Configuring ACL
Configuring ACL (Access Control List)
An ACL in the context of network administration is a set of rules that control network traffic and limit access to networks and network resources based on predefined criteria. In DNS servers like ISC BIND, ACLs are used to define which clients (based on IP addresses or networks) are allowed or denied access to certain DNS services. Common uses of ACLs in DNS include:
- Restricting Query Access: Defining which clients are allowed to query the DNS server.
- Controlling Zone Transfers: Specifying which secondary servers are allowed to receive zone data from the primary server.
- Limiting Dynamic Updates: Controlling which clients can dynamically update DNS records, often used in conjunction with TSIG for secure DDNS.
ACLs allow for the implementation of security policies by controlling who can access the DNS server and what actions they can perform, which is critical for maintaining the integrity and security of the DNS infrastructure.
Managing ACL templates
ACL templates are predefined configurations that simplify the creation of Access Control Lists (ACLs) in various network services, including DNS and DHCP servers. An ACL template allows administrators to define a set of rules or criteria once and then apply them across multiple instances, reducing redundancy and potential for error in configurations.
Usage of ACL Templates
ACL templates are typically used in environments where the same access restrictions or permissions are needed across different zones, views, or services. Instead of defining the same ACL multiple times, a template is created once and then referenced wherever needed.
They can be applied gobally on the cluster level, within specific zones, views, or options.
Defining Named ACLs
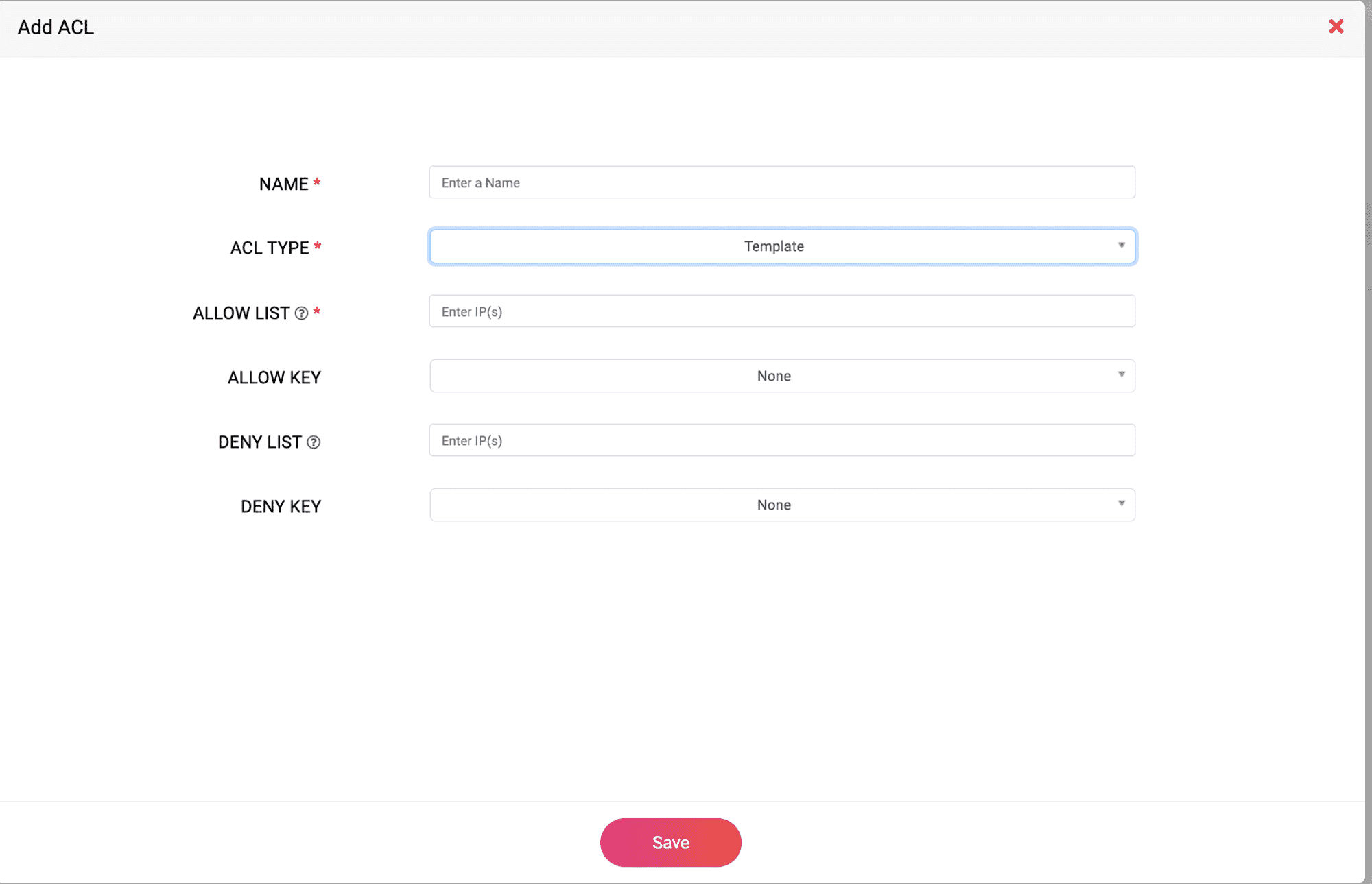
To create Named ACLs
- Go to DNS-> Config-> ACL
- Click on ADD ACL button on the right.
- You can choose the type of the ACL: ISC Format or Template based ACL.
- For the DDI Central template, just enter the IPv4/IPv6 addresses one by one in the allow and Deny lists.
- For the ISC format Follow the Example below: Here's an example of an ACL in ISC BIND format:
New to ADSelfService Plus?
Related Articles
Configuring ACL (Access Control List)
An ACL in the context of network administration is a set of rules that control network traffic and limit access to networks and network resources based on predefined criteria. In DNS servers like ISC BIND, ACLs are used to define which clients (based ...Configuring DNSSEC
DNSSEC DNSSEC, short for Domain Name System Security Extensions, is a suite of specifications for securing certain kinds of information provided by the Domain Name System (DNS). It is designed to protect against a range of DNS attacks such as cache ...Configuring the SMTP Host
Configuring the SMTP Host Setting up SMTP (Simple Mail Transfer Protocol) configurations is essential for enabling secure and reliable email communications within your network. With SMTP, you can specify how outgoing emails are sent from your ...Configuring TSIG keys
Configuring TSIG keys TSIG (Transaction Signature) TSIG is a security protocol used in the Domain Name System (DNS) to provide authenticated and secure communications between DNS servers and between DNS servers and clients. TSIG uses shared secret ...Configuring DNS client subnets
Configuring DNS Clientsubnets Client subnets in Microsoft DNS, are named groups of IP subnets that allow DNS servers to provide more specific responses based on the client’s location or network segment. A client subnet is identified by a name and ...