Configuring TOTP authentication for Active Directory-based actions
Time-based one-time-password or TOTP is one of the most common methods used in multi-factor authentication (MFA). With this method, users are required to enter a passcode within a specific time from its generation. When users prove their identity in a service with TFA or MFA using TOTP, they first have to provide their accounts' username and password. If the credentials provided are valid, a TOTP is generated specifically for that session in the authentication app. Users have to enter this TOTP in the field provided within the given time.
Users in any organization tend to enter passwords during Active Directory domain logins and enterprise application logins frequently. The main purpose of these passwords is to prohibit attackers from obtaining access to sensitive data. However, many users are not adequately vigilant regarding online security. Having to maintain multiple passwords leads to users creating simple ones that professionals can crack in a matter of seconds. MFA is a solution to this issue. Instead of using just a password, additional authentications like TOTP can be used. A major advantage of TOTP is that if the password is not entered within the specified time, it expires. Thus, even if attackers lay their hands on the user's Active Directory or enterprise application password, they will not be able to get the TOTP and enter it before it expires. With such advantages, employing TOTP during self-service password resets and account unlocks would be a good move.
ADSelfService Plus, an Active Directory self-service password management and single sign-on solution offers this feature. The solution supports over 15 MFA methods, including TOTP, Google Authenticator, fingerprint authentication, security questions and answers, and YubiKey Authenticator, to validate user identity during:
- Active Directory self-service password reset or account unlock actions via the ADSelfService portal, ADSelfService Plus mobile app, and native Windows/macOS/Linux login screen.
- Windows, macOS, and Linux logins.
- Enterprise application logins through single sign-on (SSO).
- Self-update of Active Directory profile information, subscription to mail groups, and employee search using ADSelfService Plus.
TOTP Authentication for MFA can be enabled with minimal steps in ADSelfService Plus
- Navigate to Configuration → Self-Service → Multi-factor Authentication → Authenticators Setup.
- From the Choose the Policy drop-down, select a policy.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy. - Click TOTP Authentication section.
- Select Enable Time-based One-time Password Authentication.
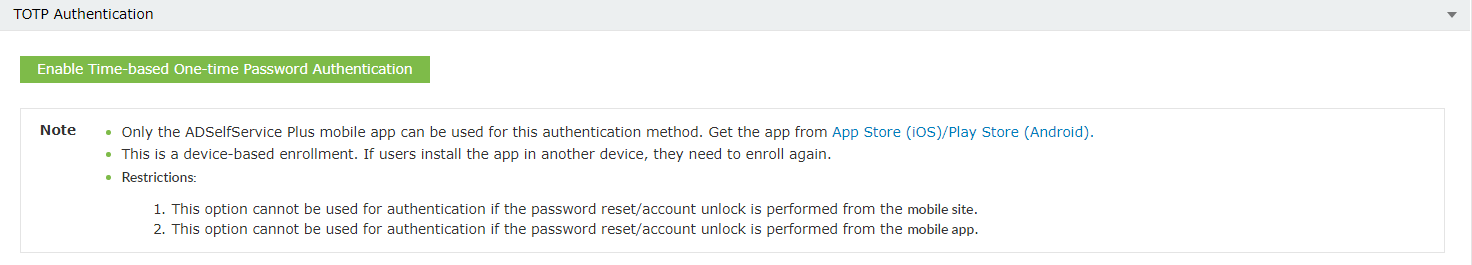
Enable TOTP Authentication for Active Directory password resets
- Go to Configuration > Self-Service > Multi-factor Authentication > MFA for Reset/Unlock. In the MFA for Reset/Unlock section, enter the number of authentication factors to be enforced, and select TOTP Authentication along with the other authentication techniques to be used.
- Click Save Settings.
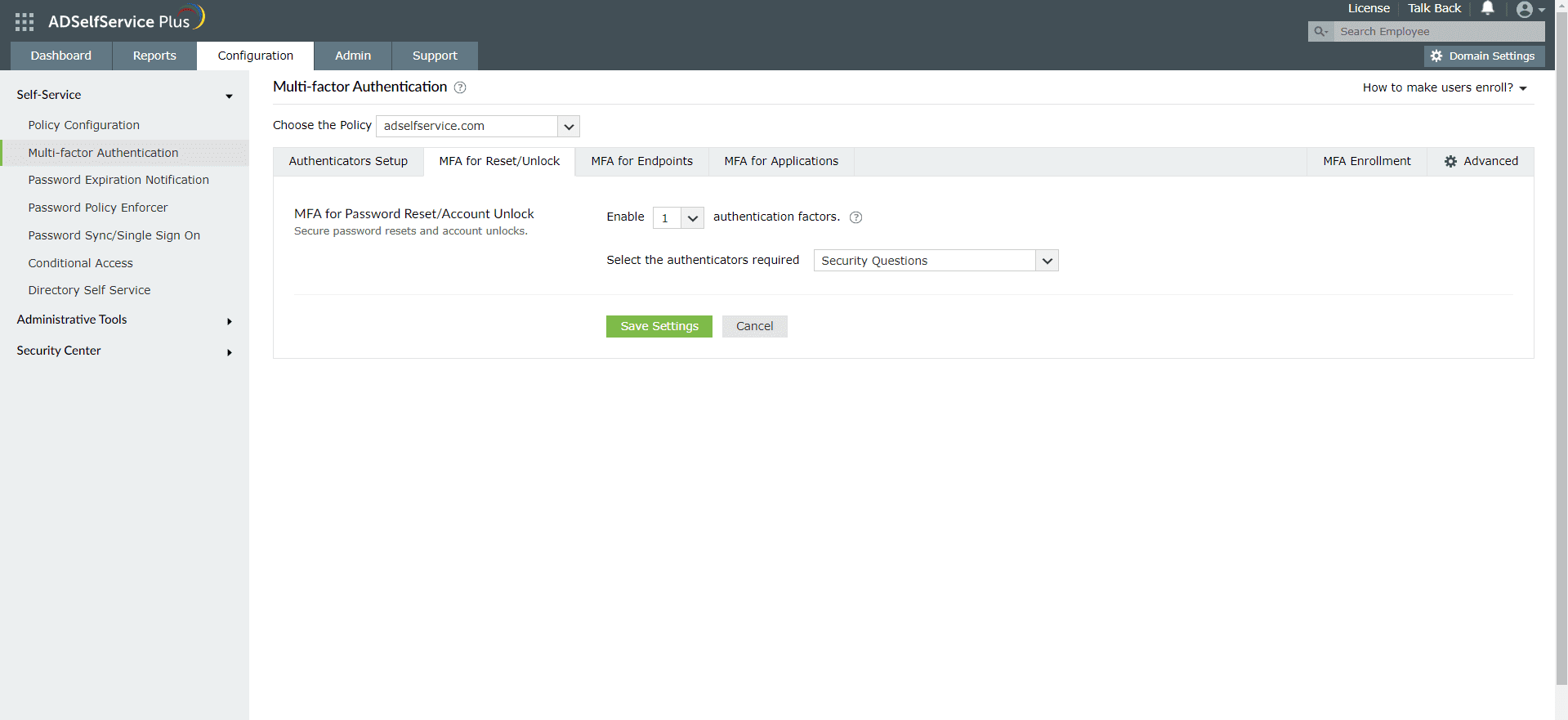
Enable TOTP Authentication for Active Directory domain logins
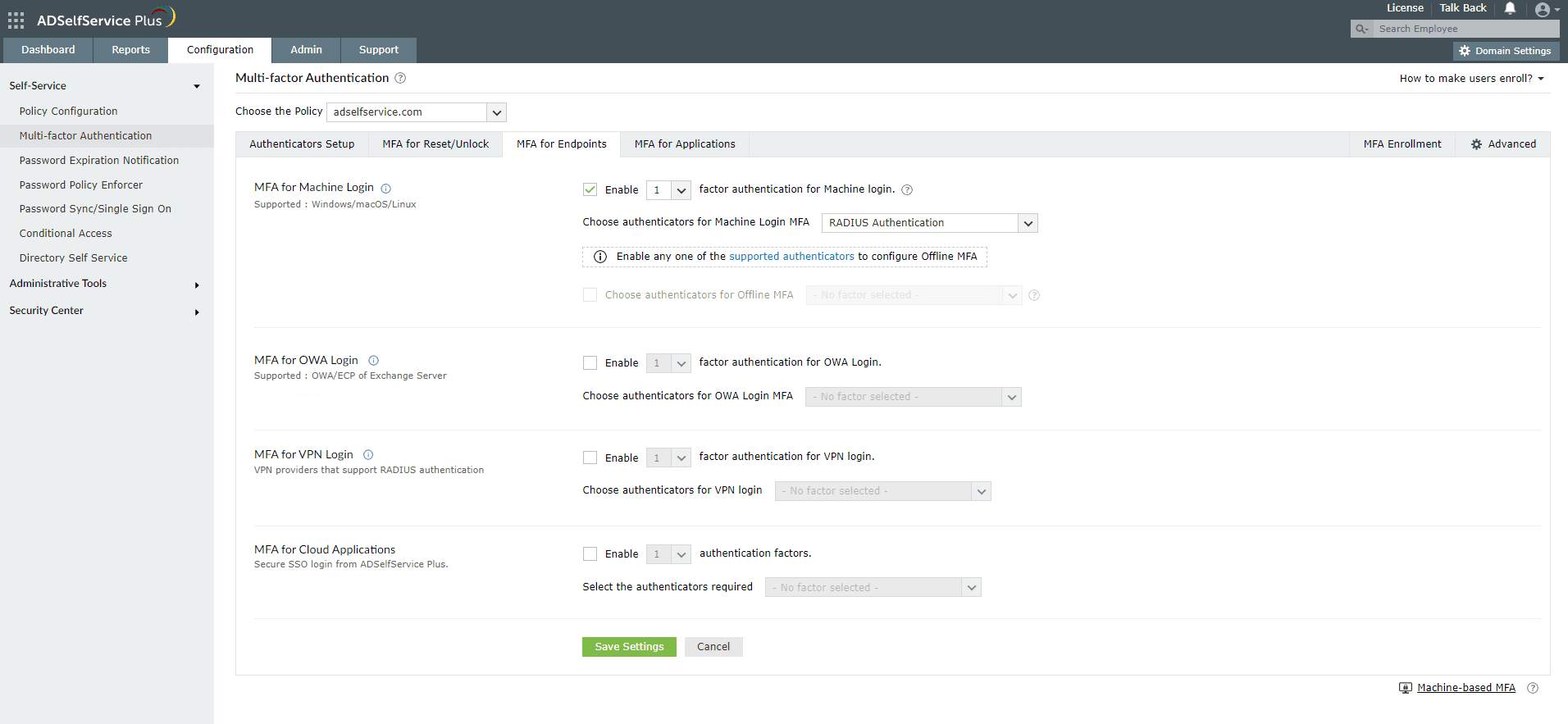
- Go to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for which sets of users.
- In the MFA for Machine Login section, check the box to enable MFA for Machine Login and select the number of authentication factors to be prompted. Select the TOTP Authentication and other required authenticators from the drop-down.
- Click Save Settings.
New to ADSelfService Plus?
Related Articles
Configuring RADIUS authentication for Active Directory-based actions
Traditional logins to resources on an organizational network involve only a username and password. However, if all the data breaches in recent years teach us anything, it is that they are not sufficient. Multi-factor authentication (MFA) has become ...Configuring Microsoft Authenticator for Active Directory-based actions
Microsoft Authenticator is an authentication method developed by Google that uses a time-based one-time-passcode (TOTP) in order to verify users' identities. It is often used as one of the multi-factor authentication (MFA) methods along with others ...Configuring Google Authenticator for Active Directory password resets and logins
Google Authenticator is an authentication method developed by Google that uses a time-based one-time-passcode (TOTP) in order to verify users' identities. It is often used as one of the multi-factor authentication (MFA) methods along with others in ...Configuring QR code-based authentication for Active Directory-based actions
QR code-based authentication is a type of multi-factor authentication method that involves scanning a QR code with an app in order to verify one's identity. When authenticating into a service using MFA, users need to provide their account credentials ...Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...