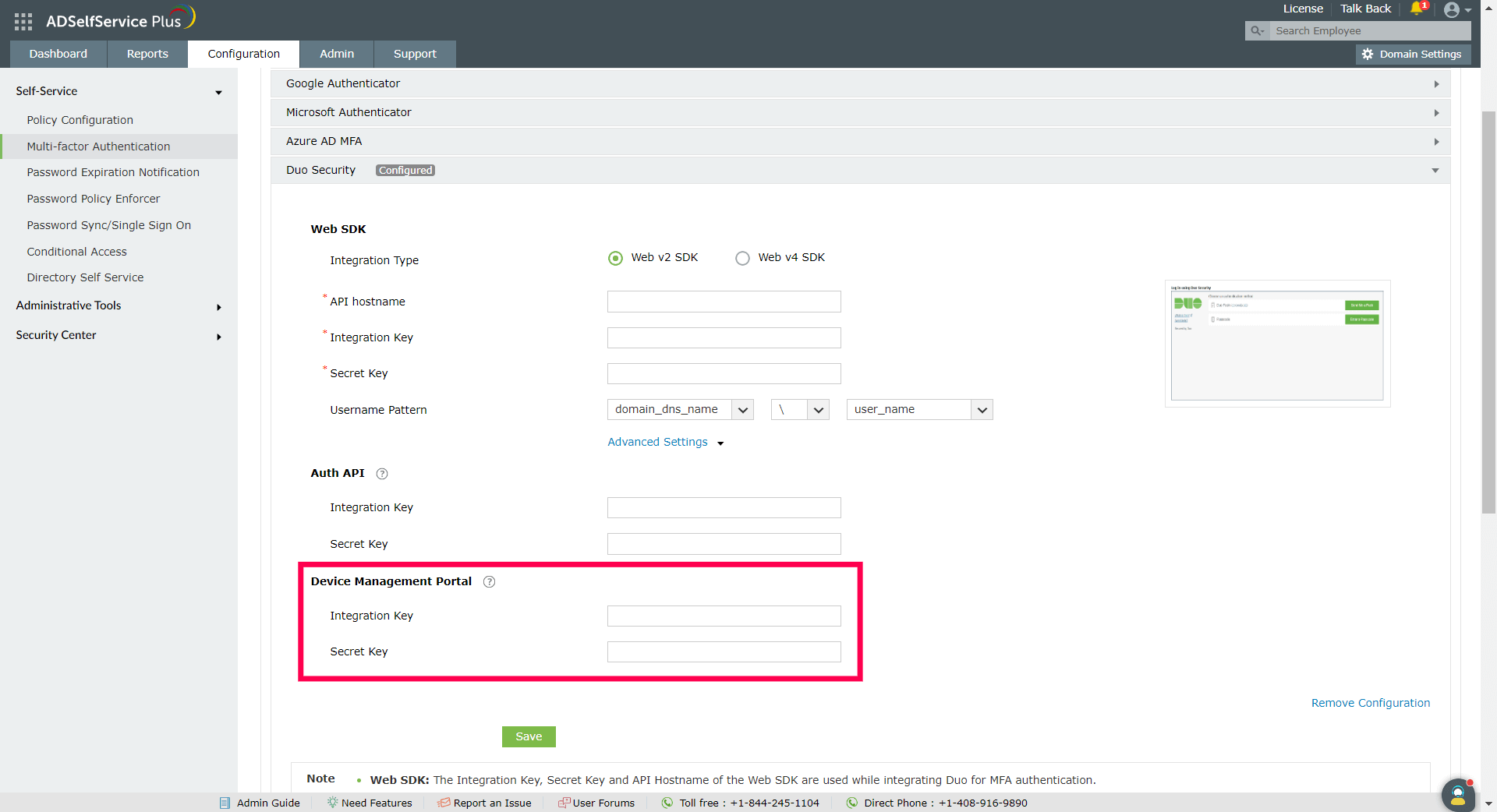
- Login to the Duo Security portal.
- Navigate to Applications and click Protect An Application.
- Search for Auth API. Click Protect this Application.
- Copy the Integration key and Secret key.
Steps to migrate to the new Universal Prompt
- In the Duo Admin Panel, select the Web SDK application, which was previously configured for ADSelfService Plus, and copy the Integration key, Secret key and API hostname values.
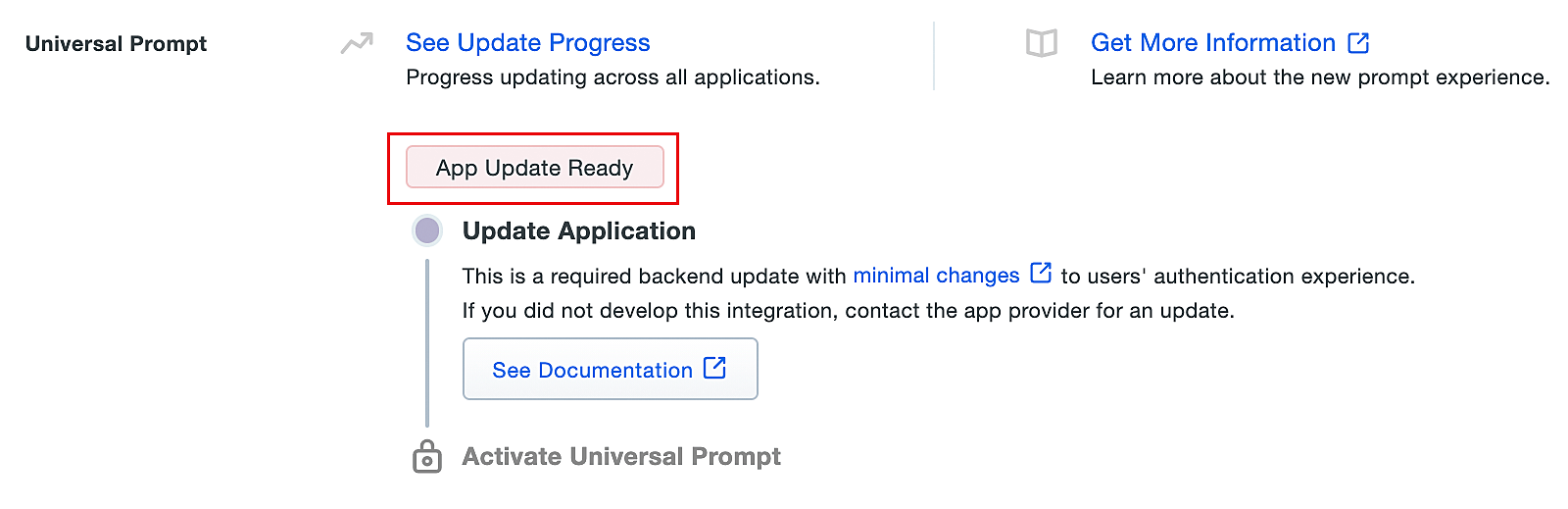
- Scroll down to the Universal Prompt section. The App Update Ready message will be displayed, indicating that Universal Prompt can now be activated for ADSelfService Plus.
- In ADSelfService Plus, navigate to Configuration > Multi-factor Authentication > Duo Security.
- Click Web v4 SDK and paste the Integration key, Secret key, and API hostname values in the Client ID, Client Secret, and API Host name fields respectively.
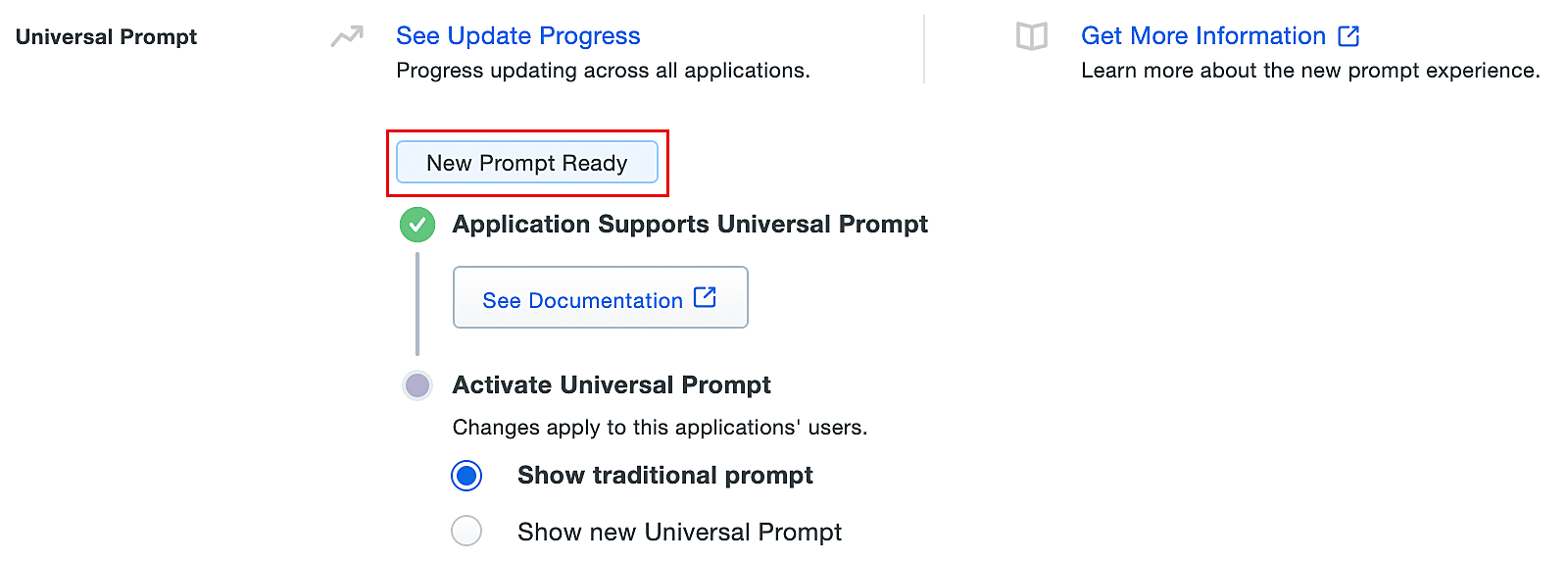
- Once the Web v4 SDK is configured in ADSelfService Plus and a user authenticates through the frameless Duo v4 SDK, the App Update Ready message in Duo Admin Panel will be updated and the New Prompt Ready message will be displayed.
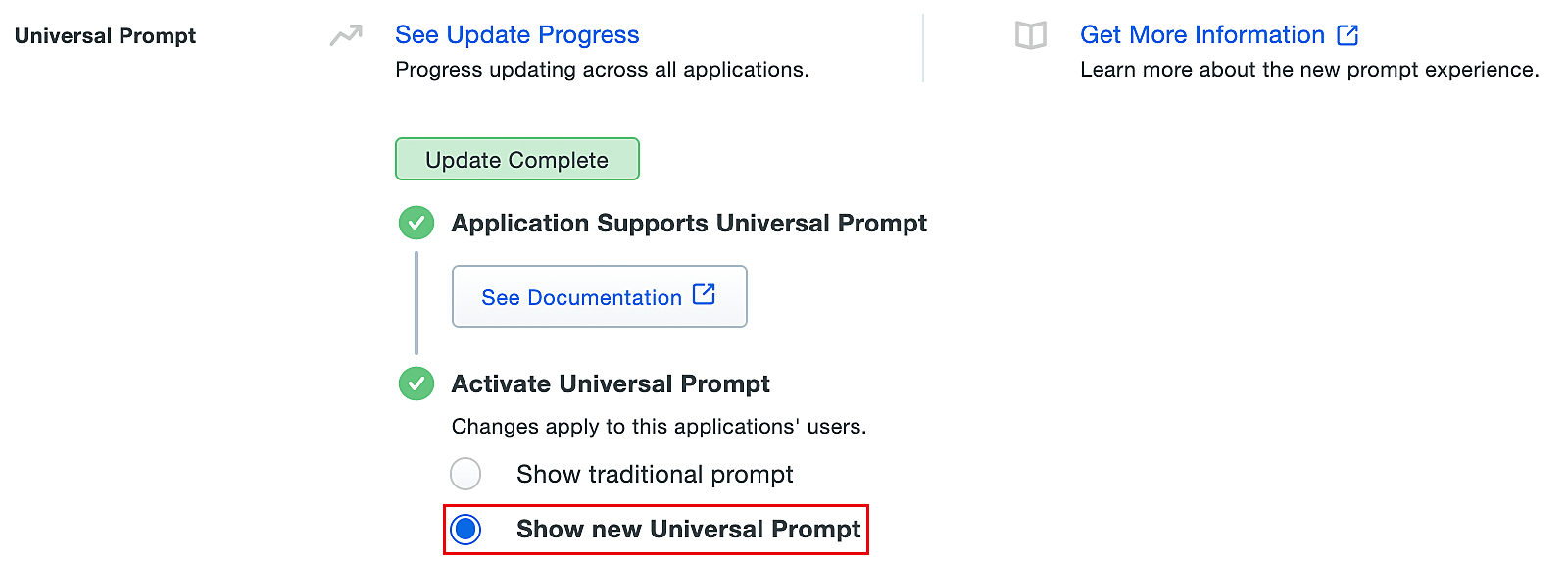
- Select Show new Universal Prompt to activate the universal prompt for ADSelfService Plus.
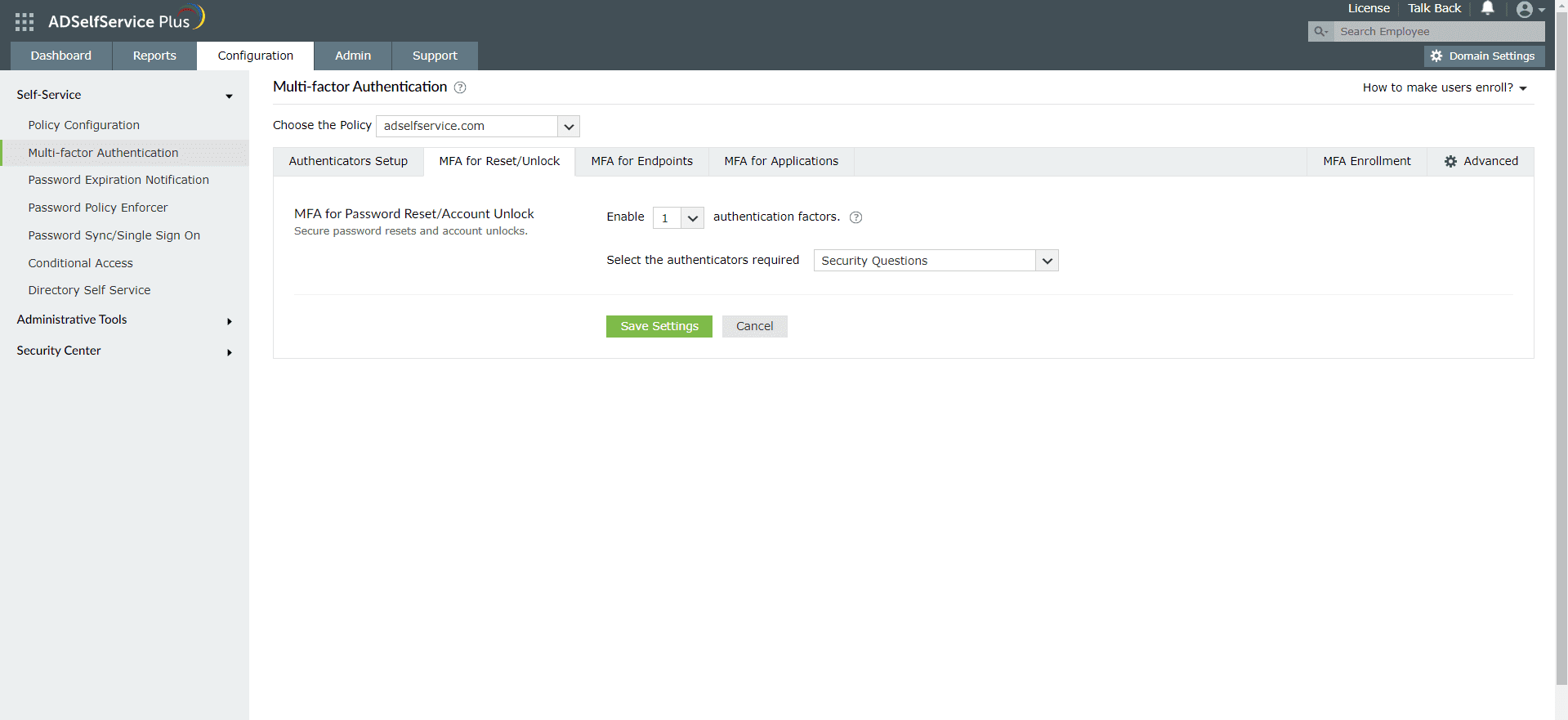
Enable Duo Security for Active Directory password resets
- Go to Configuration → Self-Service → Multi-factor Authentication → MFA/TFA Settings. In the MFA for Reset/Unlock section, enter the number of authentication factors to be enforced, and select Duo Security along with the other authentication techniques
to be used.
- Click Save Settings.
Enable Duo Security for Active Directory domain logins
To enable MFA for Active Directory domain logins:
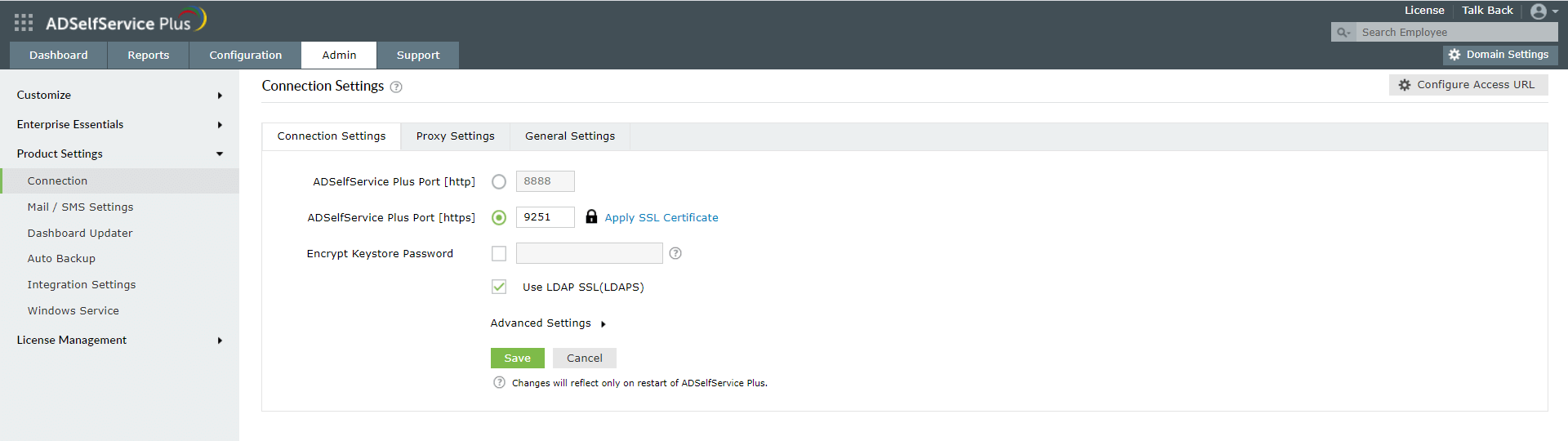
- The ADSelfService Plus login agent must be installed on client machines. Click here for steps on login agent installation.
- SSL must be enabled: Log in to the ADSelfService Plus web console with admin credentials. Navigate to the Admin tab > Product Settings > Connection. Select the ADSelfService Plus Port [https] option.
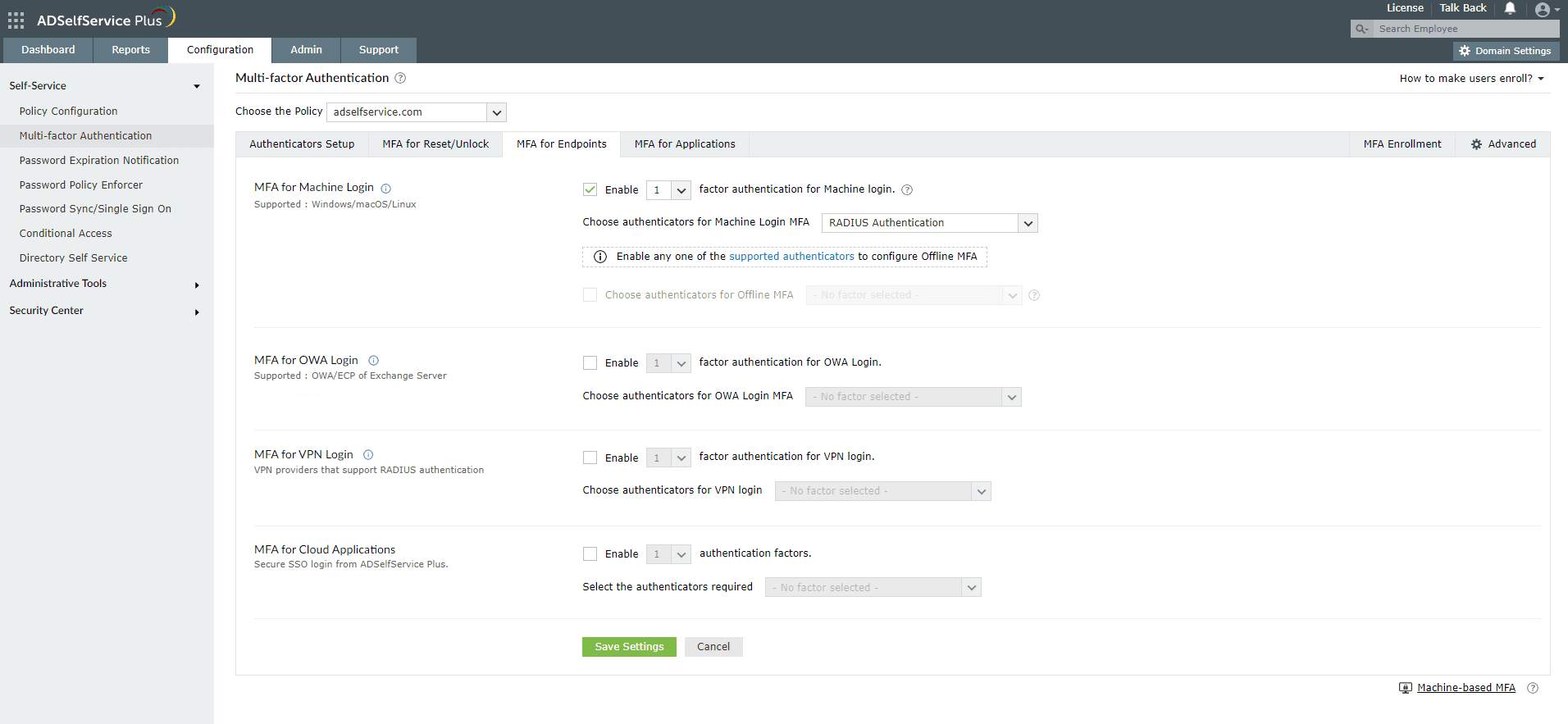
- Go to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for which sets of users.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration > Self-Service > Policy Configuration > Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy. - In the MFA for Machine Login section, check the Enable _ authentication factors box and select the authentication methods from the drop-down.
- Click Save Settings.
New to ADSelfService Plus?
Related Articles
How to set up MFA for macOS
When employees are required to manage multiple passwords, they often resort to reusing the same password across various applications or creating simple, easy-to-remember passwords that lack sufficient strength. This behavior significantly increases ...Whitelisting the DUO credential provider for proper functioning of the ADSelfService Plus' self-service password reset feature
If you are using Duo Security's credential provider for MFA during machine logins, and want to use ADSelfService Plus' self-service password reset and account unlock feature from login screens, merely configuring the self-service password feature and ...Configuring the ADSelfService Plus login agent for machine MFA and password self-service in Linux
Securing data and resources on the corporate network is of paramount importance to organizations. In a world where most corporate attacks originate at an endpoint, ADSelfService Plus offers 20 MFA factors to protect endpoints by allowing access only ...ADSelfService Plus self-service password reset configuration: Reset & Unlock tab
Reset & Unlock tab The Reset & Unlock tab consists of settings related to the self-password reset and account unlock features. Learn how to configure these settings to suit your requirements. Here are the settings under the Reset & Unlock tab: Unlock ...Self-service password reset for Windows 7, 8, and 10
We've all had to reset a forgotten password at some point in our lives. But have you ever wondered what goes on behind the scenes when you initiate a password reset? Have you considered the security risks that can arise due to poor password ...