How to enable force enrollment of users based on their OU(s) and group(s) using login script in ADSelfService Plus?
Solution
The Force Enrollment using Login Script feature of ADSelfService Plus allows you to forcefully enroll the un-enrolled users with a login script. You can schedule the execution of a login script to enable force enrollment. Only after the enrollment, users can access other resources in their machine.
This feature also provides you with the ability to decide whether users of the entire domain or that of a selected organisational unit(s) and group(s) would be forced to enroll. This means, with this feature you can craft a strong deployment policy that fits your requirements to a T.
Steps involved:
- Login to ADSelfService Plus web console with admin credentials.
- Navigate to Configuration tab → Administrative Tools → Quick Enrollment → Force Enrollment using Logon Script.
- Enter the Scheduler Name and the Description.
- Enable this scheduler only for select organizational units (OUs) and groups by selecting a policy from the Select Policy drop-down list.Note: To create or edit a policy, navigate to the Configuration tab → Self-Service → Policy Configuration. You can either create a new self-service policy by clicking the +Add New Policy button, or edit the existing default policy. For detailed steps, click here.
- Enter the Window Title and Window Content.
- Enter the text you want to be displayed in the Enrollment Button. Example: Enroll Now.
- Select the Cancellation Button checkbox if you want one in the pop-up, and enter the text you want to be displayed in it. Example: Remind me later.
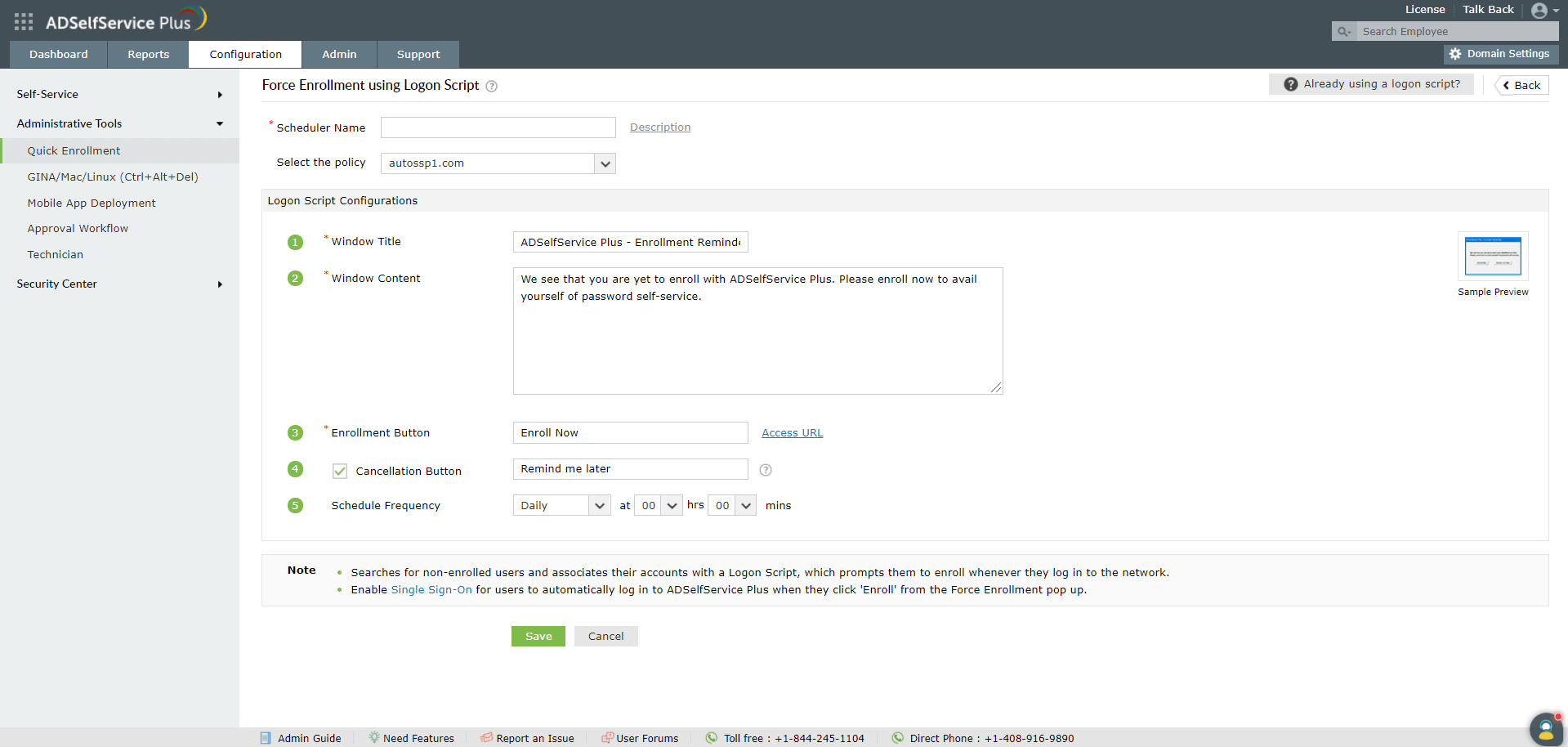
- Note: Click Access URL and enter the Server Name and the Port number in which ADSelfService Plus is running. This ensures that when a user tries to enroll, the right server is contacted for the operation.
- Schedule the frequency in which you want the script to run in the Schedule Frequency field (range: Hourly to Monthly).
- Click Save.
You have now successfully set up a scheduler which runs the login script and forces users to enroll if they have not already.
New to ADSelfService Plus?
Related Articles
How to enable Partial Enrollment for Active Directory users in ADSelfService Plus
Active Directory domain users need to complete enrollment with ADSelfService Plus before they can use the below listed features: Self-service password reset Self-service account unlock Endpoint multi-factor authentication ADSelfService Plus' logon ...How to enable offline MFA in ADSelfService Plus
ManageEngine ADSelfService Plus supports offline multi-factor authentication (MFA) for Windows machine logins, User Account Control (UAC) prompt elevation, and Remote Desktop Protocol (RDP) server authentication when the product server is ...Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...How to reset forgotten Windows passwords from the login screen using ADSelfService Plus
Empowering users with a Windows password reset tool According to recent research, organizations are spending close to one million dollars annually on resolving password-related tickets. This isn’t that surprising, as the Microsoft-approved methods to ...How to automatically enroll new users for self-password reset with CSV files?
With a multitude of users, ensuring them to enroll for password expiry notifications can be a cumbersome process. Despite the reminders, when the user fails to enroll, the administrator’s intervention becomes mandatory. With ADSelfService Plus' Auto ...