Prerequisites to simulate Ransomware correlation rule in EventLog Analyzer
Prerequisites to simulate Ransomware correlation rule in EventLog Analyzer:
1) Ensure to add the target machine inside EventLog Analyzer(Product Configuration):
On adding a windows device, the default monitoring interval time is set to "10 minutes" for Windows devices. Execute the below steps to change the monitoring interval to "realtime".
Refer: How to change the monitoring interval? in the above link.
2) Enable the below audit polices and apply SACL on all the target machines(Environmental):
Pushing audit policies/SACL via GPO:
Steps to configure any advanced audit policy setting:
Setting an advanced audit policy requires administrator-level account permissions or the appropriate delegated permissions.
- From the Domain Controller, click Start, point to Administrative Tools, and then Group Policy Management.
- From the console tree, click the name of your forest > Domains > your domain, then right-click on the relevant Default Domain or Domain Controllers Policy (or create your own policy), and then click Edit.
- Under Computer Configuration, click Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policy, then double-click on the policy setting
"Object Access" -> Enable Success for the SubCategory "Audit File System"
"Detailed Tracking" -> Enable Success for the SubCategory "Audit Process Creation"
- Click on "Ok" to save the changes.
Force advanced audit policies
When using advanced audit policies, ensure that they are forced over legacy audit policies.
- Enable Force audit policy subcategory settings in <YourGPOPolicy>
- Navigate to Computer Configuration > Windows Settings > Security Settings > Local Polices > Security Options > Audit: Force audit policy subcategory settings (Windows Vista or later) to override the audit policy category settings.
Steps to configure Folder level auditing permissions:
- Go to Computer Configuration > Policies > Windows Settings >Security Settings and right-click File System> Add File. The ‘Add a file or folder’ dialog box will display.
- Locate the folder or file you want to assign permissions to and click on it. Now press OK.
- Click on "Advanced" -> "Auditing" -> Add -> Enable Create and Delete Permissions.
- Click on Ok -> Apply -> Ok.
Reference Screenshots: 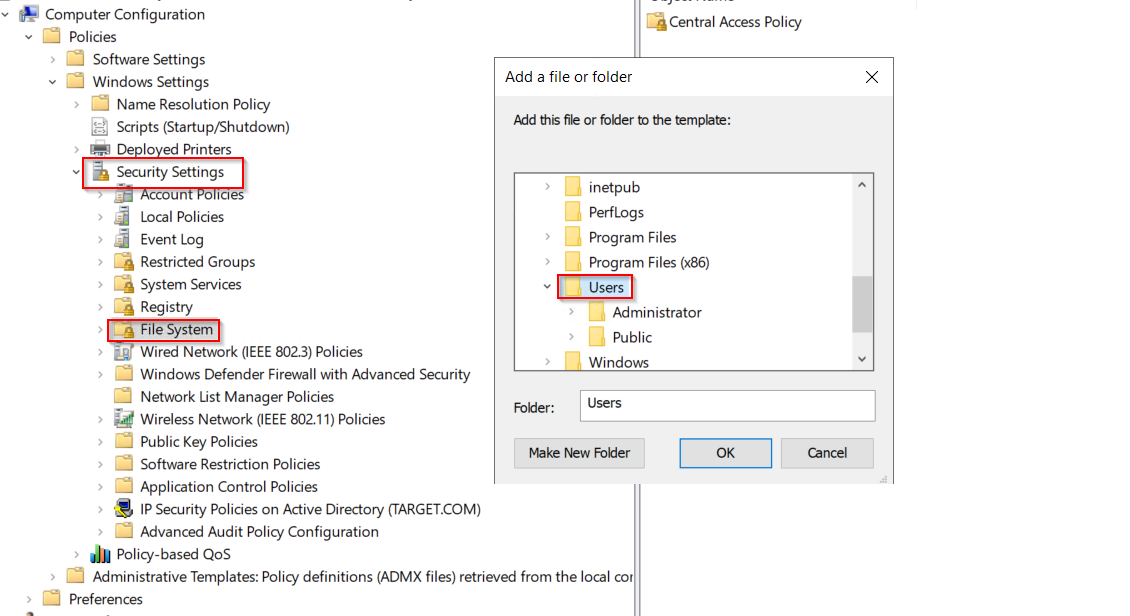
Security Filtering: To add the target machines for whom these policies/SACL needs to be pushed.
- Select the appropriate GPO which you have created and navigate to "Security Filtering". Under "Security Filtering", Click Add and Choose the Security group/computers to push the changes.
3) Please enforce the policy and check the target machine to confirm if the required policies are in place.
- On the target machine, open a cmdprompt with admin mode > type the below command to check the status,
auditpol /get /category:*
Check if the below highlighted audit policies are enabled:
Also, confirm if the required SACL's are in place. Manually access the folder's properties -> Advanced -> Auditing to confirm the same,
Permissions Enabled: Create / Delete Function
4) If point 3 is true, then whenever there's a ransomware pattern created, the relevant logs from Event viewer will be captured by EventLog Analyzer to trigger an alert or notification.
(Docx and PDF file attached)
Reference Ticket ID: #6666173
Note: We got confirmation from the client that the steps were implemented successfully.
New to ADSelfService Plus?
Related Articles
Troubleshooting: Disk space issues in EventLog Analyzer
Issue description EventLog Analyzer server might run out of storage due to misconfiguration and other known factors. This article offers troubleshooting steps to resolve when your disk or drive where the application is installed is full and help you ...How to perform Veeam auditing in EventLog Analyzer
Objective Veeam is a data protection and disaster recovery solution designed for modern IT environments. ManageEngine EventLog Analyzer offers Veeam extension for which is designed to enable seamless integration of log data from Veeam Backup & ...Unable to start EventLog Analyzer
Issue description This issue occurs when the EventLog Analyzer service fails to start, or when users are unable to access the web client through the browser (typically on ports 8400 or 8445). Users may experience one or more of the following ...How to increase the records per page in Eventlog Analyzer
Objective By default, EventLog Analyzer displays 10 records per page in the Reports section. While users can manually adjust this number, the change is temporary. This article will guide you through configuring a global rule so that all reports ...How to import custom threat feeds in EventLog Analyzer
Objective EventLog Analyzer provides an option to import custom threat feeds or indicators, allowing users to upload lists of malicious IP addresses, CIDR values, domains, and URLs as per internal investigation. These imported indicators are then ...