Configuring RADIUS authentication for Active Directory-based actions
Traditional logins to resources on an organizational network involve only a username and password. However, if all the data breaches in recent years teach us anything, it is that they are not sufficient. Multi-factor authentication (MFA) has become an indispensable part of logins and implementing it is mandatory to meet regulatory standards such as the GDPR and the HIPAA. RADIUS or Remote Authentication Dial-In User Service is one of the methods that can be used for MFA.
When RADIUS is used for MFA, users first need to provide their username and password. They are then asked to enter the unique RADIUS password that is mapped to their account to authenticate themselves. If the password provided is valid, they will be allowed to access the service. Implementing MFA using RADIUS and other methods during Active Directory-based actions like domain logins, password changes, and self-service password resets and account unlocks can be extremely beneficial to domain user accounts and network security.
ADSelfService Plus, an identity management solution, offers RADIUS along with 20 other authentication methods including FIDO Passkeys, Biometric Authentication, and Zoho OneAuth TOTP, to secure users during:
- Active Directory self-service password reset or account unlock actions via the ADSelfService portal, ADSelfService Plus mobile app, and native Windows/macOS/Linux login screens.
- Windows, macOS, and Linux logins.
- Enterprise application logins through single sign-on (SSO).
- Self-update of Active Directory profile information, subscription to mail groups, and employee search using ADSelfService Plus.
Prerequisite steps:
- Log in to the RADIUS server.
- Log in to the RADIUS server.Navigate to the clients.conf file (default location:
/etc/raddb/clients.conf). - Add the following snippet in the clients.conf file:
- Restart the RADIUS server.
client <xyz> |
where,
<xyz> refers to the ADSelfService Plus server name.
<xxx.xxx.xxx.xxx> refers to the ADSelfService Plus server's IP address. and, <abc> refers to the secret key value created by the admin.
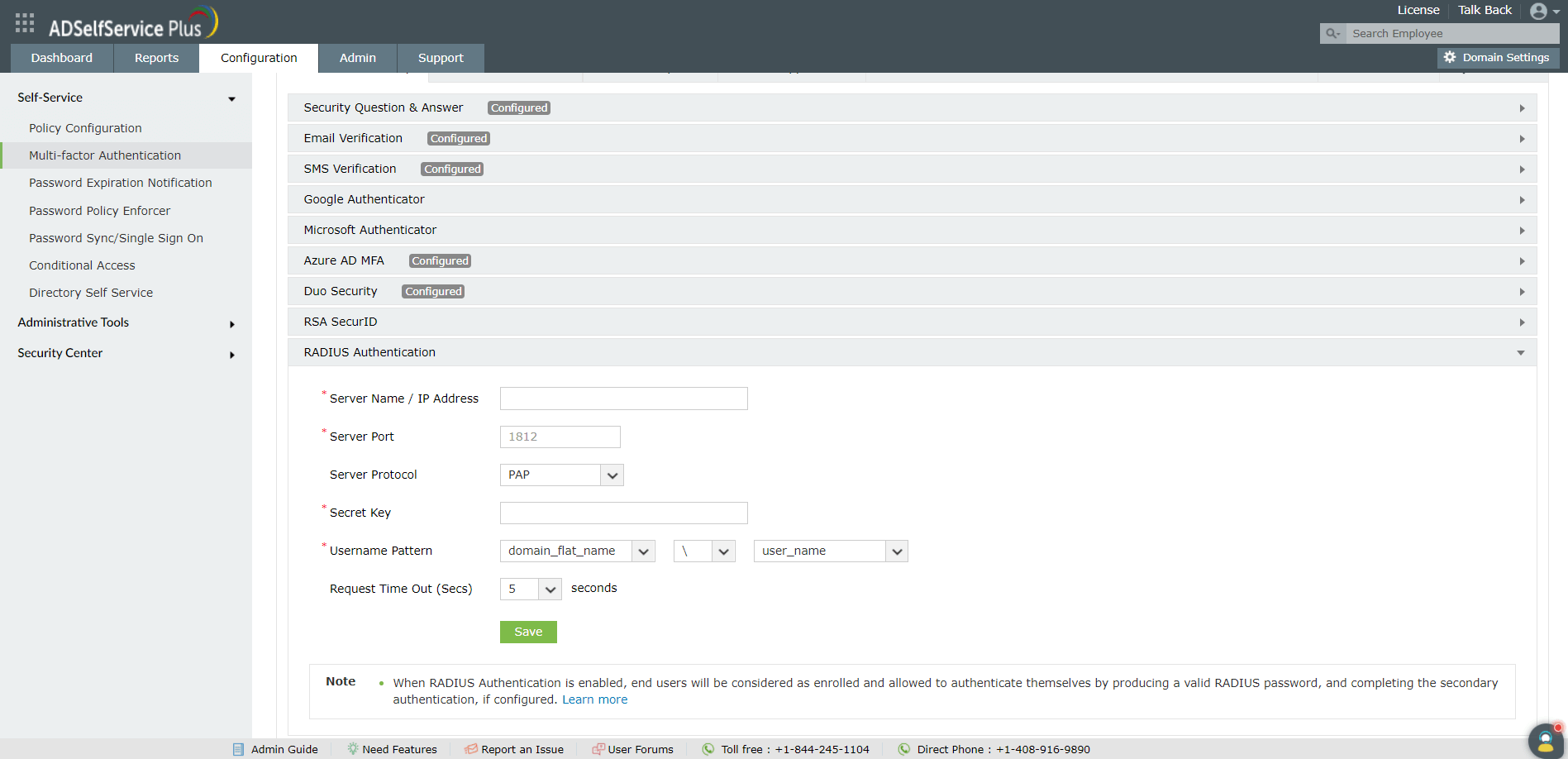
Configure ADSelfService Plus for RADIUS
- Navigate to Configuration > Self Service > Multi-Factor Authentication > Authenticators.
- From the Choose the Policy drop-down, select a policy.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- Click RADIUS Authentication section.
- Enter the Server Name, Server Port number, Server Protocol, Secret Key, Username Pattern, and the Request Time Out seconds.
- Click Save.
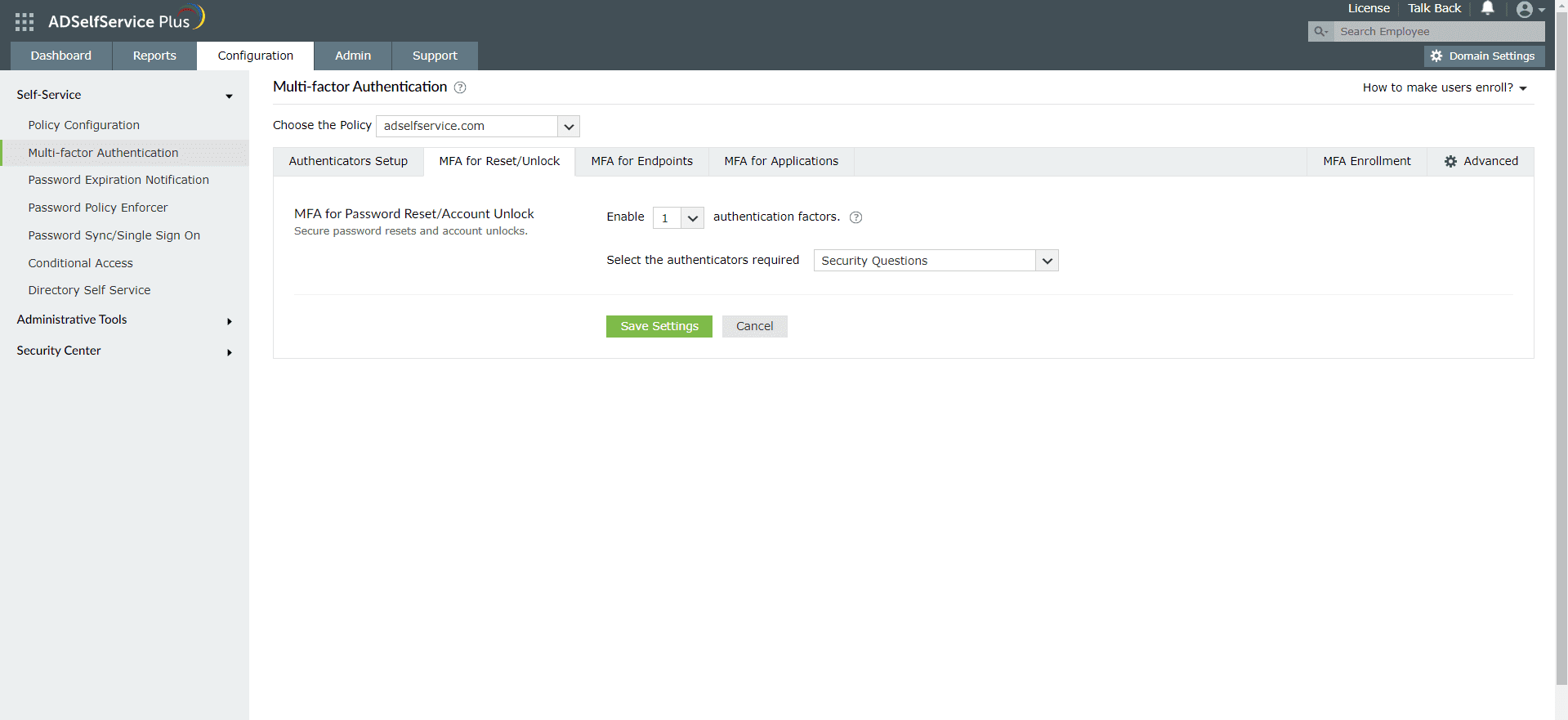
Enable RADIUS Authentication for Active Directory password resets
- Go to Configuration → Self-Service → Multi-factor Authentication → MFA for Reset/Unlock. In the MFA for Reset/Unlock section, enter the number of authentication factors to be enforced, and select Push Notification Authentication along with the other authentication techniques to be used.
- Click Save Settings.
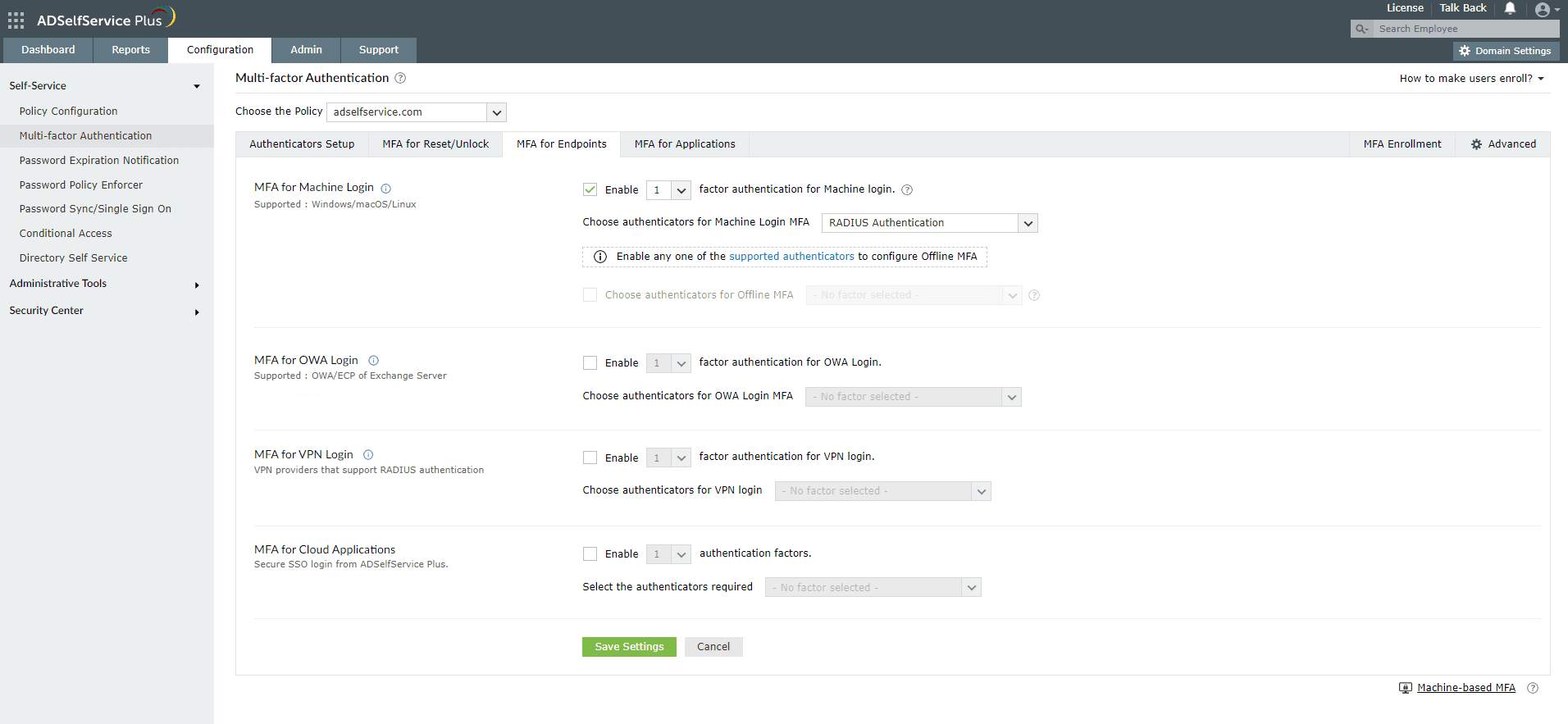
Enable push notification for Active Directory domain logins
- Go to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for which sets of users.
- In the MFA for Machine Login section, check the box to enable MFA for Machine Login and select the number of authentication factors to be prompted. Select the RADIUS Authentication and other required authenticators from the drop-down.
- Click Save Settings.
New to ADSelfService Plus?
Related Articles
Configuring QR code-based authentication for Active Directory-based actions
QR code-based authentication is a type of multi-factor authentication method that involves scanning a QR code with an app in order to verify one's identity. When authenticating into a service using MFA, users need to provide their account credentials ...Configuring TOTP authentication for Active Directory-based actions
Time-based one-time-password or TOTP is one of the most common methods used in multi-factor authentication (MFA). With this method, users are required to enter a passcode within a specific time from its generation. When users prove their identity in ...Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...Configuring MFA for Cisco ASA SSL VPN using RADIUS
This guide provides steps for enabling multi-factor authentication (MFA) using RADIUS for Cisco's Adaptive Security Appliance (ASA) product using ManageEngine ADSelfService Plus' MFA for VPN feature. To enable RADIUS-based authentication for VPN ...Configuring fingerprint authentication for Active Directory password resets and logins
Fingerprint authentication is an identity verification method that is widely used in recent times. The fact that everyone has a unique fingerprint makes it one of the more secure methods of authentication. Fingerprint authentication is also simple ...