How to fight password theft using the multi-factor authentication techniques available in ADSelfService Plus
Issue: One of the main intrusion techniques used by hackers is password theft. In fact, stolen credentials ranked among the top 5 data breach action types in 2022.
Use case: Most organizations rely heavily on passwords to secure their network resources. However, users deal with their password saturated lives by often creating weak passwords and reusing them across critical business accounts. This makes stealing passwords the easiest way to get hold of network resources. Hackers only need to crack one user's password to enter an organization's network and cause havoc.
Solution: ADSelfService Plus makes stolen passwords ineffective by mandating a additional layers of authentication (MFA) for
- Windows, macOS, and Linux OS remote access.
- Windows, macOS, and Linux OS local access.
- Cloud application access.
The solution supports upto 19 methods for MFA including Fingerprint or Face ID Authentication, YubiKey Authentication, Google Authenticator, Microsoft Authenticator, and Azure AD MFA. Click here to get the complete list of authenticators.
Prerequisites for enabling Windows/macOS/Linux OS MFA
- Your ADSelfService Plus license must include Endpoint MFA. Visit the store to purchase it.
- SSL and TFA must be enabled in ADSelfService Plus.
- The Windows and macOS logon agents, which come bundled with ADSelfService Plus, must be installed through the GINA/Mac/Linux Installation option available in the admin console.
- The authentication techniques you'd like to enforce for users to prove their identity need to be configured in ADSelfService Plus.
Steps involved:
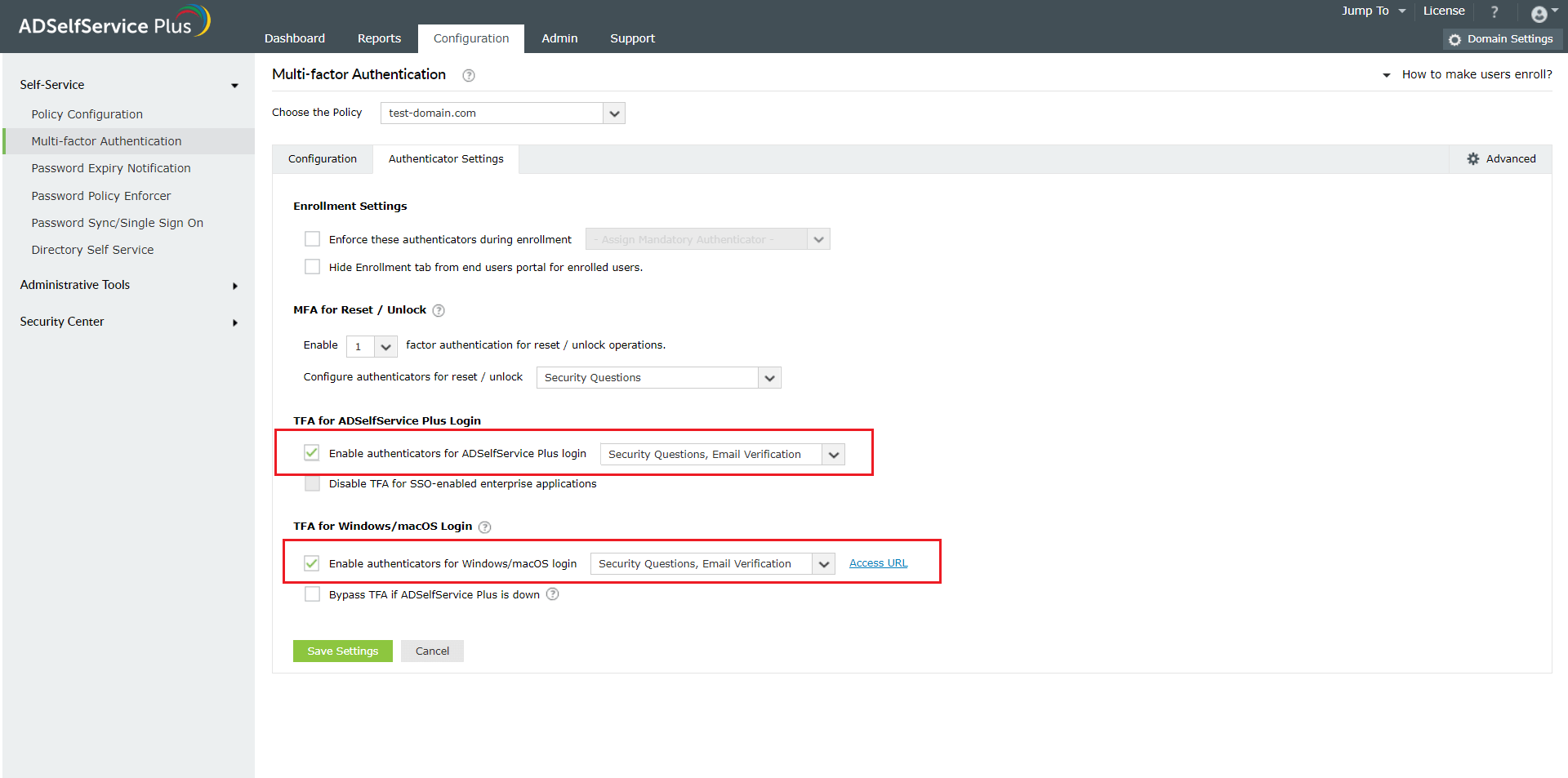
- Navigate to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints > MFA for Machine Logins.
- Choose the Policy from the drop-down.Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. Select at least one self-service feature. Finally, click Save Policy.
- Enable the Select the authenticators required checkbox.
- Use the Enable _ authentication factors option next to MFA for Machine Login to select the number of authenticators.
- Select RSA SecurID and other necessary configured authenticators from the drop-down.
- Click Save Settings.
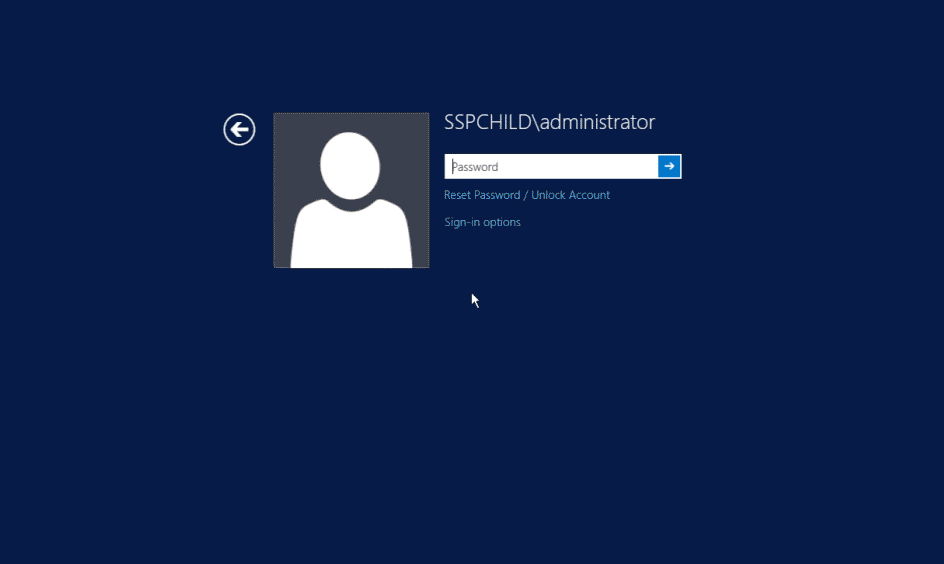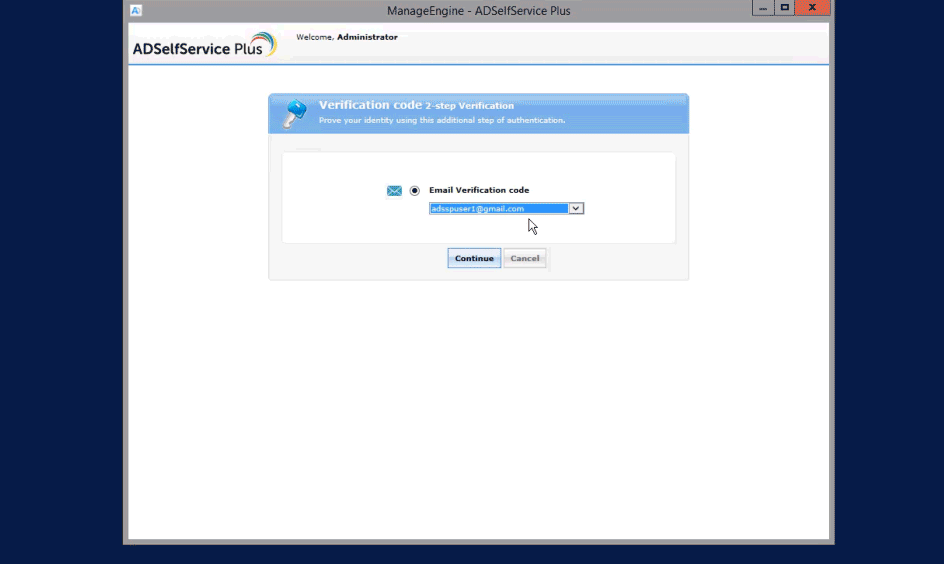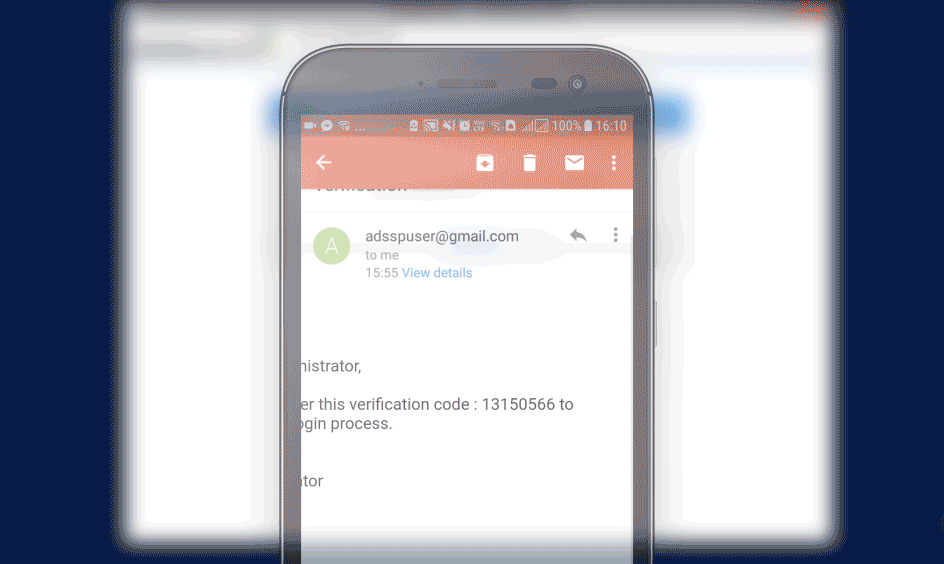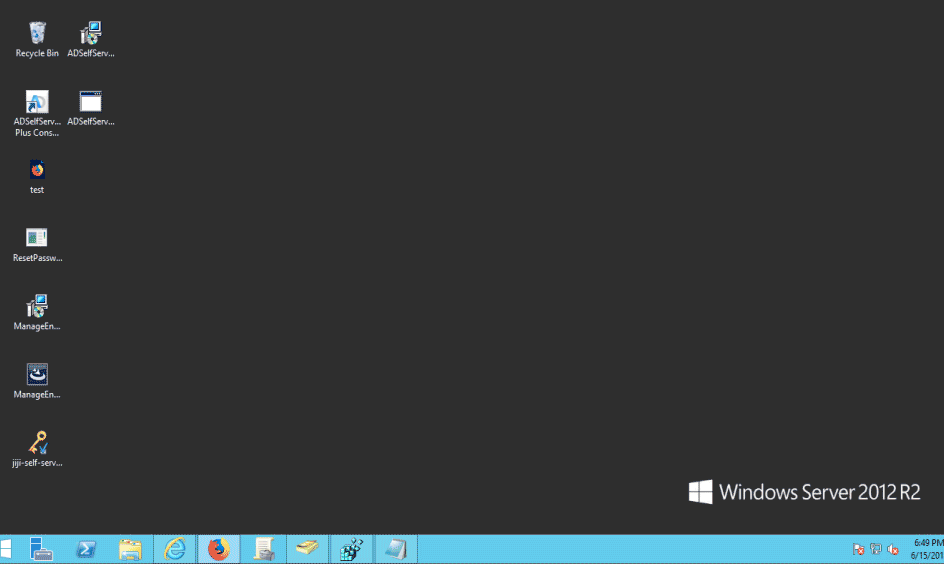
To enforce MFA for Windows/macOS/Linux logons logons
- In the Endpoint MFA section, click the select the second authenticator option, and mandate the authenticator of your choice from the drop-down.
To enforce 2FA for SAML-enabled cloud applications
- Navigate to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints > MFA for Cloud Applications Login.
- Choose the Policy from the drop-down.
- Check the box next to Enable authenticators, enter the number of authentication methods to be enforced and select the authentication methods from the drop-down.
- Select Save Settings.
New to ADSelfService Plus?
Related Articles
Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...How to enable smart card authentication in ADSelfService Plus?
ADSelfService Plus supports smart card authentication which enables users to access the self-service portal securely, without having to enter a password. If your organization already utilizes smart cards, PKI, or certificates as an authentication ...How to enable Partial Enrollment for Active Directory users in ADSelfService Plus
Active Directory domain users need to complete enrollment with ADSelfService Plus before they can use the below listed features: Self-service password reset Self-service account unlock Endpoint multi-factor authentication ADSelfService Plus' logon ...How to enable multi-factor authentication for RDP
Generally, remote employees use Microsoft Remote Desktop Protocol (RDP) to connect to their work devices from an external network, using only a password to authenticate their devices. This makes RDP-based access highly vulnerable to password-based ...How to disallow palindrome passwords using ADSelfService Plus
Having a secure password is of paramount importance to ensure the safety of your network. A password's strength depends on the length of the password, the different types of characters used, the number of repeated characters, the sequence of ...