Analyzing AWS VPCs and VPC Subnets in DDI Central
Analyzing AWS VPCs and VPC Subnets in DDI Central
Table of Contents
Analyzing AWS VPCs in DDI Central
DDI Central enables you to visualize, monitor AWS VPCs and derive actionable insights as part of its Cloud Observability Integration.
With centralized access to key VPC metadata, subnet allocations, EC2 usage, RDS states, load balancers, and more, DDI Central acts as your one-window interface to govern IP identity in hybrid and cloud-native environments.
What are AWS VPCs?
AWS VPC (Virtual Private Cloud) is Amazon's virtual network environment that allows you to launch AWS resources like EC2, RDS, or Lambda inside a logically isolated section of the AWS cloud.
It gives you control over:
- Your private IP address ranges (via CIDR blocks)
- Subnet definitions
- Route tables and internet gateways
- Network security via security groups and ACLs
Here's how to access and analyze AWS VPCs in DDI Central:
- Log into DDI Central using the web UI. Only an Admin or Operator with pertinent access privileges to a cloud cluster can access a Cloud Observability cluster.
- Select an AWS-integrated Cloud Observability Cluster, created during cloud integration setup, from the top right corner within the Web UI.
- Navigate to IPAM->VPC menu inside the selected cluster:
- Click the VPC tab at the top of the page
- This opens a dedicated dashboard for AWS VPC observability
- Choose a RegionUse the dropdown in the top-right corner to:
- Select a specific AWS region (e.g., ap-east-1 for Hong Kong)
- All data displayed in the dashboard — graphs, charts, and tables — will be based on your region selection
- Explore the VPC Dashboard.
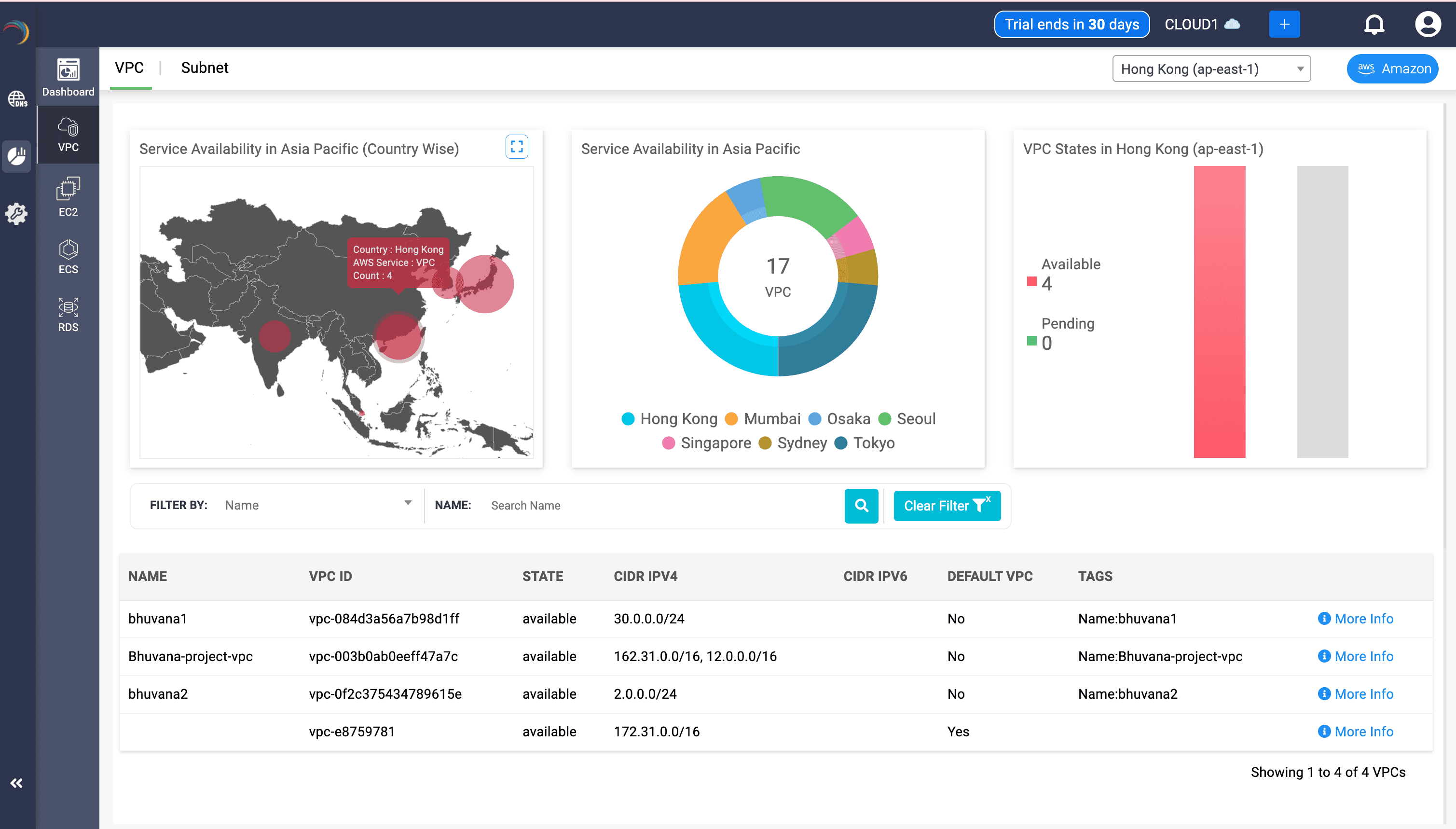
The rich visual dashboard provides a macro-level understanding of where your AWS VPC resources are deployed across AWS's geographical datacenters, enabling strategic resource placement and availability checks.
- Map Panel (Left)
- Visualizes the geographic spread of AWS VPCs with proportional heatmap bubbles. This enables admins to identify regional density and prioritize capacity expansion or redundancy.
- Tooltip highlights:
- Country (e.g., Hong Kong)
- AWS Service: VPC
- Count: Number of active VPCs in that country
- Donut Chart (Center)
- Displays total VPCs (17) grouped by region (e.g., Hong Kong, Mumbai, Sydney). This drives admins to undertake comparative planning across regional data centers.
- Bar Graph (Right)
- Segregates VPCs in Hong Kong into Available and Pending states. It helps admins to monitor provisioning delays or anomalies in real time.
- Table View (Bottom)
- Key Fields:
- VPC Name and ID: Identification of each VPC instance
- State: Indicates whether VPC is ready for use
- CIDR IPv4/IPv6: IP ranges assigned for internal routing
- Default VPC: Yes/No status to indicate AWS auto-created VPCs
- Tags: Descriptive metadata
- The table offers filterable, searchable breakdown for operational tracking.
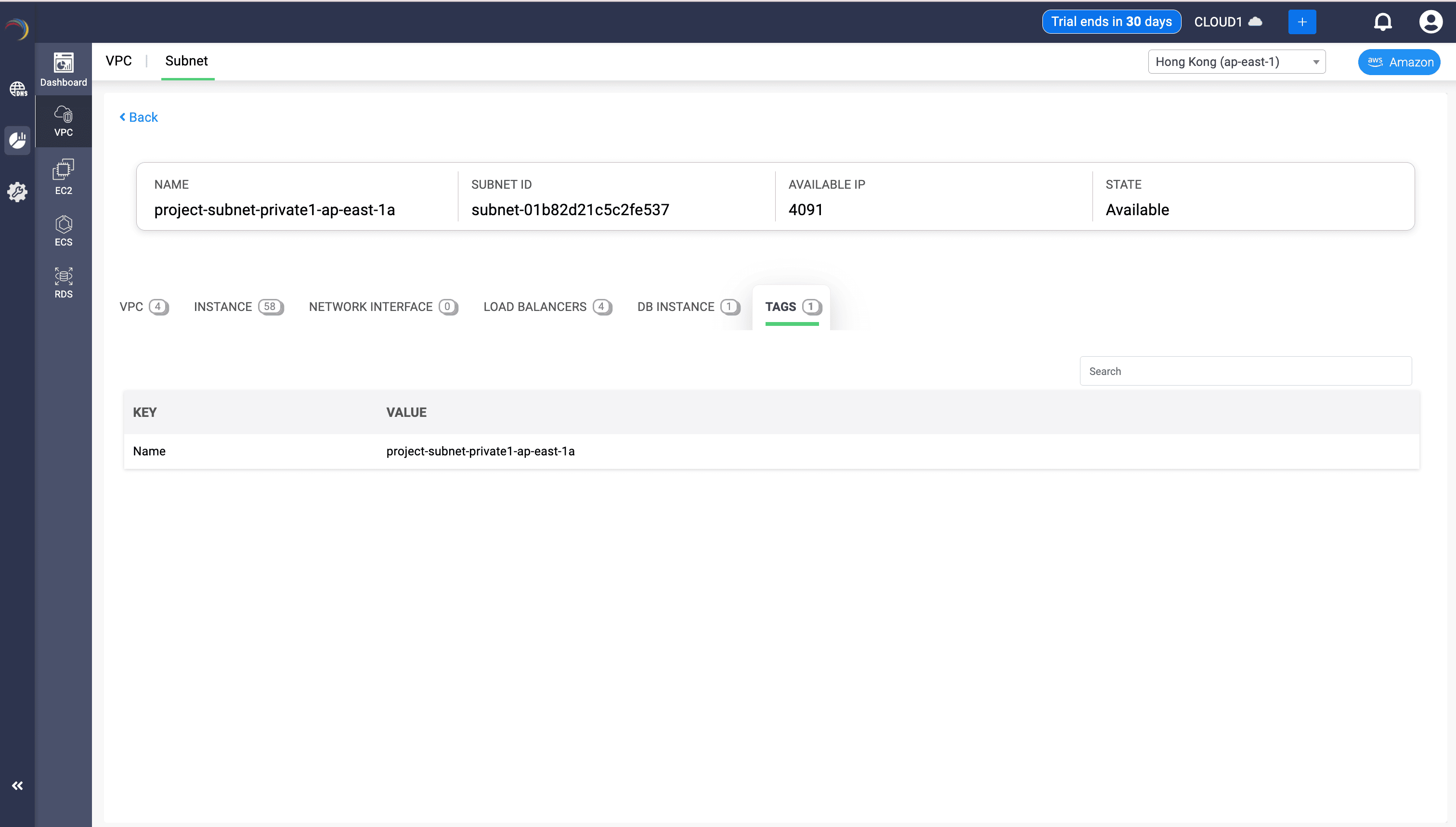
Deep Subnet Insights
To drill more details about the Subnet Utilization in a VPC, click the More details link in the extreme right end. This takes you to a dedicate page within the VPC dashboard. This page in DDI Central gives you micro-level clarity inside your AWS VPCs. Whether you’re troubleshooting DHCP scope exhaustion, planning IPv6 rollout, or reviewing address hygiene, this view acts as your control tower.
Here you can see six tabs below a specific VPC. Navigate to the Subnet tab to gather more details on subnet behavior and resource usage inside a selected VPC.
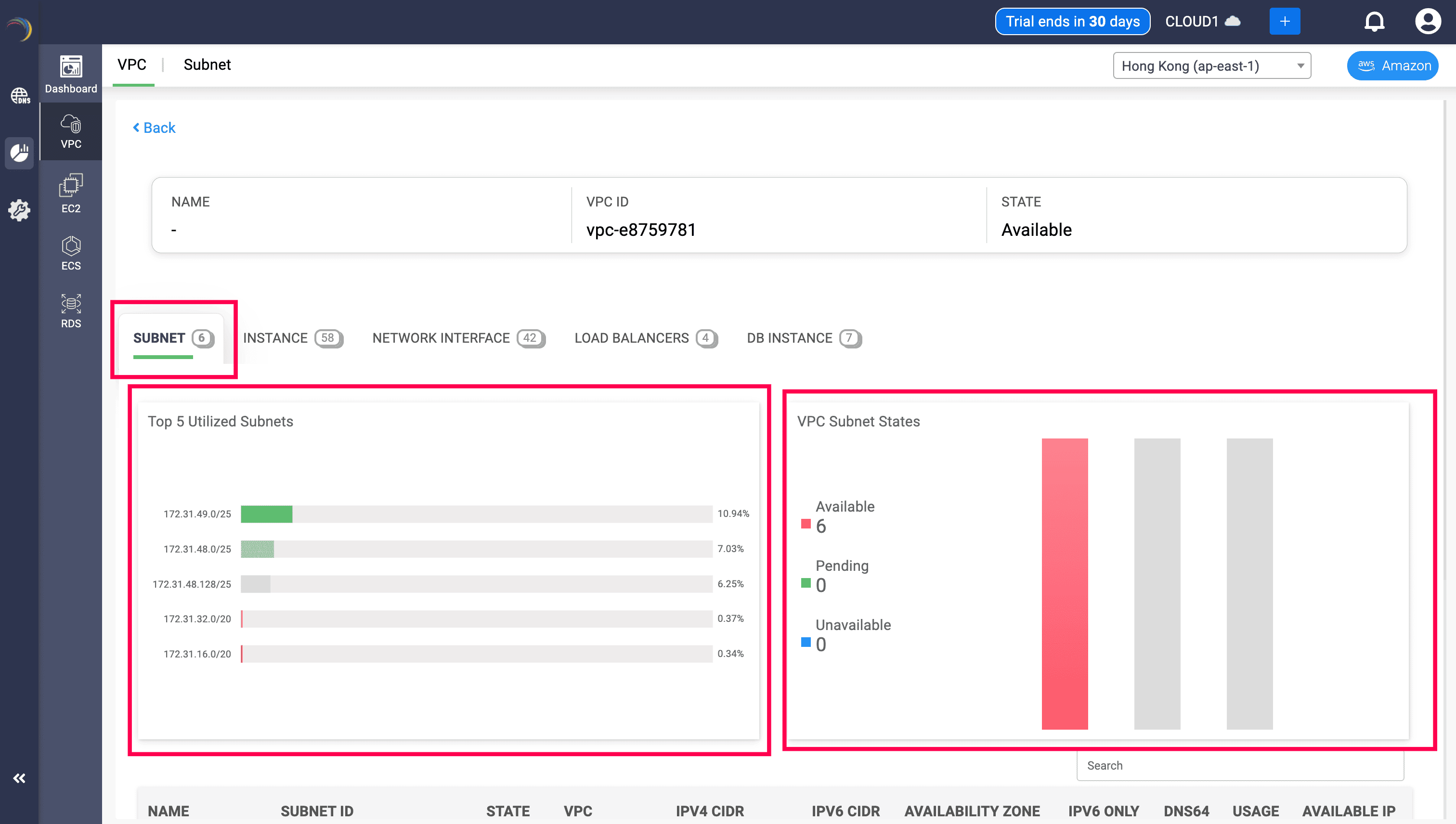
There are three powerful sections under the Subnet tab:
1. Top Subnet Utilization Bar Chart (Left Side)
- Displays the top 5 subnets with the highest IP address consumption.
- Each bar represents a subnet’s total IP range and the percentage of it currently used.
This section instantly identifies IP usage hotspots across your VPC — enabling you to detect:
- Subnets nearing exhaustion (e.g., 80%+ used)
- Underutilized subnets (e.g., 10–20% used)
- Imbalanced address planning
This insight helps you rebalance IP allocations before you run out of space or create inefficient subnet layouts.
2. VPC Subnet State Distribution (Right Side)
- Visualizes the current lifecycle states of all subnets within the VPC:
- Available: Active and provisioned
- Pending: Still provisioning
- Unavailable: Deleted, unreachable, or with failed status
Enables health monitoring of your subnet landscape. You can:
- Detect provisioning delays
- Confirm successful subnet rollout
- Catch misconfigurations that may render subnets unavailable
3. Subnet Inventory Table (Bottom)
The table offers the most complete view of each subnet’s health, capacity, and location in the cloud. Whether you're troubleshooting connectivity issues, scaling infrastructure, or cleaning up unused IP blocks— every field here helps you make faster, more accurate decisions.
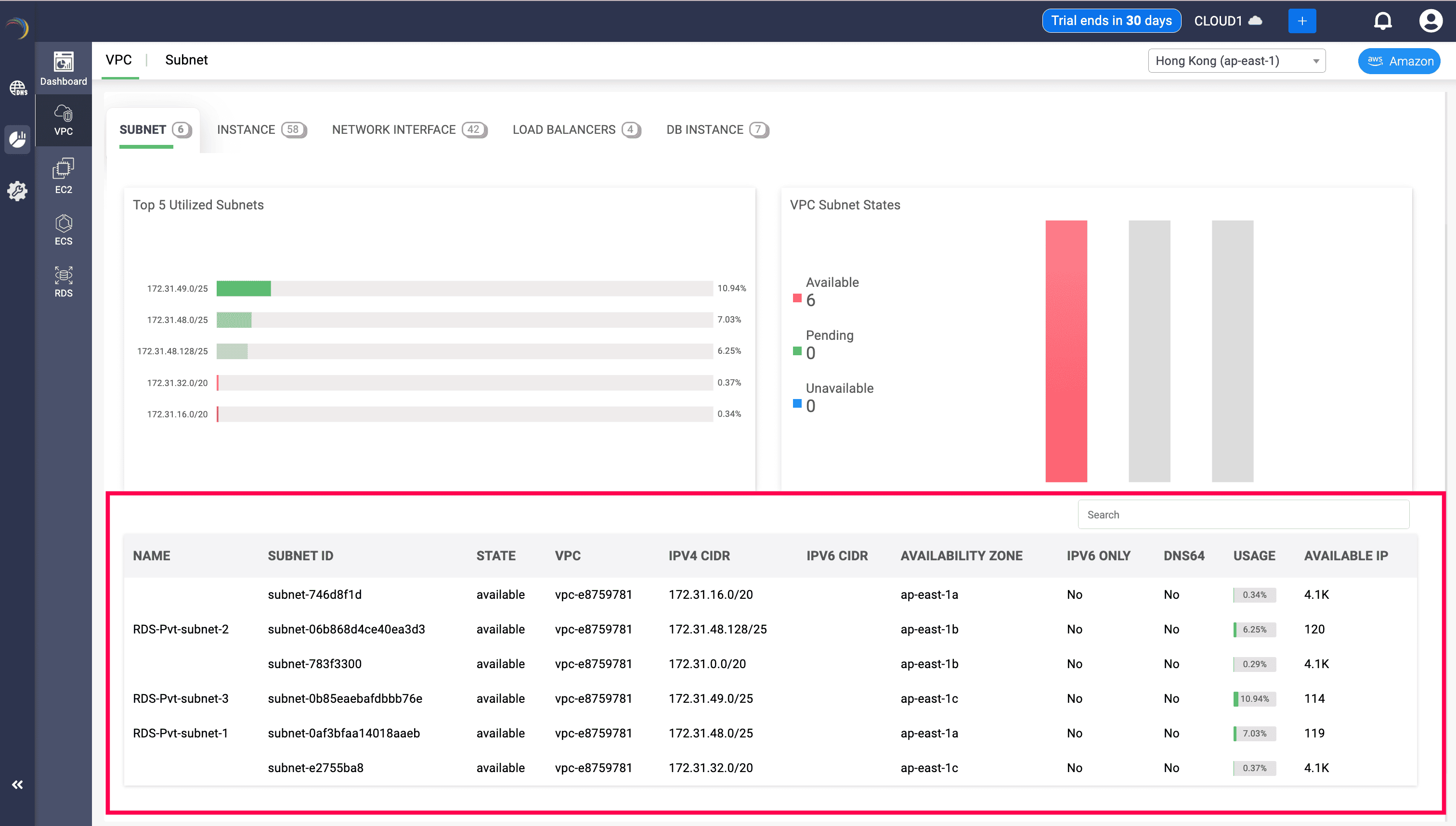
How do each field empower administrators
| Field Name | What It Means | Why It Matters for Admins |
|---|---|---|
| NAME | The subnet's user-assigned name or tag (e.g., RDS-Pvt-subnet-2) | Helps admins quickly identify subnets associated with specific projects, applications, or environments. |
| SUBNET ID | The unique AWS-assigned identifier for the subnet (e.g., subnet-06b868d4ce40ea3d3) | Required for automation, CLI commands, API calls, and scripting. It ensures there's no ambiguity between subnets. |
| STATE | Operational state of the subnet: “available” or “pending” | Tells you whether the subnet is ready for use or still being provisioned. |
| VPC | The ID of the VPC in which this subnet resides (e.g., vpc-e8759781) | Essential for mapping subnets to their parent networks. Multiple subnets can exist across different VPCs. |
| IPV4 CIDR | The IPv4 address block assigned to the subnet (e.g., 172.31.48.0/25) | Shows the IP range available for use inside this subnet. Critical for IP planning and routing configurations. |
| IPV6 CIDR | If enabled, shows the associated IPv6 CIDR block | Indicates whether the subnet supports IPv6, important for dual-stack or IPv6-native deployments. |
| AVAILABILITY ZONE | The physical zone in which the subnet is deployed (e.g., ap-east-1a) | Allows admins to ensure HA and fault tolerance by distributing subnets across multiple zones. |
| IPV6 ONLY | Displays Yes/No if the subnet supports only IPv6 (Yes = IPv4 disabled) | Useful for verifying whether the subnet is intentionally IPv6-only or legacy dual-stack. |
| DNS64 | Indicates whether DNS64 translation is enabled (Yes/No) | DNS64 allows IPv6-only clients to resolve IPv4 destinations. Important for compatibility with IPv4-only apps. |
| USAGE | Percentage of IPs currently allocated or consumed in the subnet | A real-time health indicator showing how “full” the subnet is. Useful for forecasting exhaustion. |
| AVAILABLE IP | The actual number of IPs still available in the subnet (e.g., 114, 4.1K) | Gives precise capacity planning insight—lets admins know when to reclaim, expand, or reallocate address space. |
Why It's Effective
This data in whole enables administrators to:
- Audit current IP consumption in real time
- Spot subnets that need expansion or reassignment
- Validate IPv6 readiness and DNS64 compatibility
- Plan proactive scaling without last-minute chaos
Now navigate to the Instance tab. This view displays all EC2 virtual machines (instances) tied to that VPC — giving admins direct visibility into compute resources and their current operational and networking state. DDI Central will now display a detailed list of EC2 instances deployed within this VPC.
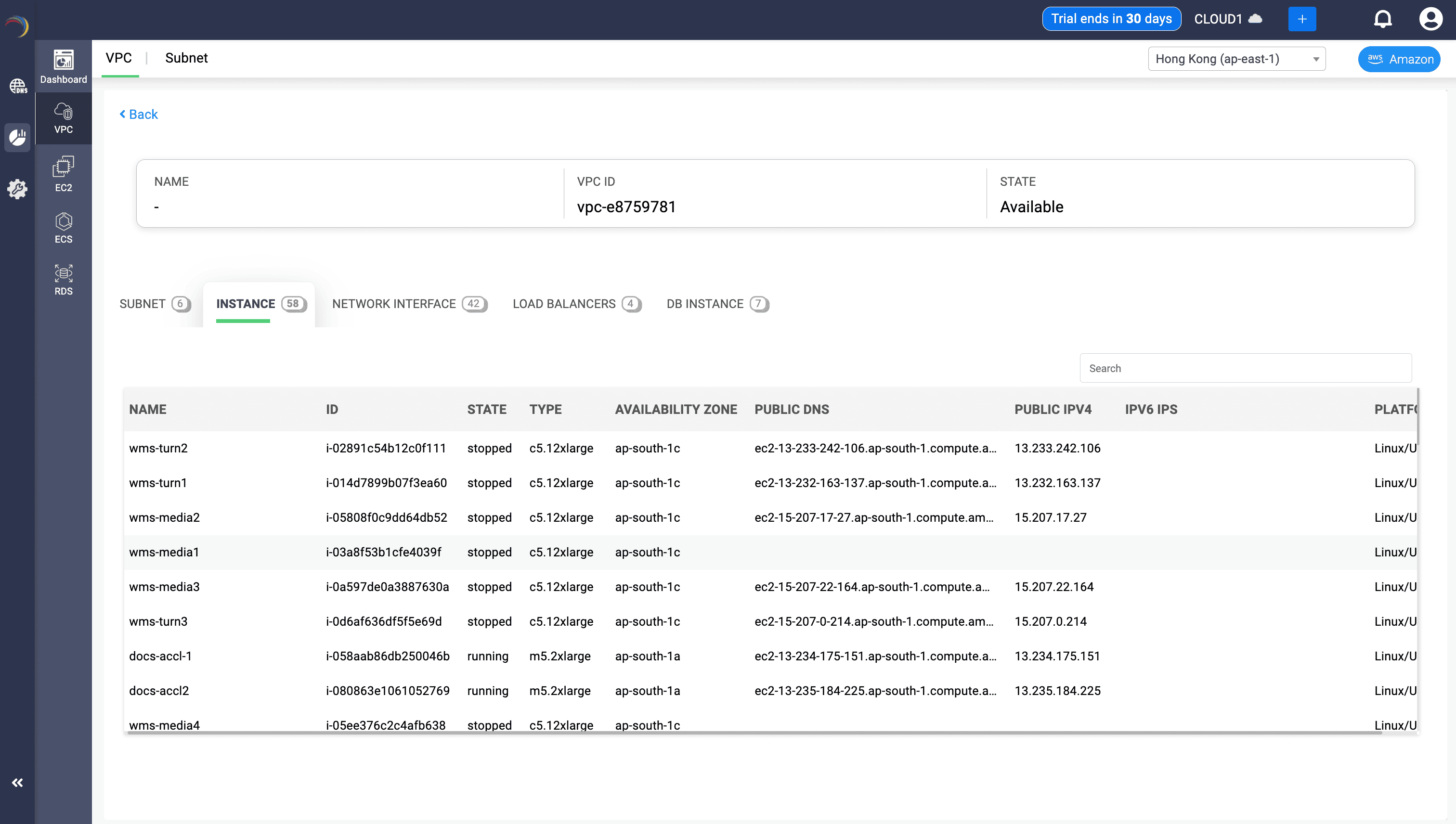
Each instance is listed with the following key fields:
| Field Name | What It Tells You | Why It Matters for Admins |
|---|---|---|
| NAME | The user-friendly label assigned to the instance. | Helps identify the business context of the VM (e.g., "wms-turn2" may relate to a workload or app function). |
| ID | The AWS-assigned Instance ID (e.g., i-02891c54b12c0f111). | Required for automation, IAM policies, tagging, or linking to other AWS services. |
| STATE | Whether the instance is running, stopped, or in another transitional state. | Allows admins to verify if services are available, or if a resource has been decommissioned. |
| TYPE | The performance class of the instance (e.g., c5.12xlarge, m5.2xlarge). | Critical for analyzing compute cost, capacity, and workload suitability. |
| AVAILABILITY ZONE | Indicates the specific zone within the region where the instance is deployed (e.g., ap-south-1c). | Ensures high availability through geographic distribution and can guide subnet placement. |
| PUBLIC DNS / PUBLIC IPv4 | The public-facing address (and hostname) of the instance. | Useful for SSH access, remote troubleshooting, and DNS-based tracing. |
| PLATFORM | The operating system running on the instance (e.g., Linux/Unix). | Confirms compatibility with workloads, agents, or OS-specific policies. |
Why It's Effective
This data in whole enables administrators to:
- Allows centralized visibility into cloud-based compute assets from within the IPAM layer.
- Helps validate zone diversity and balance for DR/HA planning.
- Allows you to track instance availability and spot dormant or stopped VMs that can be deprovisioned.
- Public DNS records make it easy to trace traffic behavior back to a source instance.
Elastic Network Interface (ENI) Snapshot
Go to the Network Interface tab beside Instances. DDI Central displays every Elastic Network Interface deployed within the selected VPC.
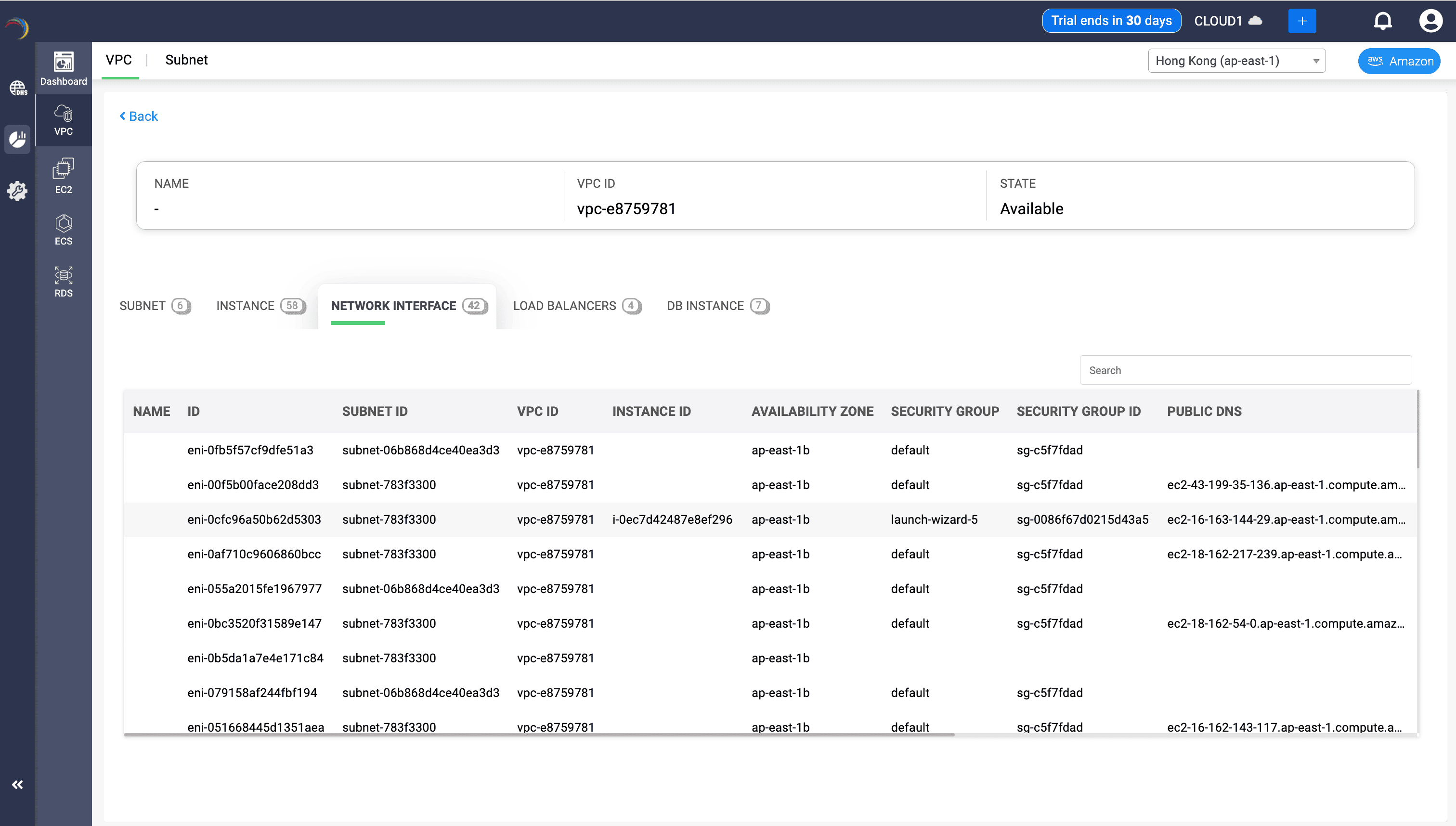
From the same Network Interface tab, scroll further towards right to quickly view the per-interface address mapping. DDI Central makes sure to display deeper address-layer data, helping admins trace every bit of IP allocation tied to an ENI.
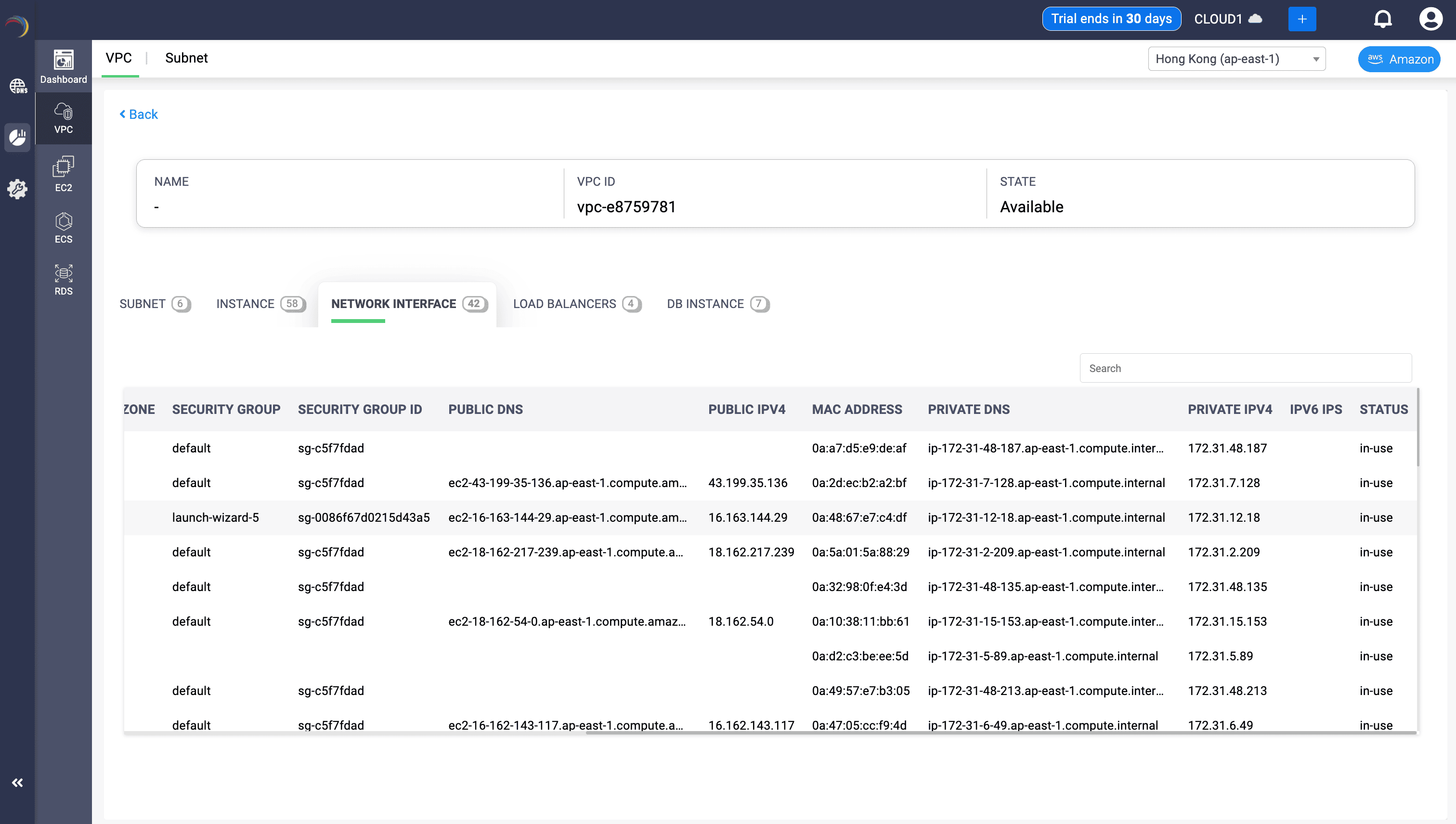
What does the table say
| Field Name | What It Means | Why It Matters |
|---|---|---|
| NAME | The user-friendly name of the ENI | Useful for labeling or identifying purpose-specific ENIs |
| ID | AWS-assigned unique identifier (e.g., eni-0fb5f57cf9dfe51a3) | Required for CLI operations, automation, and scripting |
| SUBNET ID | Indicates which subnet this ENI belongs to | Useful for subnet-bound security tracing |
| VPC ID | Parent VPC of the ENI | Helps visualize ENI placement in network topology |
| INSTANCE ID | The EC2 instance the ENI is attached to | Correlates virtual machines to network interfaces |
| AVAILABILITY ZONE | Region subdivision hosting the subnet (e.g., ap-east-1b) | Helps plan zone-level HA or zonal failover designs |
| SECURITY GROUP NAME | Human-readable name of security policy | Indicates which rule set is applied to the ENI traffic |
| SECURITY GROUP ID | AWS identifier for the security group (e.g., sg-c57f7dad) | Enables fine-grained policy enforcement and audit trails |
| PUBLIC DNS | Resolves public-facing DNS endpoint if assigned | Enables DNS-based tracing and resolution |
| MAC ADDRESS | Hardware address of the ENI | Identifies interface at Layer 2 or for DHCP-based configs |
| PRIVATE IPV4 | Internal IP used within the VPC | Core to routing, security policies, and app connectivity |
| PRIVATE DNS | DNS record mapped to internal IP | Enables internal name resolution within the VPC |
| PUBLIC IPV4 | The public-facing IP assigned | Required for internet access or SSH/RDP visibility |
| IPV6 IPS | Any IPv6 addresses assigned | Indicates readiness for IPv6 workloads |
| STATUS | Current state (e.g., in-use) | Helps detect stale or active network interfaces |
Why It's Effective
- Allows admins to verify which interfaces are live, associated, or orphaned
- Great for tracing network bottlenecks or firewall rule failures
- Centralizes security group-to-interface visibility
- Crucial for troubleshooting “no connectivity” issues from instances or services
- Provides end-to-end address tracking for security audits and troubleshooting
- Helps avoid duplicate IPs or binding failures across reboots or scaling events
- Ideal for incident forensics or confirming DNS-to-IP linkages
- Supports compliance reporting with MAC/IP/DNS binding logs
9. Load Balancer Intelligence
Now switch to the Load Balancers tab within the selected VPC view. DDI Central displays an insightful table that provides a unified view of all Elastic Load Balancers (ELBs) associated with the selected AWS VPC. It helps administrators assess traffic flow distribution, high availability, and fault tolerance.
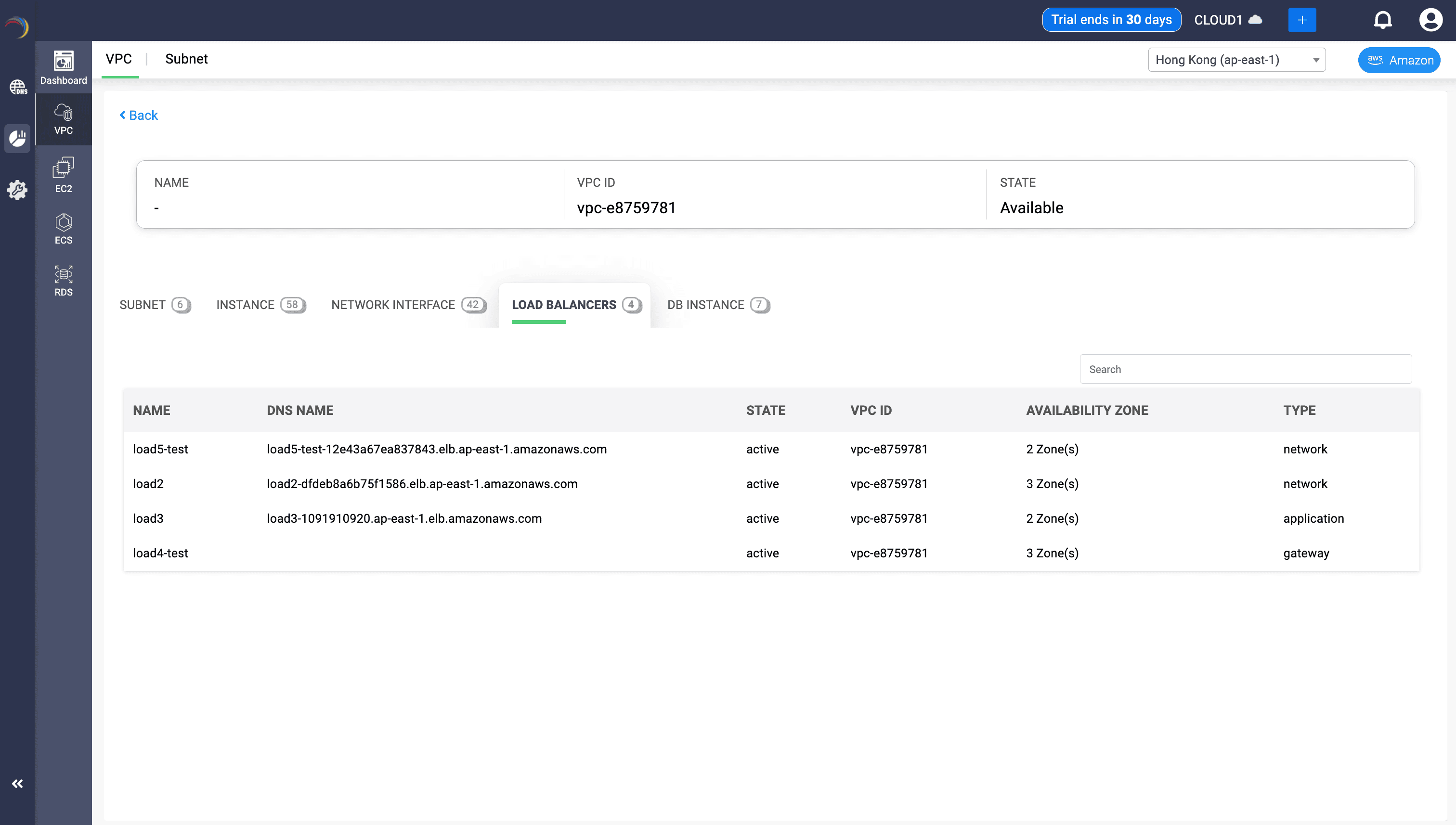
The table presents the following insights:
| Field | What It Represents | Why It Matters |
|---|---|---|
| Name | User-assigned identifier for the Load Balancer (e.g., load5-test) | Helps distinguish between different ELBs across staging, production, or test environments. |
| DNS Name | Endpoint used by clients to reach the ELB (e.g., *.elb.amazonaws.com) | Critical for traffic routing and ensuring DNS resolves correctly for your apps. |
| State | Indicates if the ELB is active or inactive | Shows readiness for use or if troubleshooting is required for deactivated ELBs. |
| VPC ID | The virtual network the ELB belongs to (e.g., vpc-e8759781) | Ensures the ELB is correctly placed within the expected network boundary. |
| Availability Zone | Number of AZs spanned (e.g., 2 Zone(s), 3 Zone(s)) | Indicates fault tolerance and resiliency — more zones mean better redundancy. |
| Type | The ELB category: network, application, or gateway | Helps match the load balancer to the correct OSI layer and traffic handling behavior. |
Why It's Effective
- Ensures that load balancers are properly distributed across zones for high availability.
- Confirms the right type of load balancer is deployed per use case.
- Validates that the DNS entry is accessible and resolves correctly to maintain uptime.
- Allows admins to act quickly if a load balancer appears inactive, misconfigured, or not adequately zoned.
Load Balancer Intelligence
Now switch to the Load Balancers tab within the selected VPC view. DDI Central displays an insightful table that provides a unified view of all Elastic Load Balancers (ELBs) associated with the selected AWS VPC. It helps administrators assess traffic flow distribution, high availability, and fault tolerance.
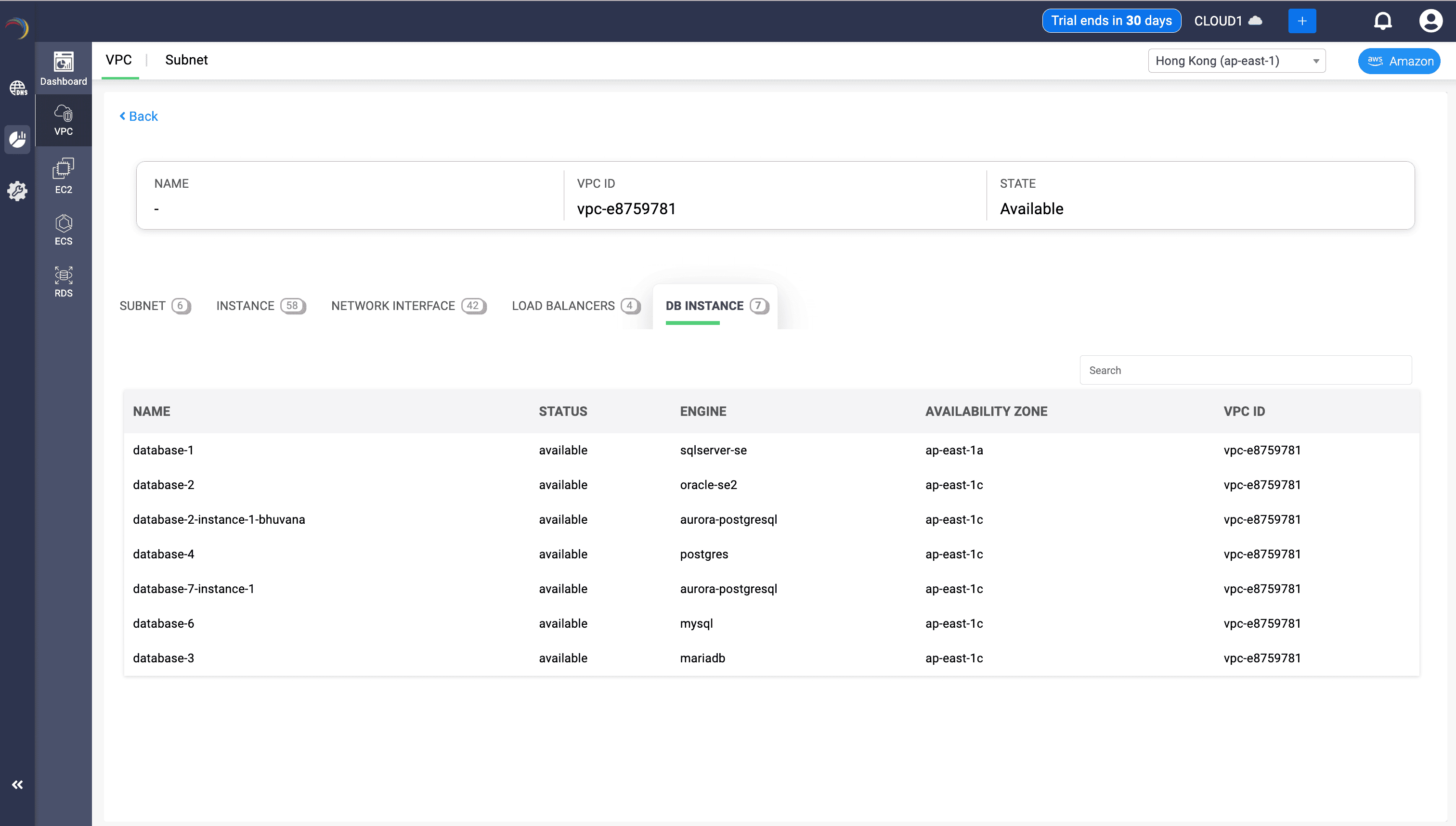
The table presents the following insights:
The RDS inventory of a VPC presents the following insights:
| NAME | STATUS | ENGINE | AVAILABILITY ZONE | VPC ID |
|---|---|---|---|---|
| database-1 | available | sqlserver-se | ap-east-1a | vpc-e8759781 |
| database-2 | available | oracle-se2 | ap-east-1c | vpc-e8759781 |
| database-2-instance-1-bhuvana | available | aurora-postgresql | ap-east-1c | vpc-e8759781 |
| database-4 | available | postgres | ap-east-1c | vpc-e8759781 |
| database-7-instance-1 | available | aurora-postgresql | ap-east-1c | vpc-e8759781 |
| database-6 | available | mysql | ap-east-1c | vpc-e8759781 |
| database-3 | available | mariadb | ap-east-1c | vpc-e8759781 |
Why It's Effective
- High Availability Planning: The AZ field helps ensure your RDS instances are spread across multiple zones for fault tolerance.
- Backend IP Planning: Knowing the status and engine types helps you align database traffic, IP allocation, and DNS naming schemes.
- Troubleshooting: Quickly detect failed or missing RDS components in your service chain.
- DNS Routing Validation: The presence and health of these RDS entries validate DNS-based application failovers.
Analyzing AWS Subnets in DDI Central
With AWS integration, network administrators can extract deep value from AWS subnet visualizations within DDI Central. Rather than focusing on just the VPC layer, this guide emphasizes subnet-level observability—your most granular and dynamic layer for IP planning, access routing, and service segmentation.
In AWS:
- A VPC (Virtual Private Cloud) is a logically isolated network environment—a container for networking resources like subnets, route tables, and gateways.
- A Subnet is a segmented portion of a VPC’s IP address range that you deploy resources into (like EC2 instances).
In the context of VPCs (Virtual Private Clouds) in AWS, a subnet is a segment of the IP address range of a VPC where you can place your resources, such as EC2 instances, RDS databases, and Lambda functions.
Here’s a breakdown:
What Is a Subnet:
- A subnet is a range of IP addresses within a VPC.
- It helps you organize and isolate resources based on function, security, or availability.
Relationship to VPC:
- A VPC provides a private, isolated network environment with a defined CIDR block (e.g., 10.0.0.0/16).
- Subnets are slices of that block (e.g., 10.0.1.0/24, 10.0.2.0/24), each associated with a specific Availability Zone.
Types of Subnets:
- -Public Subnet: Has a route to the internet through an internet gateway (used for web servers, bastions).
- -Private Subnet: Has no direct internet route (used for databases, internal services).
What are Tags? Why do subnets often have more visible or required tags?
AWS allows tagging of almost all resources, including VPCs and subnets. Tags are key-value pairs (e.g., Environment: Production) used for:
- Resource grouping
- Cost allocation
- Access control (via IAM policies)
- Automation workflows
VPCs can be tagged, but often serve as a broader container. On the other hand, subnets are closer to where resources live and route traffic—so tagging them helps AWS services, administrators, and automation tools make better decisions.
Subnets and Availability Zones (AZ)
Subnets within a VPC must be associated with specific Availability Zones (AZs), and they can span different AZs. A VPC’s CIDR block (e.g., 10.0.0.0/16) is a large IP address range that you can subdivide into multiple subnets. Each subnet is mapped to exactly one Availability Zone.
You can (and should) create and spread multiple subnets in different AZs as it is essential for:
- Highly available architectures (e.g., load balancers across multiple subnets)
- Auto scaling groups
- Database failover support
- Disaster recovery
Here’s how to access and analyze AWS VPCs in DDI Central:
- Open a Cloud Observability of your choice
- Navigate to IPAM->VPC menu inside the selected cluster
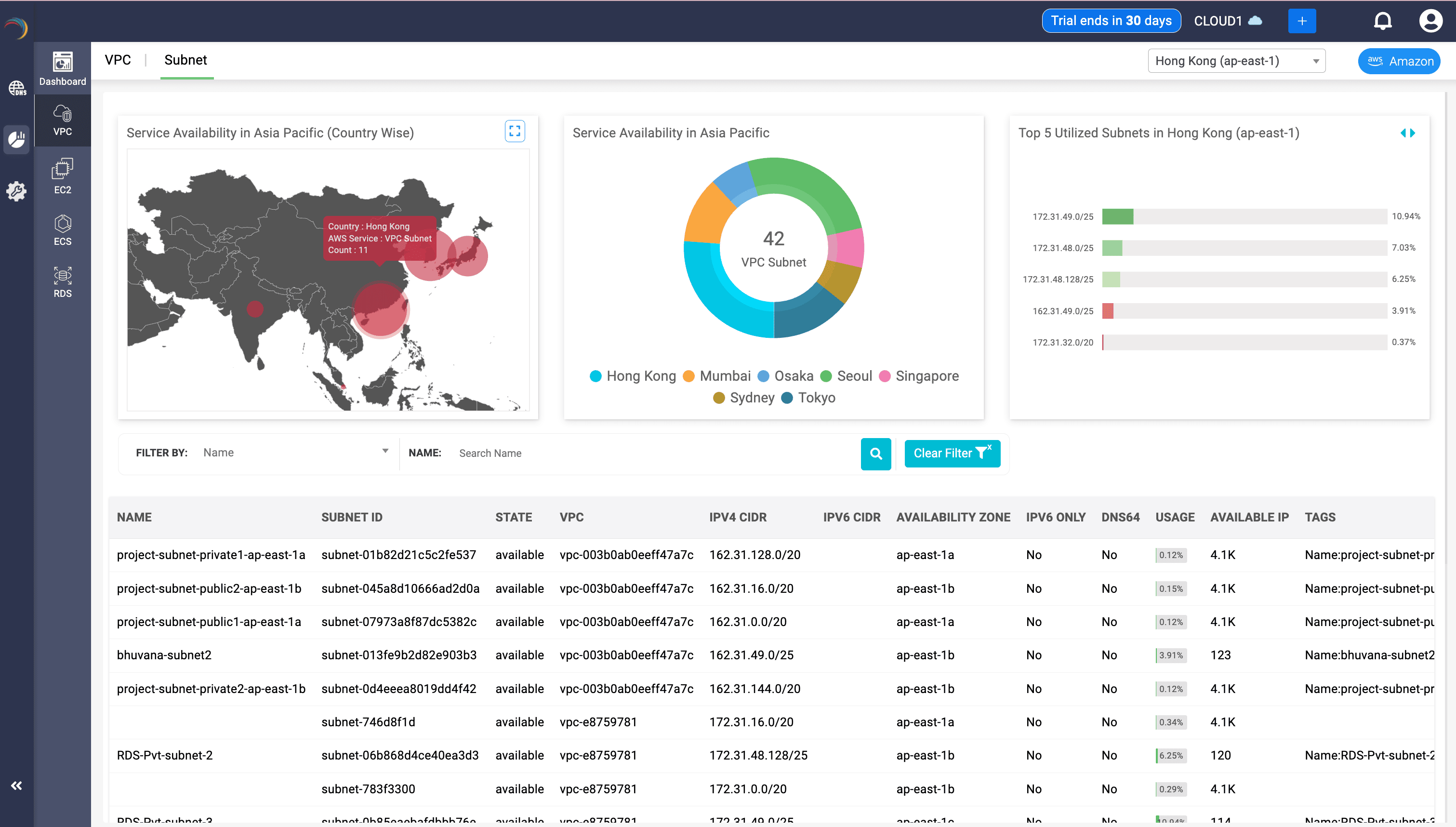
Subnet availability overview across multiple AZs
This screen above provides an aggregated regional view of all subnets across multiple VPCs, empowering teams to understand how IP space is fragmented and utilized. In essence, this dashboard transforms raw subnet metadata into actionable intelligence—supporting cost control, risk mitigation, and uptime for network-driven workloads.
- Map Panel (Left)
- Displays subnet distribution by country using red heatmap overlays.
- Tooltip shows:
- Country (e.g., Hong Kong)
- AWS Service: VPC Subnet
- Count: Total subnets provisioned
- This reveals regional subnet density and infrastructure concentration zones.
- Donut Chart (Center)
- Breaks down 42 subnets across APAC locations like Tokyo, Seoul, Hong Kong, and Singapore.
- It offers a normalized visual of infrastructure deployment by region.
- Top Utilized Subnets (Right)
- Highlights top 5 subnets in Hong Kong with the highest IP utilization.
- It enables Admins to quickly identify which subnets are nearing exhaustion for proactive expansion.
- Table View (Bottom)
- Key Fields:
- Subnet Name: Human-readable context for project ownership or role (e.g., RDS, public, private)
- ID: Unique reference for automation, config, and routing
- State: Confirms health or availability of each subnet
- Associated VPC: Shows which VPC each subnet belongs to—important for policy boundaries
- (IPv4)CIDR: Displays subnet IP range for IP planning and overlap checks
- Availability Zone: Ensures redundancy and AZ spread validation
- IPv6 / DNS64: Flags subnets with special networking behavior
- Usage: Quantified IP consumption—ideal for proactive alerting and capacity planning
- Available IP: Real-time visibility into how much space remains in each subnet
- Tags: Provides metadata for ownership, billing, lifecycle stage (e.g., Name, Project)
- Network teams can monitor subnet saturation before IP exhaustion or outages occur
- Cloud architects can audit subnet-to-AZ distribution to maintain fault tolerance
- Security admins can quickly scan for exposed or IPv6-enabled subnets
- Ops can align usage and allocation with organizational tagging policies
- Engineers can clean up low-usage or overlapping subnets
Why This View Matters
Associated VPCs with Subnet Context
While the subnet is a slice of the VPC, this section helps confirm which VPCs the subnet lives under and their CIDR plans. This VPC tab contextualizes the subnet within the broader cloud network architecture—giving the admin the visibility to enforce policy, plan growth, and troubleshoot intelligently.
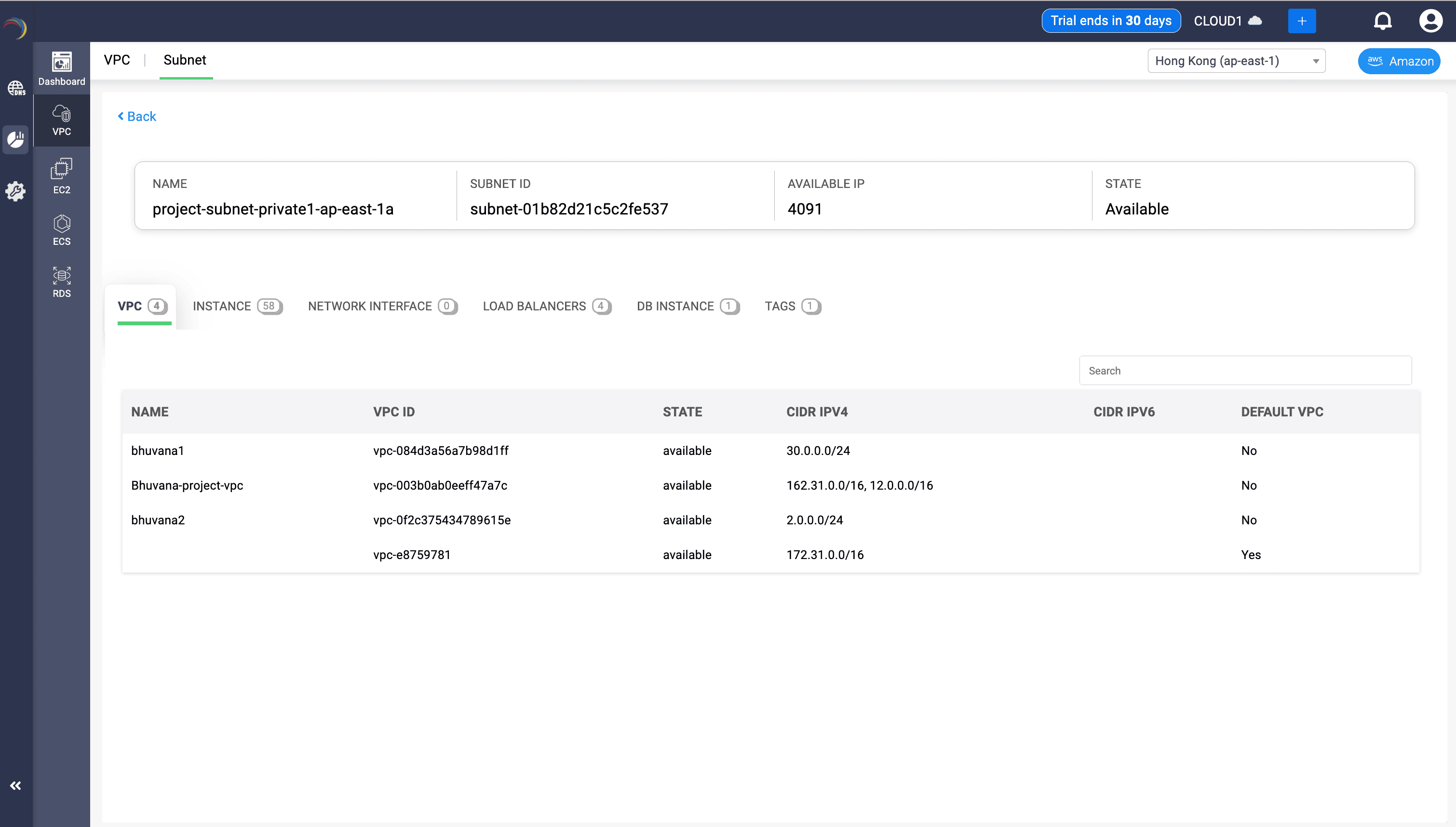
- Fields:
- Name: Identifies the VPC to which the subnet belongs or may be associated with. Useful for confirming environment boundaries (e.g., dev, test, prod).
- VPC ID: A unique identifier that lets admins trace routing tables, internet gateways, and peering connections tied to the subnet. CIDR ranges (IPv4 and optional IPv6).
- State: Verifies that the VPC is active and routable—important during provisioning or troubleshooting.
- CIDR IPv4: Shows the IP range available in the VPC. Helps confirm whether the subnet’s IP block is within bounds and whether enough space exists for scaling.
- CIDR IPv6: Indicates if the VPC is IPv6-enabled, helping admins plan for dual-stack or modern networking compatibility.
- Default VPC: Flags whether the VPC is AWS’s default (auto-configured) or a custom-designed one—important for enforcing strict segmentation policies.
- Ensures context when assessing routing behaviors or peering implications.
Why It Matters in a Subnet View
- Validates whether the subnet is part of a custom VPC with specific security/routing rules or a default VPC with more relaxed controls.
- Assists in identifying overlapping IP ranges across VPCs that could cause routing conflicts or break peering setups.
- Ensures subnet-to-VPC alignment before attaching route tables, NAT gateways, or deploying hybrid cloud connectors.
- Helps in auditing and compliance: network teams can ensure workloads are deployed in the correct VPC context.
EC2 Workloads in Subnet
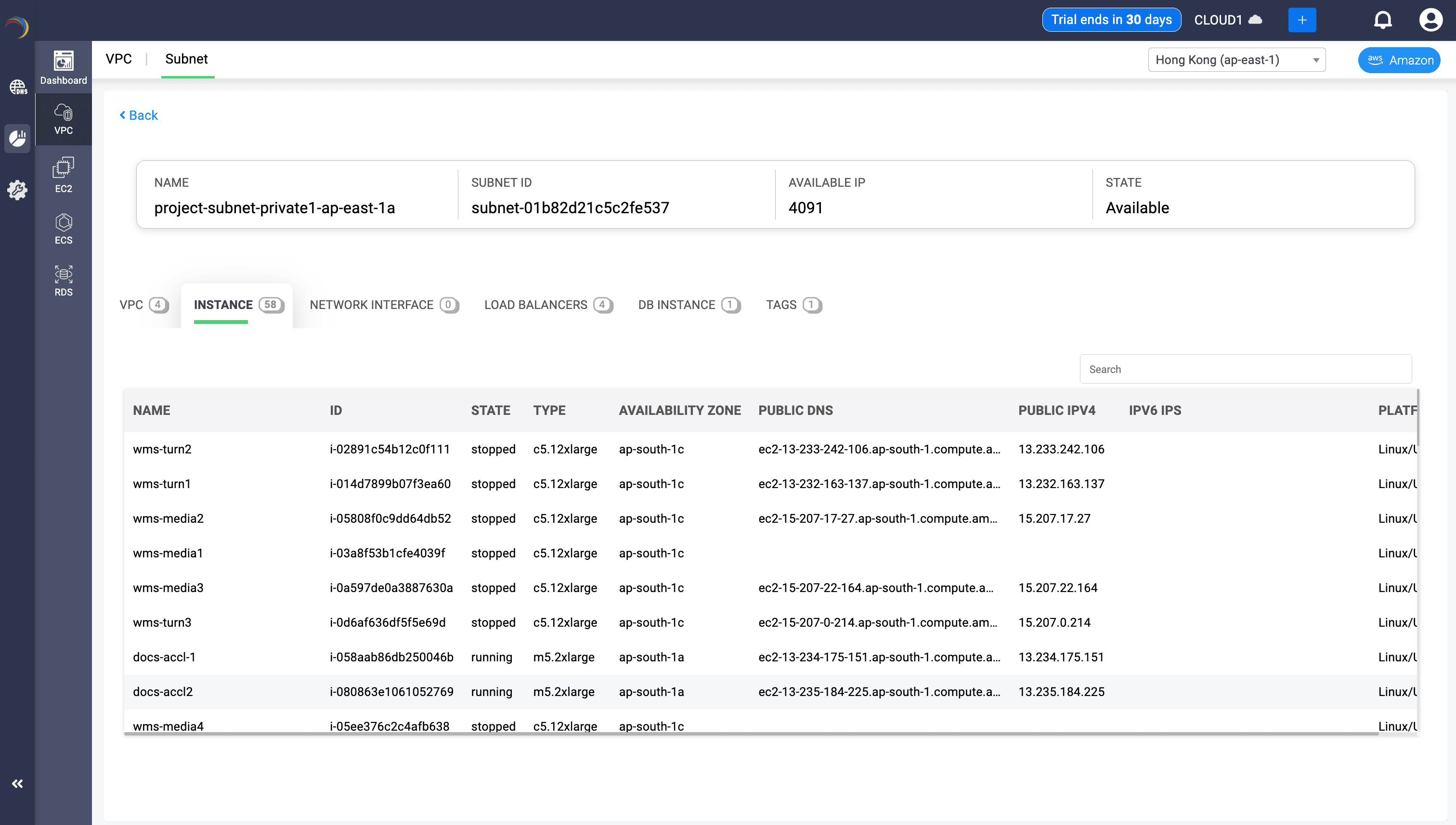
Gives a list of virtual machines actively or historically using the subnet. It provides subnet-level visibility into the EC2 instances. Even in a read-only view, each field is rich with operational value for a network administrator overseeing workload distribution, access, and security posture. This view lets a network admin zoom in on how compute resources behave, communicate, and are distributed within a single subnet slice—essential for maintaining a secure, efficient, and well-architected cloud network.
Fields:
- Instance Name: Identifies workload role (e.g., media, WMS, docs). Helps in inventory management and naming convention enforcement.
- ID: Unique identifier of each instance. Critical for correlating logs, automation scripts, and audits.
- Instance State: Shows if the instance is running or stopped—useful for cost control, resource planning, and incident response.
- Type: Indicates instance size and capacity (e.g., c5.12xlarge, m5.2xlarge). Helps gauge subnet resource density and impact on IP exhaustion.
- Availability Zone: Reveals the AZ distribution of workloads—key for HA design and latency planning.
- Public DNS / Public IPv4: Provides external reachability insights. Identifies which instances are internet-facing and subject to additional security scrutiny.
- IPv6 IPs: Displays IPv6 readiness. Important for hybrid and modern app architectures.
- Platform: Reveals the OS platform (Linux/UNIX) for OS-specific firewalling or patching compliance.
- Helps determine traffic origin and capacity stress imposed on the subnet.
Why This Matters in a Subnet View:
- Confirms whether the subnet is hosting production-facing compute or backend-only workloads.
- Enables rapid identification of improperly placed or idle/stopped instances.
- Supports network isolation validation: e.g., whether public IPs should exist in this subnet.
- Aids in identifying AZ imbalance that could affect availability or performance.
- Improves capacity planning: is this subnet approaching IP exhaustion due to instance count?
Network Interface Mapping (ENI)
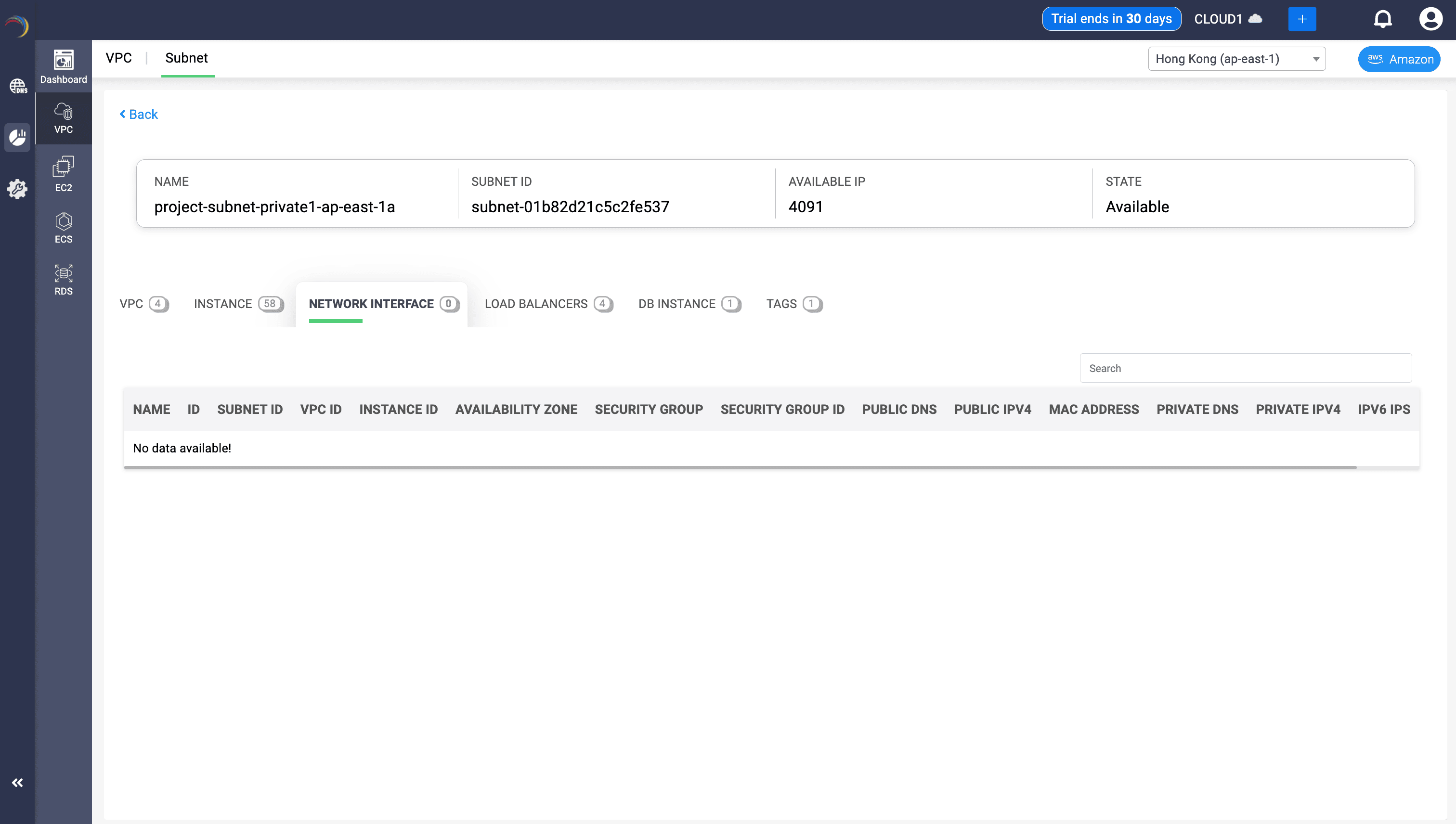
This section displays all ENIs of a subnet.
Fields:
- Name / Subnet ID: Helps quickly identify and reference specific subnets in large VPC architectures.
- VPC ID: Ties the subnet to its parent network boundary, important for routing, NATs, and gateways.
- Instance ID: Shows which EC2 instances are attached to this subnet — helps understand workload distribution.
- Availability Zone: Clarifies fault domain — helps ensure high availability through multi-AZ architecture.
- Security Group / ID: Reveals which firewall rules govern traffic for instances in this subnet — crucial for audit and compliance.
- Public / Private DNS: Indicates DNS naming for attached resources — aids in debugging and service discovery.
- Public / Private IPv4: Lets you track assigned IPs — useful for IP planning, troubleshooting, and inventory management.
- MAC Address: Can help in deep-level diagnostics, network capture correlation, or static IP assignments.
- IPv6 IPs: Supports dual-stack visibility if the subnet uses IPv6 — important for modern network scaling.
Why This View Matters:
- Gives a per-subnet breakdown of all network interfaces (ENIs) and their associations.
- Helps ensure proper IP segmentation, routing isolation, and AZ alignment.
- Aids in troubleshooting (e.g., "Why can’t this instance reach the internet?") by cross-verifying IPs, AZ, SGs, and instance bindings.
- Supports cost monitoring and capacity planning by viewing available IPs and usage density.
Load Balancers Active Within Subnet Scope
Provides visibility into DNS-driven traffic handling for workloads hosted in or routed through the subnet's VPC.
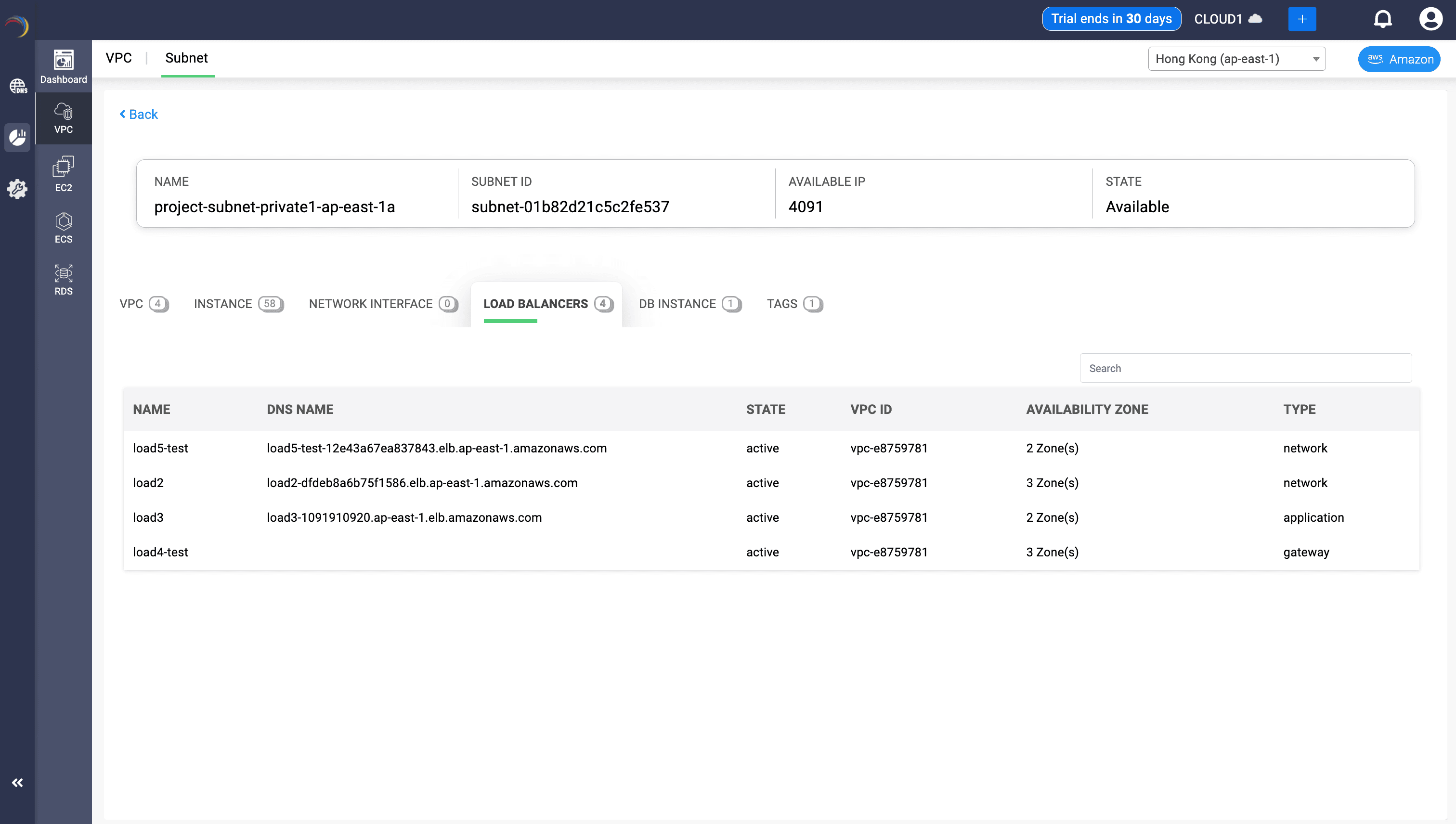
Fields:
- Load Balancer Name: Identifies which load balancers are actively serving resources within this subnet. Helpful for quick correlation with infrastructure services.
- DNS Name: Shows the publicly or internally resolvable name used by clients to reach services. Useful for testing, monitoring, and endpoint validation.
- State: Indicates operational status (e.g., active/inactive). Helps quickly identify health or deployment issues tied to the subnet.
- VPC ID: Verifies which VPC the load balancer belongs to. Ensures proper segmentation and routing.
- Availability Zone (AZ): Reveals redundancy spread. Load balancers deployed across multiple AZs improve fault tolerance and load distribution.
- Type: Shows the purpose of each load balancer (application, network, gateway). This helps in understanding traffic patterns and where in the OSI model the traffic is handled.
Why It Matters:
- Enables subnet-level troubleshooting when latency or access issues occur.
- Helps assess whether application traffic is properly distributed across zones.
- Validates whether load balancing is set up for public access, internal routing, or API gateway functions.
- Supports planning for scaling, security group assignments, and subnet utilization.
This view, even at a glance, is a tactical hub for understanding how load-balanced traffic flows through a network slice (subnet) in a complex AWS environment. Highlights DNS path redundancy and fault-tolerant delivery per subnet-aware applications.
RDS Instances Bound to Subnet
Displays databases deployed in or routed through the subnet.
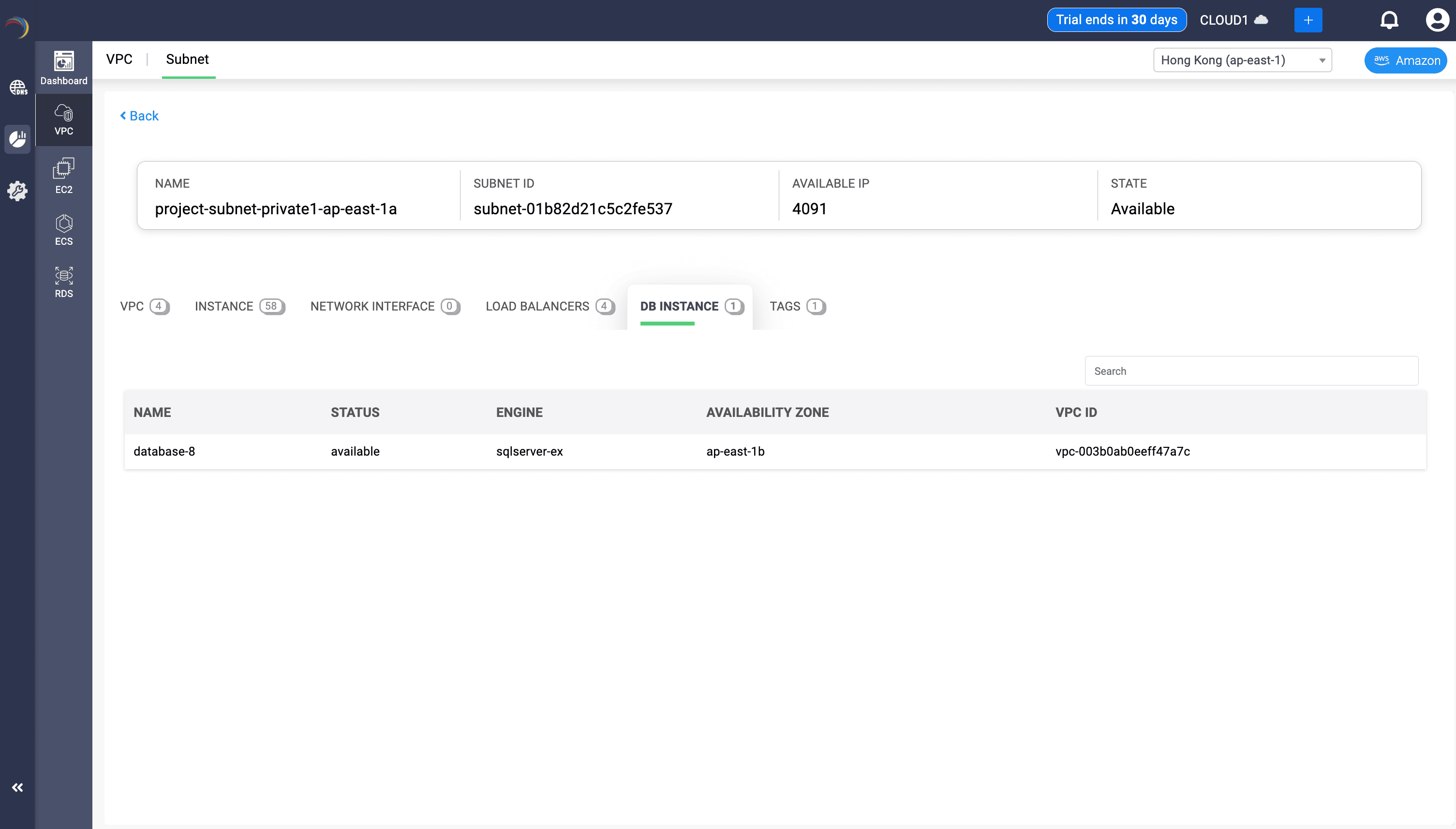
Displays databases deployed in or routed through the subnet.
- Fields:
- Name: Identifies the database workload operating in this subnet. Useful for correlating network flows, auditing, and troubleshooting.
- Status: Shows if the DB instance is healthy, pending, or failing—critical for real-time operational awareness.
- Engine: Displays the database engine (e.g., sqlserver-ex), informing the admin about potential port/protocol needs and performance characteristics.
- Availability Zone: Indicates which AZ this database resides in—important for understanding redundancy, failover design, and latency sensitivity.
- VPC ID: Confirms the broader network boundary that governs this subnet, helping enforce routing, firewall, and segmentation policies.
- Brings data-layer visibility to the network admin—align IP scopes to data workloads.
Why This Matters in the Context of a Subnet
- Confirms whether the subnet is serving critical back-end workloads like databases—useful for deciding whether the subnet should remain private (non-routable from the internet).
- Helps with designing and validating subnet-AZ alignment (e.g., DBs in one AZ, apps in another for HA).
- Supports IP planning—admins can ensure there's enough capacity left in the subnet for future DB replicas or read-only nodes.
- Enables root-cause investigation in case of connection drops, latency spikes, or security incidents affecting data services.
In short, this tab gives subnet-level clarity into how data workloads are distributed, isolated, and operating—essential for maintaining secure, high-performing infrastructure in cloud-native environments.
VPC Subnet Insights: Why It's Effective:
Focusing on the subnet—not just the VPC—provides:
- The most accurate visibility into address planning, usage, and exhaustion
- A clean map between IP resources and workloads (EC2, ELB, RDS)
- A scalable lens to manage DHCP scopes, DNS associations, and AZ-resilient design
- Tight control over fragmentation and collision at the infrastructure edge
New to ADSelfService Plus?
Related Articles
DDI Central for Microsoft DNS DHCP
About ManageEngine DDI Central DDI Central is a comprehensive network management solution that unifies DNS, DHCP, and IP Address Management (IPAM) to enhance operational efficiency and network stability. It is deployed as an overlay on your existing ...AWS Integration with DDI Central
AWS Integration with DDI Central DDI Central seamlessly integrates with Amazon Web Services (AWS) to provide deep visibility and centralized oversight of key cloud infrastructure components— EC2 instances, ECS services, RDS databases, VPCs, and their ...Analyzing AWS EC2 Network Resources in DDI Central
Analyzing AWS EC2 Network Resources in DDI Central Amazon EC2 (Elastic Compute Cloud) is at the heart of most AWS deployments, powering scalable virtual machines for applications, services, and infrastructure workloads. But managing EC2 efficiently ...AWS Integration Dashboard in DDI Central
AWS Integration Dashboard in DDI Central DDI Central’s AWS integration dashboard provides network administrators a centralized, visual snapshot of their AWS resource landscape across VPC, EC2, ECS, and RDS services. This guide outlines how to ...AWS RDS Instance Observability in DDI Central
AWS RDS Instance Observability in DDI Central Amazon RDS (Relational Database Service) is a managed database platform that simplifies the deployment and scaling of databases like MySQL, PostgreSQL, SQL Server, and more. It abstracts infrastructure ...