[ForYourInformation - 44] SAML In ServiceDesk Plus
Security Assertion Markup Language (SAML) is a means to exchange authorization and authentication information between services. SAML is a solution where the user logs into a service that acts as the single source of identity which then grants access to a subset of other internal services.
This post will be focused on providing an overview of SAML working from ServiceDesk Plus initiated login.
Few key terminologies :
An Identity Provider, frequently abbreviated as IdP, is the service that serves as the source of identity information and authentication decision. Identity providers authenticate principals and return identity information to service providers
Service providers, frequently abbreviated as SP, are the services that are requesting authentication and identity information about the principal(ServiceDesk Plus, Desktop Central, etc). Service providers take authentication responses received from identity providers and use that information to create and configure sessions.
SAML supports two different types of flows: those initiated by the service provider and those initiated by the identity provider.
In SP-initiated flows, you start out at the service provider ( ServiceDesk plus )and redirected to the identity provider to authenticate, and are then redirected back to the service provider.
Assertions are statements made by the identity provider about the principal. For example, the User’s Login Name or Login Name\Domain name. Assertions are used by the service provider to create and configure sessions for a principal.
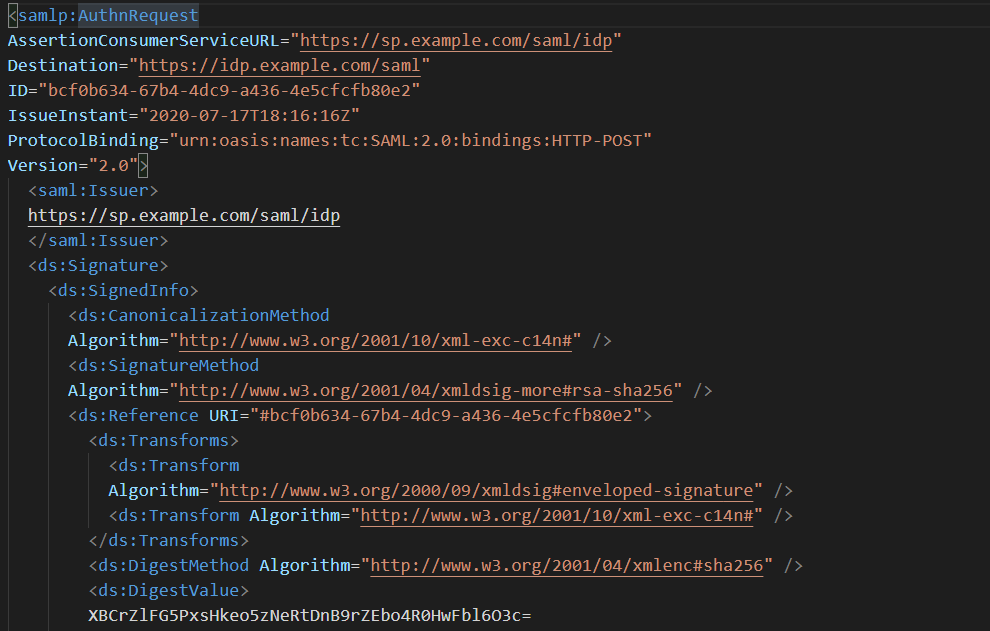
Authentication Request

To begin the login process, the User typically will navigate to the ServiceDesk Plus login page, and then click on a button that reads, “Login with SAML Single Sign ON.”
At this point an AuthenticationRequest is created as an XML document, serialize it (base64, compress, and URL encode), adds it as a query parameter to the URL, and redirect the user's browser to the identity provider’s login page.
As the name of the request implies, the service provider is requesting the identity provider to perform authentication on its behalf.
The AuthNRequest is often sent using HTTP Redirect Binding and ends up looking something like the following
Authentication Response
At this point, the user is sitting at the login page of the identity provider. If the user enters their correct login credentials, the identity provider will perform a 302 Redirect to the Assertion Consumer URL of the service provider ( mentioned under the SAML configuration page in SDP ) with the body containing the authentication response.
A simplified SAMLResponse would look like the following:
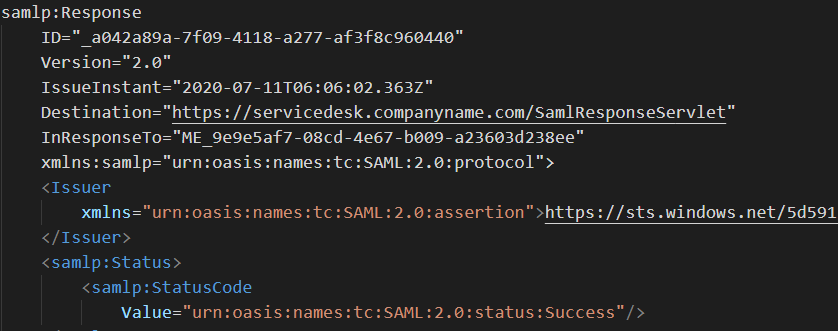
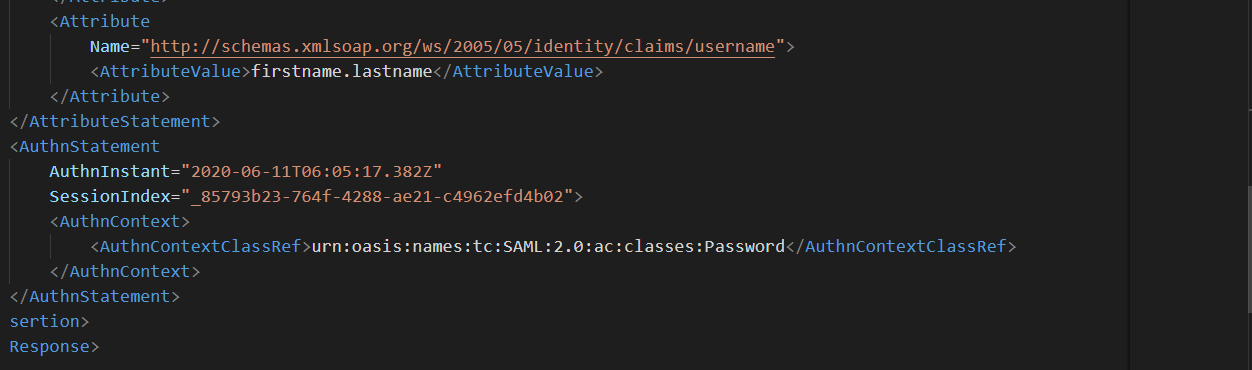
When a service provider receives an authentication response, it should first check if the InResponse To attribute references an ID of an AuthNRequest that the service provider actually sent. In addition, the IssueInstant attribute should be used to scope the validity window of the response.
The response also contains tags: Status, Subject, Conditions, and AttributeStatement:
- The Status tag contains the authentication result: success or failure.
- The Subject tag identifies the user that is just authenticated. As seen the
- This login name is generated based on the NameID attribute configured in the IDP. NameID tag contains the LoginName or Username of the principal that authenticated
- ServiceDesk plus is configured to use transient name id-format. It is the format that is being sent in the samlAuthNRequest i.e the initial request sent from ServiceDesk plus to your IdP in ServiceDesk Plus initiated login
- The Conditions tag defines constraints on the assertions, for example, the NotBefore and NotOnOrAfter attributes define the time duration that the assertions are valid. This prevents a malicious actor from recording a valid authentication response and then replaying at a later time (perhaps after the principal's account has been removed).
- The AttributeStatement tag contains assertions that the identity provider is making about the principal. Assertions typically contain information like group membership within an organization, allowed logins, or any other.
Interested to know more about how to read the SAML traces?
The login name in the SAML response from the IDP is generated based on the NameID attribute configured in the IDP. ServiceDesk plus will not be able to map this with the existing user's credentials if the login name in ServiceDesk Plus is not the same as the login name in the SAML response.
Also, if the user is associated with a domain in ServiceDesk plus, the IdP should return the domain name of the user along with the login name.
For example, if Peter is a technician with a login name peter in the Zylker domain, then the IdP should return zylker\peter as the login name.
Traces in SAML Response from IDP :
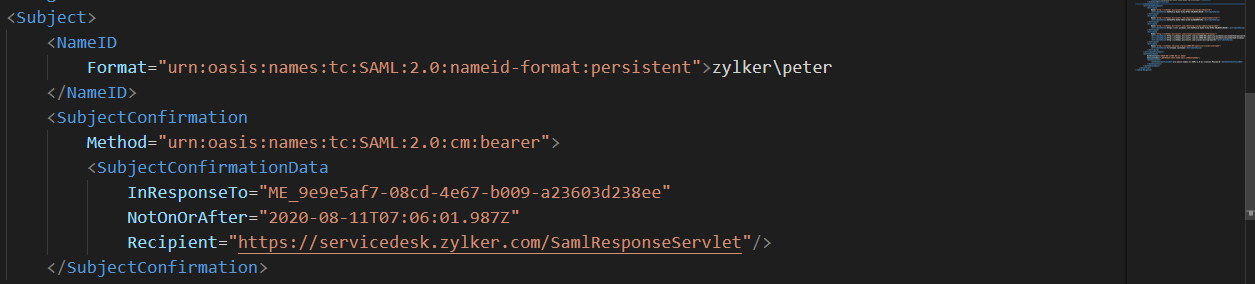
If the above case fails then,
- If dynamic user addition is enabled in ServiceDesk plus, the user will be added as a new user with the login name generated by the IdP and password as configured in the Active Directory/LDAP settings.
- If dynamic user addition is disabled, an error message will be displayed and the user will not be able to log in to ServiceDesk Plus.
To resolve this, reconfigure your IdP settings by choosing the right NameID attribute so that the Login name sent in the IDP response matches the Login name of the user in ServiceDesk plus.
Log Out Using SAML
ServiceDesk Plus supports SAML single logout service. Using this, you can choose to log out from ServiceDesk Plus only or from all the services integrated with the IdP.
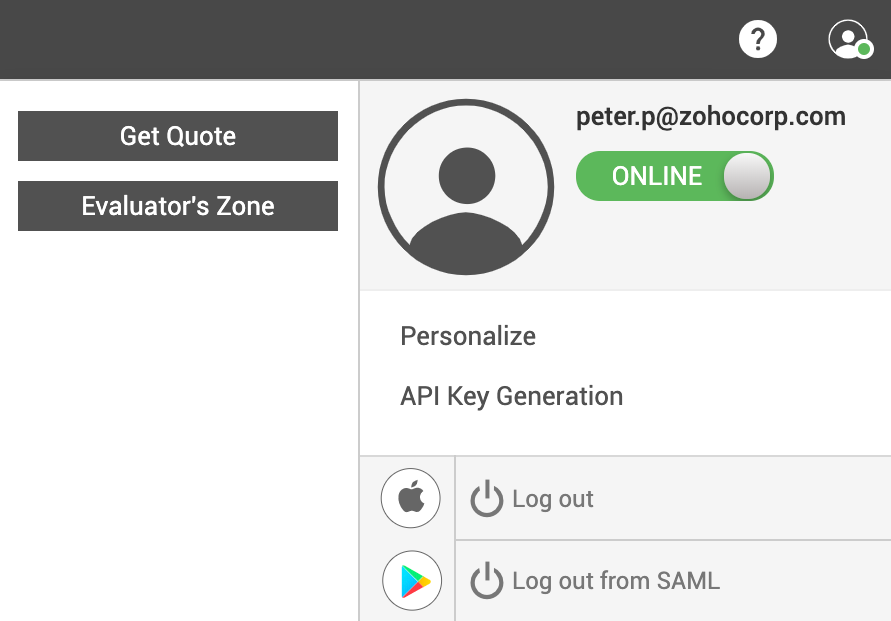
- Click.
- If you have configured SAML log out in your IdP domain, you will find two options listed.
- Click Log out to log out of ServiceDesk Plus application alone.
- If you click Log Out of SAML, you will be logged out of all the services integrated with the IdP.
Tip !!
Should there be any need to Hide this "LOGOUT FROM SAML" option, Page scripts in ServiceDesk plus can help :
Here are the details and the script
Go to Admin ► General Settings ► Page Scripts and use the following script:
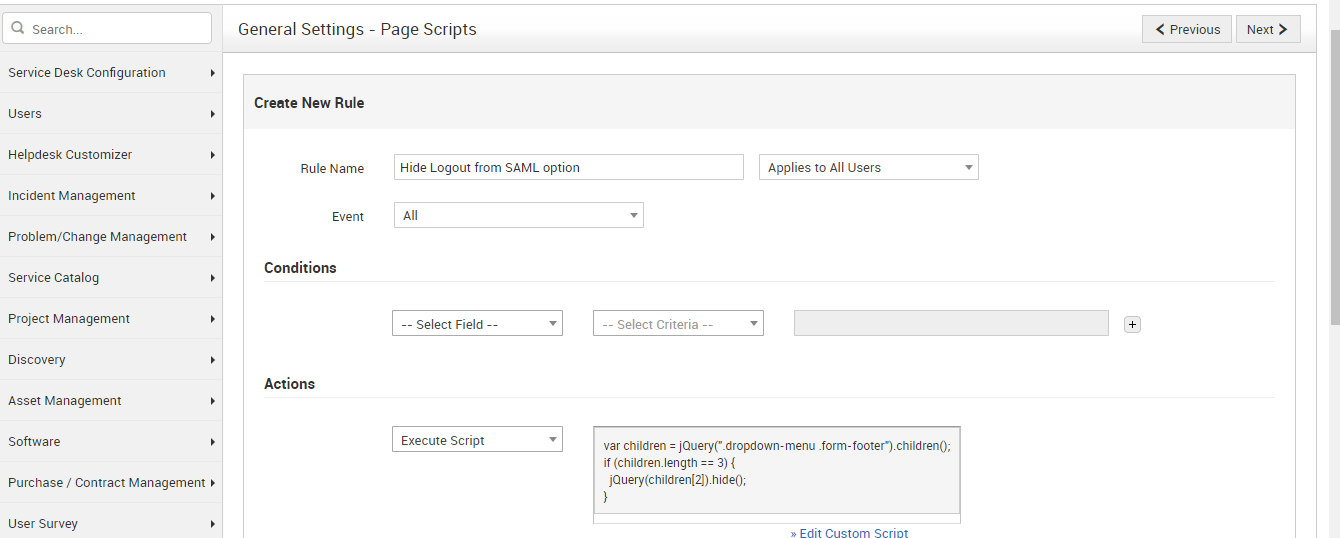
var children = jQuery(".dropdown-menu .form-footer").children();
if (children.length == 3) {
jQuery(children[2]).hide();
}
if (children.length == 3) {
jQuery(children[2]).hide();
}
This must hide the option "Log out from SAML" for the users.
If you run into any other questions while configuring SAML login in ServiceDesk plus- take a quick look :
Thank you for your time, I hope you find this article helpful.
Our previous article was on - Rich Text Support For Task And Worklog Description