How to prevent a brute force attack with ADSelfService Plus
What is a brute force attack?
In a brute force attack, cybercriminals try to guess the password of a target user account, analyze the result, and try again until they succeed. This process could take anywhere from weeks to months. Though this method is simple, it has an enormous success rate as users are susceptible to using weak passwords, like qwerty, 123456, abcdef123, password@123, etc.
An account lockout policy is the method used by most admins against brute force and reverse-brute force attacks (also known as password spray attacks). Essentially, the account lockout policy "locks out" a user after a set number of failed login attempts.
How safe are users' Active Directory (AD) accounts?
It's a generally accepted fact that users are bad at remembering their passwords. Many organizations enable password sync to help users so they only need to remember one password to access multiple applications. Hackers use this to their advantage by only targeting the inadequately protected connected applications that may or may not have enabled the account lockout option. With password sync, hackers only need to crack one user's password to gain access to all their connected applications, including AD, and cause havoc.
Wouldn't it be great if admins could prevent brute force attacks by enforcing hard-to-crack passwords for all user accounts? We think so, too.
How to stop brute force attacks with Password Policy Enforcer
ADSelfService Plus' Password Policy Enforcer feature offers advanced password policy settings that help admins prevent brute force attacks and keep up with the evolving cyber threat landscape by:
- Banning leaked or weak passwords, keyboard sequences, and palindromes.
- Restricting consecutively repeated characters from the username or old password, as well as common character types at the beginning or end of the passwords.
- Allowing users to use Unicode characters in their passwords.
- Enforcing passphrases instead of password complexity rules if the password length is above a set number.
And more!
The best part? Admins can enforce the configured custom password policy on both AD and cloud applications.
 Tip: ADSelfService Plus also allows admins to enable image and audio CAPTCHA to prevent brute force attacks (path: Admin > Customize > Logon Settings. Select Enable CAPTCHA for login page).
Tip: ADSelfService Plus also allows admins to enable image and audio CAPTCHA to prevent brute force attacks (path: Admin > Customize > Logon Settings. Select Enable CAPTCHA for login page).How to create a custom password policy in ADSelfService Plus
- Log in to ADSelfService Plus with admin credentials.
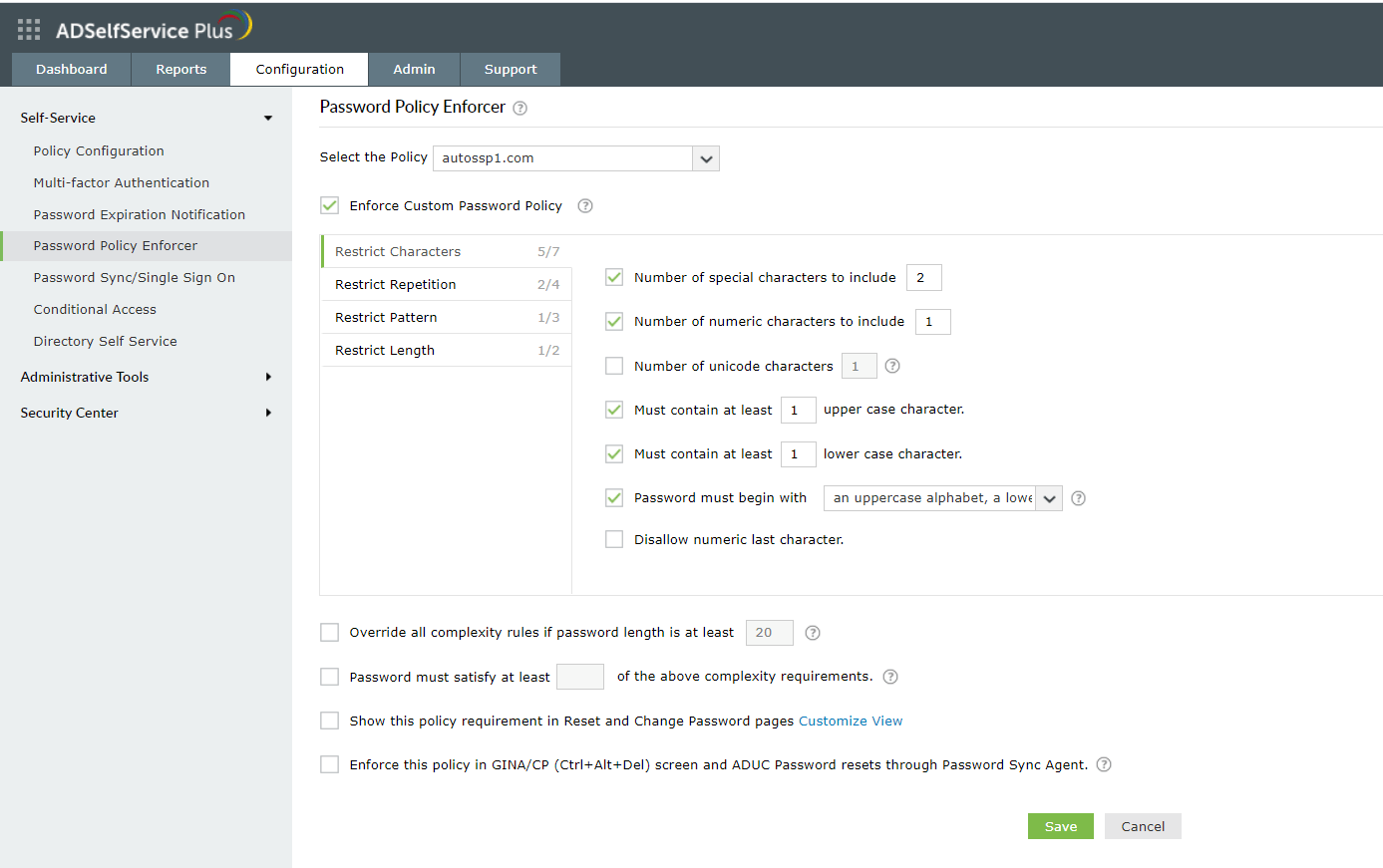
- Navigate to Configuration > Self-Service > Password Policy Enforcer.
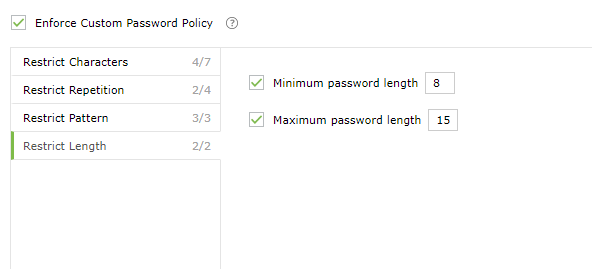
- Enable Enforce Custom Password Policy.
- In this section the admin can manage:
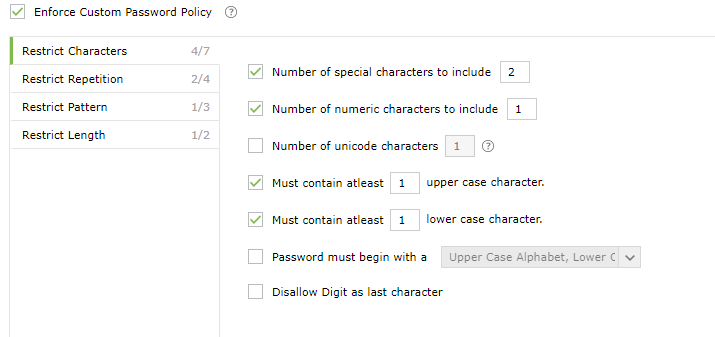
- Characters: Restrict the number of special characters, numbers, and Unicode characters used.
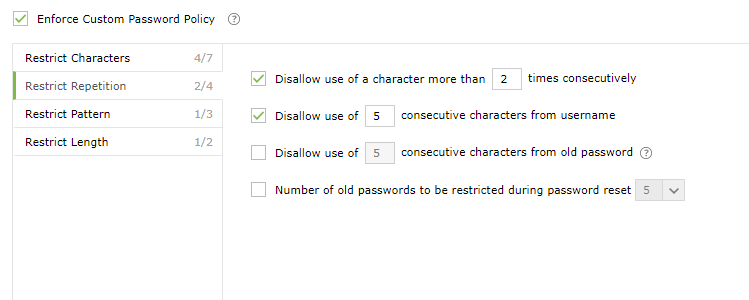
- Repetition: Enforce password history during password reset, and restrict the consecutive repetition of a specific character (e.g., aaaaa or user01) from the username or password.
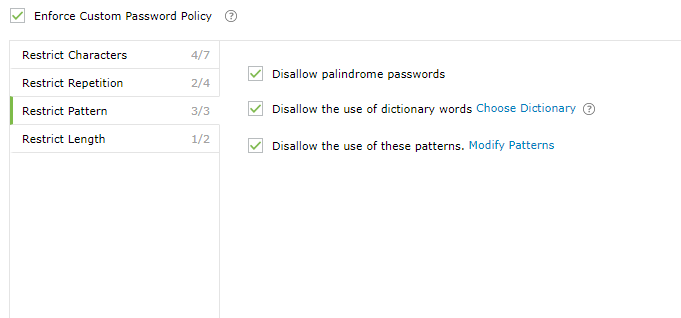
- Patterns: Restrict keyboard sequences, dictionary words, and palindromes.
- Length: Specify the minimum and maximum password length.
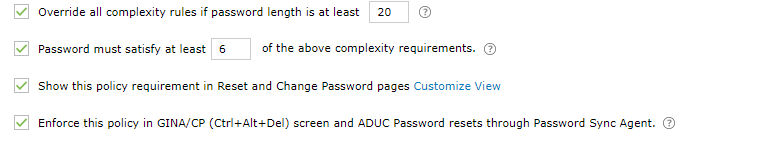
- Allow users to bypass complexity requirements when the password length exceeds a predefined limit (say, 20 characters).
- Enter the number of policy settings a user's password must comply with (say, 5) during self-service password reset and password change.
- Enforce the configured password policy settings during password resets from both the ADUC console and the change password screen.
- To help users create passwords that comply with the enforced policy settings, display the password policy requirement on both the reset and change password pages.
New to ADSelfService Plus?
Related Articles
Remote Desktop Protocol password brute-force attacks
Work-from-home conditions have become increasingly prevalent since the pandemic. This shift in working arrangements has made remote desktop applications and VPNs essential tools for accessing enterprise resources within corporate networks. What is ...How to disallow palindrome passwords using ADSelfService Plus
Having a secure password is of paramount importance to ensure the safety of your network. A password's strength depends on the length of the password, the different types of characters used, the number of repeated characters, the sequence of ...Password Policy Enforcer configuration
ADSelfService Plus' Password Policy Enforcer enables admins to utilize advanced password policy controls like banning weak passwords and keyboard sequences for users' on-premises AD accounts and cloud accounts, including Microsoft 365 and Google ...Implement granular password policies for users in the same AD domain
When sensitive information needs to be protected, complying with stringent password policies becomes essential. The default AD domain password policy lacks the flexibility to enforce different rules for different users and does not provide sufficient ...Enforcing password history during password reset
In a world reeling under a large number of applications to make our life easier, it is a daunting task to remember the usernames and passwords for each and every application being used. Though administrators force users to change the passwords ...