How to enforce HTTPS by applying an SSL certificate in EventLog Analyzer
Objective
Learn how to enforce secure communication with EventLog Analyzer by configuring HTTPS. This is done by applying an SSL certificate and disabling HTTP access. HTTPS ensures encrypted data exchanges and aligns with security hardening best practices.
Prerequisites
- Ensure you have administrative access to EventLog Analyzer and a valid SSL certificate (e.g., CRT, CER, DER, P12, PEM, P7B, JKS, or PFX) and private key (KEY). If you would like to generate and apply a self-signed certificate from EventLog Analyzer
. - Optionally, a certificate chain file (CA-BUNDLE) might be required.
Steps to follow
To apply an SSL certificate:
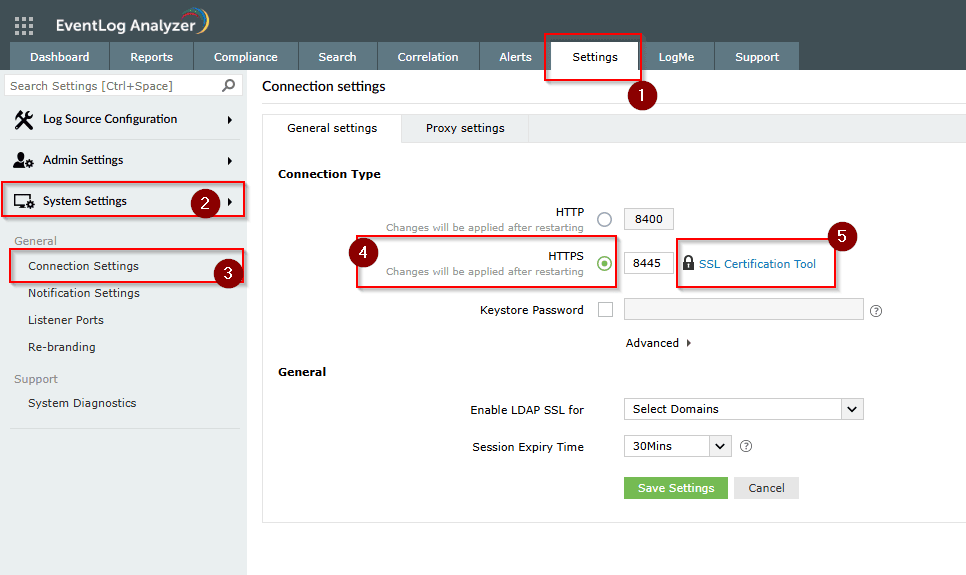
Step 1: Navigate to Settings > System Settings > Connection Settings.
Step 2: Select HTTPS . The default port is 8445, but you may change the port if required.
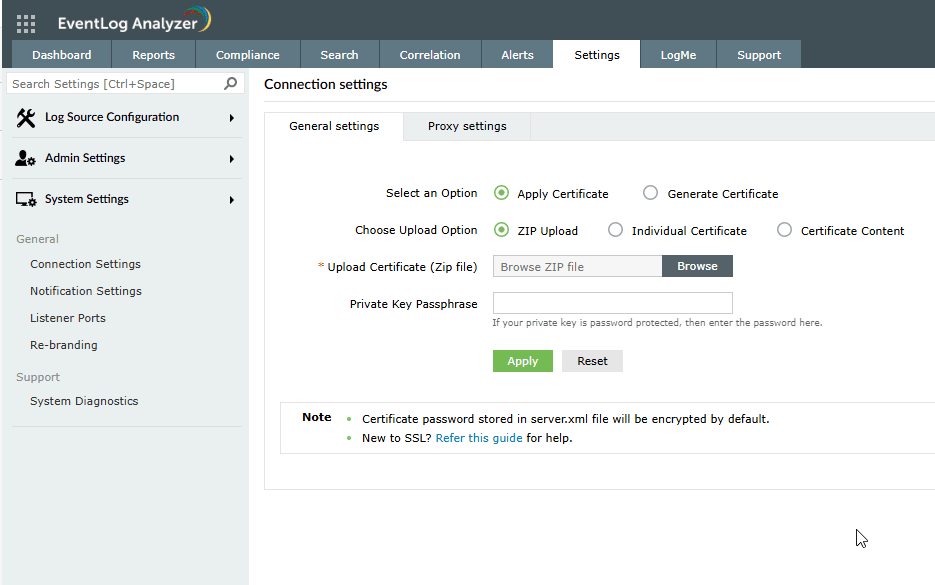
Step 3: Click SSL Certification Tool and:
- Upload the certificate file (a CRT or appropriate file).
- Upload the private key file (KEY) if required.
- Optionally upload the intermediate certificate bundle (if needed).
- If your certificate is password-protected, please enter the password in the Certificate Password field.
Step 4: Click Apply to confirm the changes.
Step 5: Restart the EventLog Analyzer service for the HTTPS configuration to take effect.
Step 6: Once it's restarted, access EventLog Analyzer using https://<server-name>:<port>.
Tips
- Self-signed certificates:
- Can be used for testing or internal environments.
- Must be manually trusted or browsers will display a warning.
- Internal-CA-signed certificates:
- Are ideal for enterprise environments with an internal public key infrastructure.
- Require an internal certificate authority (CA) to be trusted by client systems.
- Public-CA-signed certificates:
- Are recommended for production.
- Are trusted by all major browsers automatically.
- Ensure the HTTPS port (8445 by default) is open on your firewall.
- Back up the existing SSL certificate and key before replacing them.
- Check certificates' expiration dates and set reminders for renewal.
Related topics and articles
New to ADSelfService Plus?
Related Articles
How to resolve missing padlock symbol after applying a self-signed SSL certificate in EventLog Analyzer
Objective After applying an SSL certificate in EventLog Analyzer, users may still see a Not Secure warning in the browser and notice that the padlock symbol is missing. This typically occurs when the applied certificate is self-signed or not issued ...Applying a PFX certificate
Enable SSL in the GUI: Log in to EventLog Analyzer as an administrator. Go to Settings > System Settings > Connection Settings > General Settings. Enable SSL [HTTPS] and enter the desired web port number. The default web port used is 8445. Stop ...How to add Unix/Linux device in EventLog Analyzer
Objective EventLog Analyzer collects logs from Unix/Linux devices using the Syslog protocol. Devices can be configured automatically from EventLog Analyzer user interface or manually from the respective log source. This article explains both methods ...How to implement Security Hardening in EventLog Analyzer
Objective Improve the overall safety of your EventLog Analyzer setup by enabling key security settings that protect access, data, and system behavior. All of these settings can be managed easily from one place: the Security Hardening dashboard. ...How to Disable TLS 1.0 and 1.1 and enforce TLSv1.2 in in EventLog Analyzer
Objective EventLog Analyzer offers predefined support for TLSv1, TLSv1.1 and TLSv1.2 by default to offer compatibility in connection. Disabling the deprecated protocols enhances security by ensuring that only secure transport layers (TLS 1.2 and ...