How to configure multi-factor authentication with RSA SecurID
Setting up RSA SecurID authentication
You can set up RSA SecurID as an authenticator in ADSelfService Plus in two steps:
- Include the ADSelfService Plus server in the SecurID SECURITY CONSOLE as an authentication agent.
- Configure ADSelfService Plus for RSA SecurID.
Prerequisites
- Ensure that you have installed a supported version of RSA Authentication Manager.
- For SDK integration: RSA Authentication Manager 8.0 or higher
- For REST API integration: RSA Authentication Manager 8.2 SP1 or higher
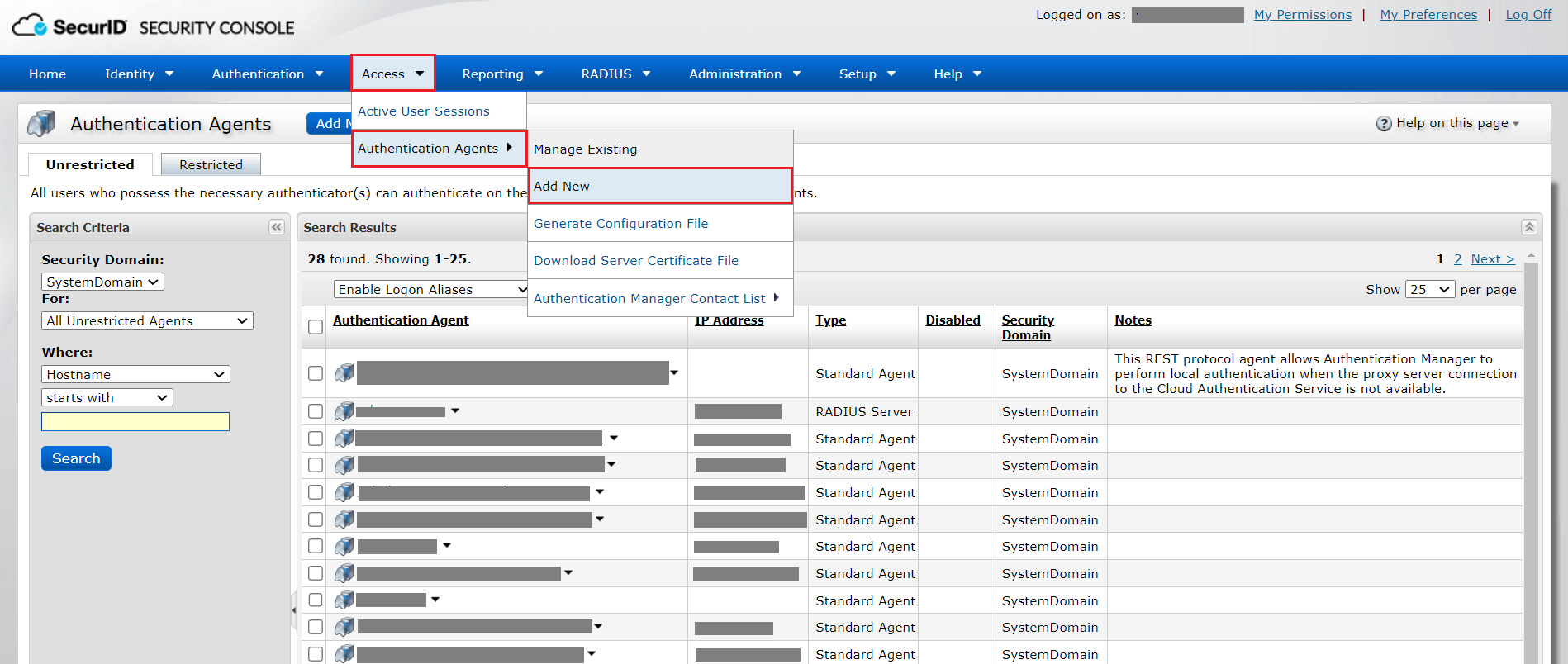
Including ADSelfService Plus as an authentication agent in the RSA SecurID SECURITY CONSOLE
- Log in to your RSA admin console (e.g., https://adssp-rsa.mydomain.com/sc ).
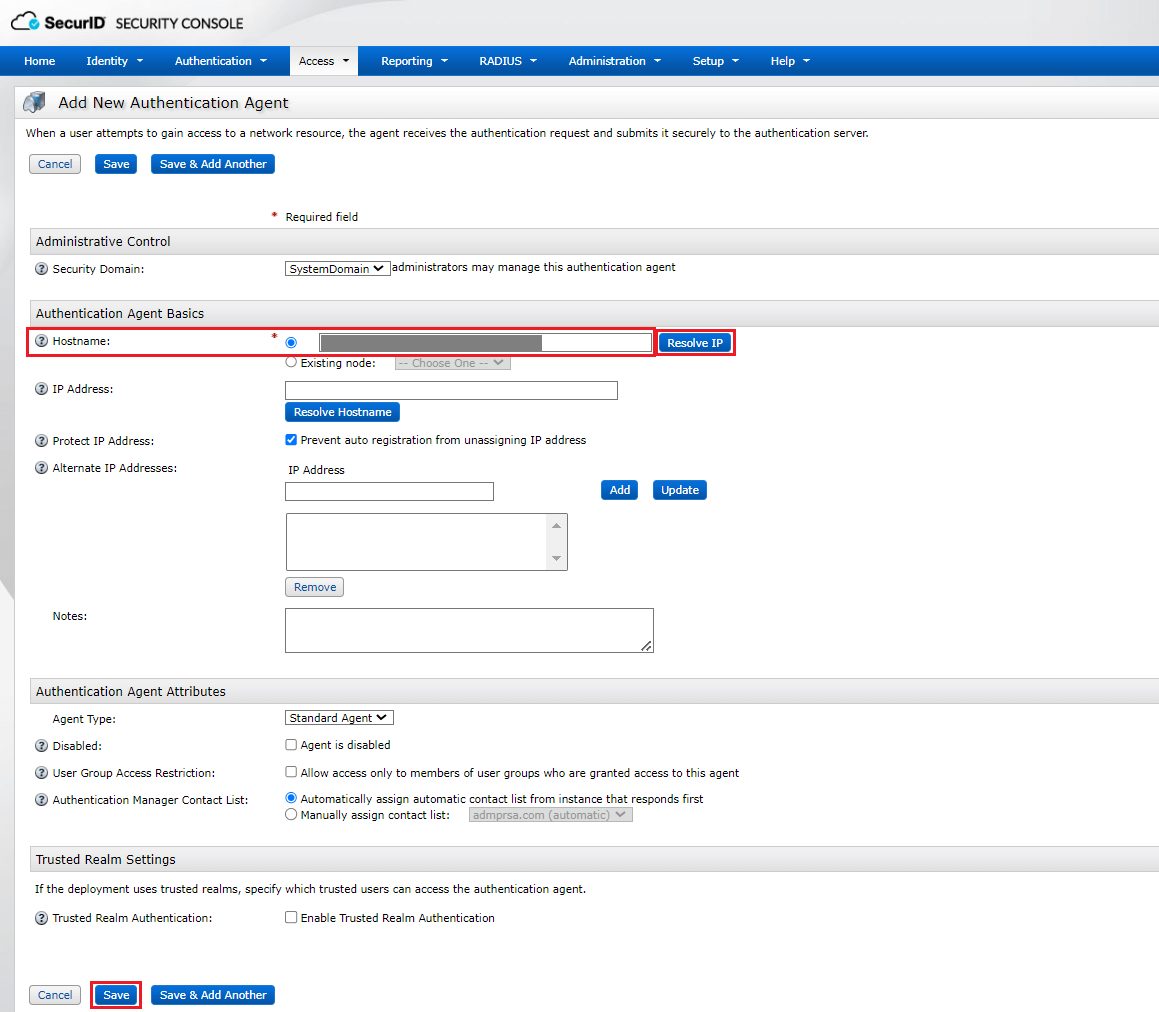
- Navigate to Access > Authentication Agents. Click Add New.
- Enter the hostname of the ADSelfService Plus server in the Hostname field and click Resolve IP to establish a connection between the SecurID SECURITY CONSOLE and the ADSelfService Plus server.
- Click Save to add the ADSelfService Plus server as an authentication agent.
Configuring ADSelfService Plus for RSA SecurID
RSA SecurID configuration can be done using either of these methods:
Note: It is recommended to configure RSA authentication using REST API as RSA SecurID no longer supports SDK Integration.
Steps to configure RSA SecurID with REST API integration
- Log into the RSA admin console and navigate to Setup > System Settings.
- Under Authentication Settings, click RSA SecurID Authentication API.
- Copy the Access ID, Access Key, and Communication Port details.
- Log into the ADSelfService Plus admin console and navigate to Admin > Configuration > Self-Service > Multi-factor Authentication > RSA SecurID.
- From the Choose the Policy drop-down, select a policy.
- Click RSA SecurID.
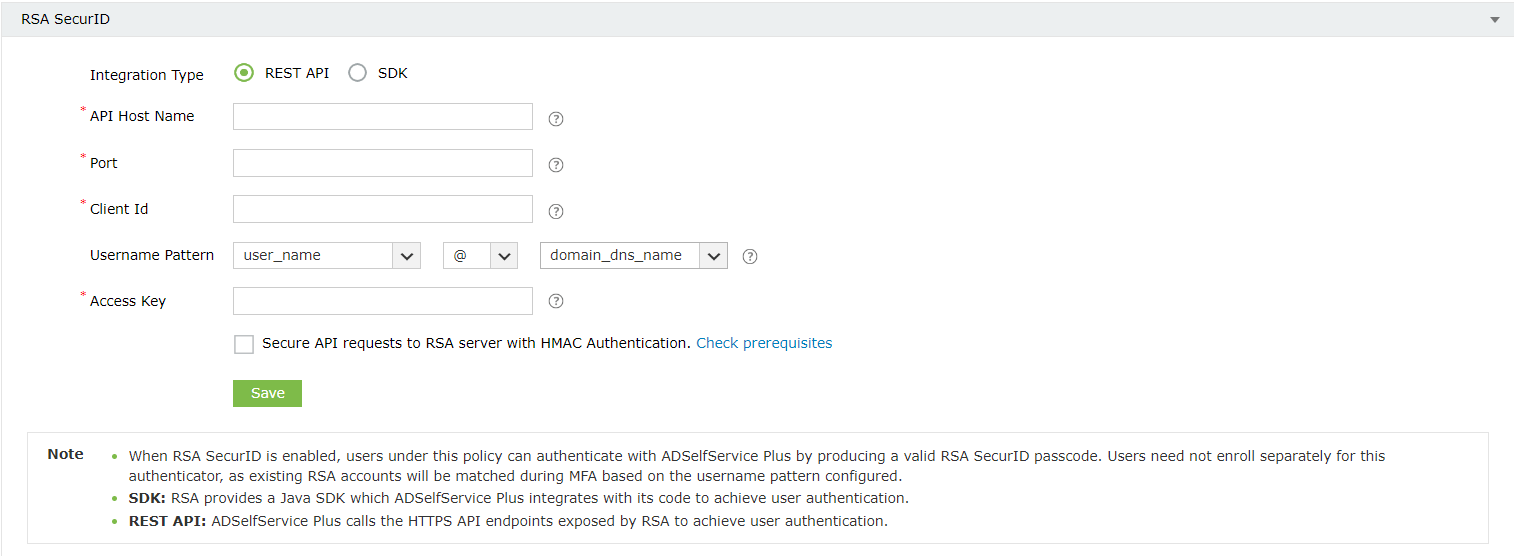
- For Integration Type, select REST API.
- Enter the hostname of RSA Authentication Manager in the API Host Name field.
- Paste the port number and access key obtained in Step 3 in the Port and Access Key fields, respectively.
- Enter the authentication agent's name (i.e., the hostname or access URL of the ADSelfService Plus server) in the Client Id field.
- Check the Secure API requests to RSA server with HMAC Authentication box to verify the integrity of the authentication requests. Please follow the steps mentioned under HMAC prerequisites before enabling HMAC authentication.
- Enter the access ID copied in Step 3, in the Access Id field.
- Select a Username Pattern that matches the User Account Format in the RSA admin console.
- Click Test Connection and Save.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration > Self-Service > Policy Configuration > Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
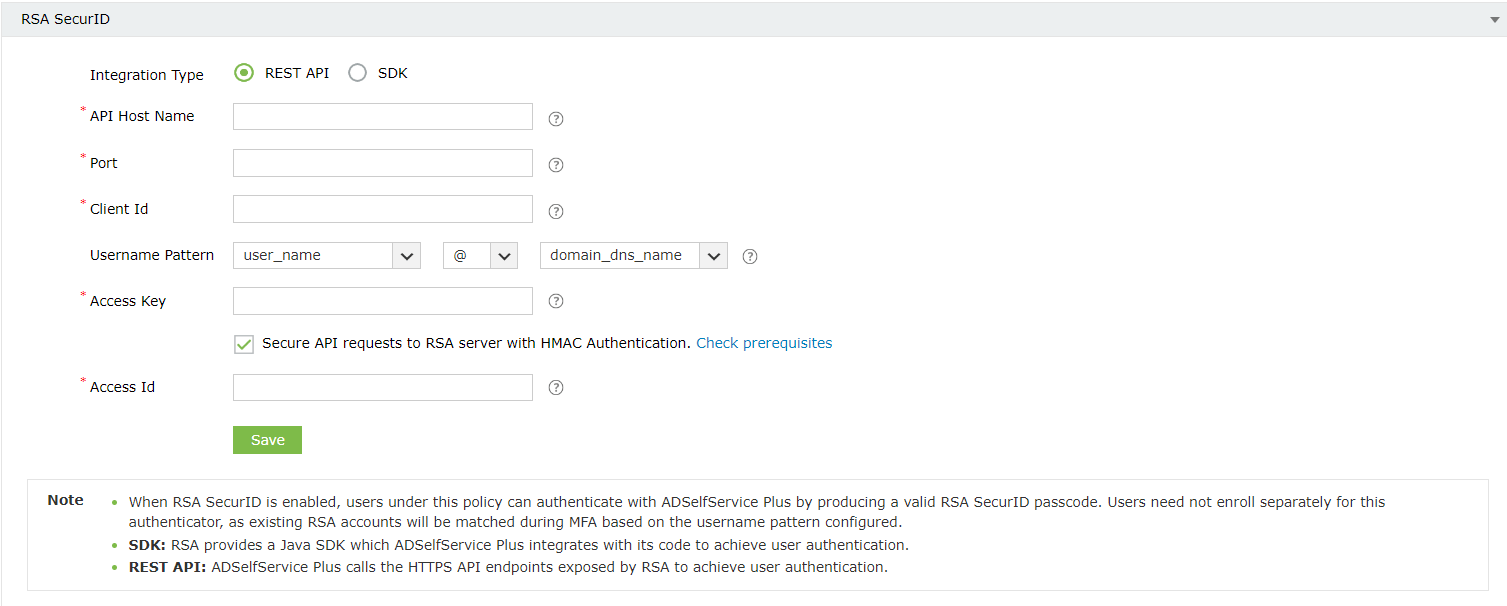
Note: Users across different domains can have the same username, causing ambiguity during RSA mapping. To ensure secure authentication, we strongly recommend using a username pattern that includes the domain. This Username Pattern needs to match the RSA User Account Format in the RSA admin console, to accurately map domain user accounts to RSA user accounts.
Steps to configure RSA SecurID with SDK integration
- Ensure that the required JAR files listed below are present in the <ADSelfService_Plus_install_directory>/lib folder.
- authapi-8.6.jar
- log4j-1.2.12rsa-1.jar
- cryptojcommon-6.1.3.3.jar
- jcmFIPS-6.1.3.3.jar
- cryptojce-6.1.3.3.jar
- In the RSA admin console, navigate to Access > Authentication Agents > Generate Configuration File.
- Click Generate Config File to download the AM_Config.zip file.
- Extract the sdconf.rec file from the ZIP file.
- Log into the ADSelfService Plus admin portal and navigate to Admin > Configuration > Self-Service > Multi-factor Authentication > Authenticators Setup > RSA SecurID.
- From the Choose the Policy drop-down, select a policy.
- Click RSA SecurID.
- For Integration Type, select SDK.
- Click Browse and select the sdconf.rec file downloaded from the SecurID SECURITY CONSOLE.
- Select a Username Pattern that matches the User Account Format in the RSA admin console.
- Click Save.
Note: These JAR files pertain to the latest version of Authentication Agent SDK for Java (version 8.6). If they are not present in the <ADSelfService_Plus_install_directory>/lib folder, please download them from RSA Community.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration > Self-Service > Policy Configuration > Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
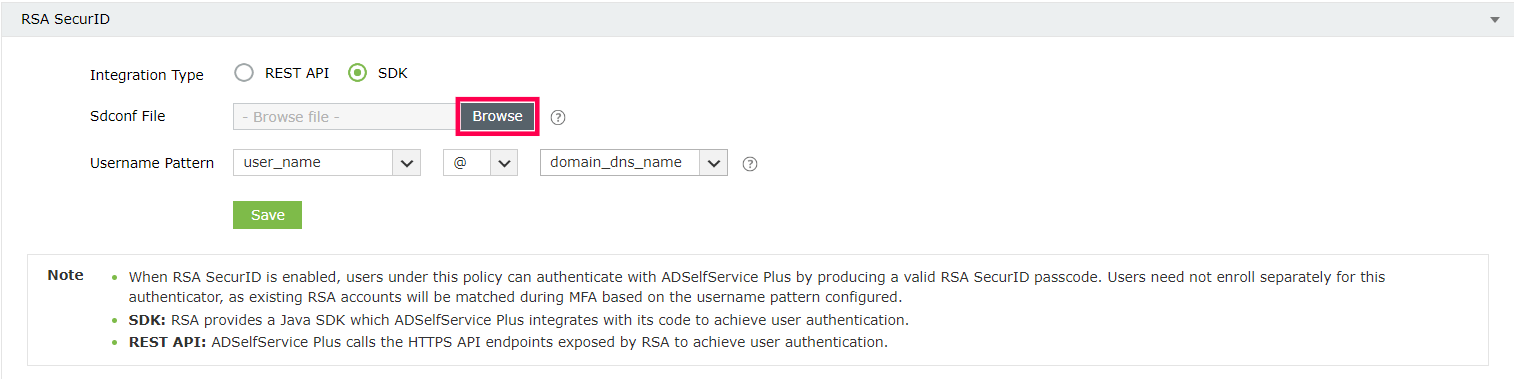
Note: Users across different domains can have the same username, causing ambiguity while matching RSA accounts to ADSelfService Plus user accounts during MFA. To ensure secure authentication, we strongly recommend using a Username Pattern that includes the domain name (domain_dns_name) or email (email_id) to accurately map domain user accounts to RSA User Accounts, which need to be in the same format. Utilizing only the username (user_name) in the Username Pattern is discouraged for security reasons.
Once enabled, users belonging to the policy for which RSA authentication has been enabled will be asked to verify their identity with their SecurID tokens while logging in.
Note:Please ensure that all the users are associated with the configured authentication agent (the ADSelfService Plus server) and have enrolled in RSA Authentication Manager with the same username and SecurID tokens assigned to them.
If you experience problems while authenticating via RSA, log in to your RSA admin console and go to the Reporting tab. Under Real-time Activity Monitors, go to Authentication Activity Monitor > Start Monitor to troubleshoot.
HMAC prerequisites
Hash-based message authentication code (HMAC) is used to validate the authentication requests that are exchanged between authentication agents and the RSA SecurID Authentication API.
- Log on to the appliance with the Secure Shell client or access the appliance on a virtual machine with the VMware vSphere Client, Hyper-V Virtual Machine Manager, or Hyper-V Manager.
- To verify authentication requests by implementing HMAC, type the following:
- ./rsautil store –a update_config
- auth_manager.rest_service.authorization.mode 1 GLOBAL 501
- To use only the RSA SecurID Authentication API's access key for authentication, type the following:
- ./rsautil store –a update_config
- auth_manager.rest_service.authorization.mode 0 GLOBAL 501
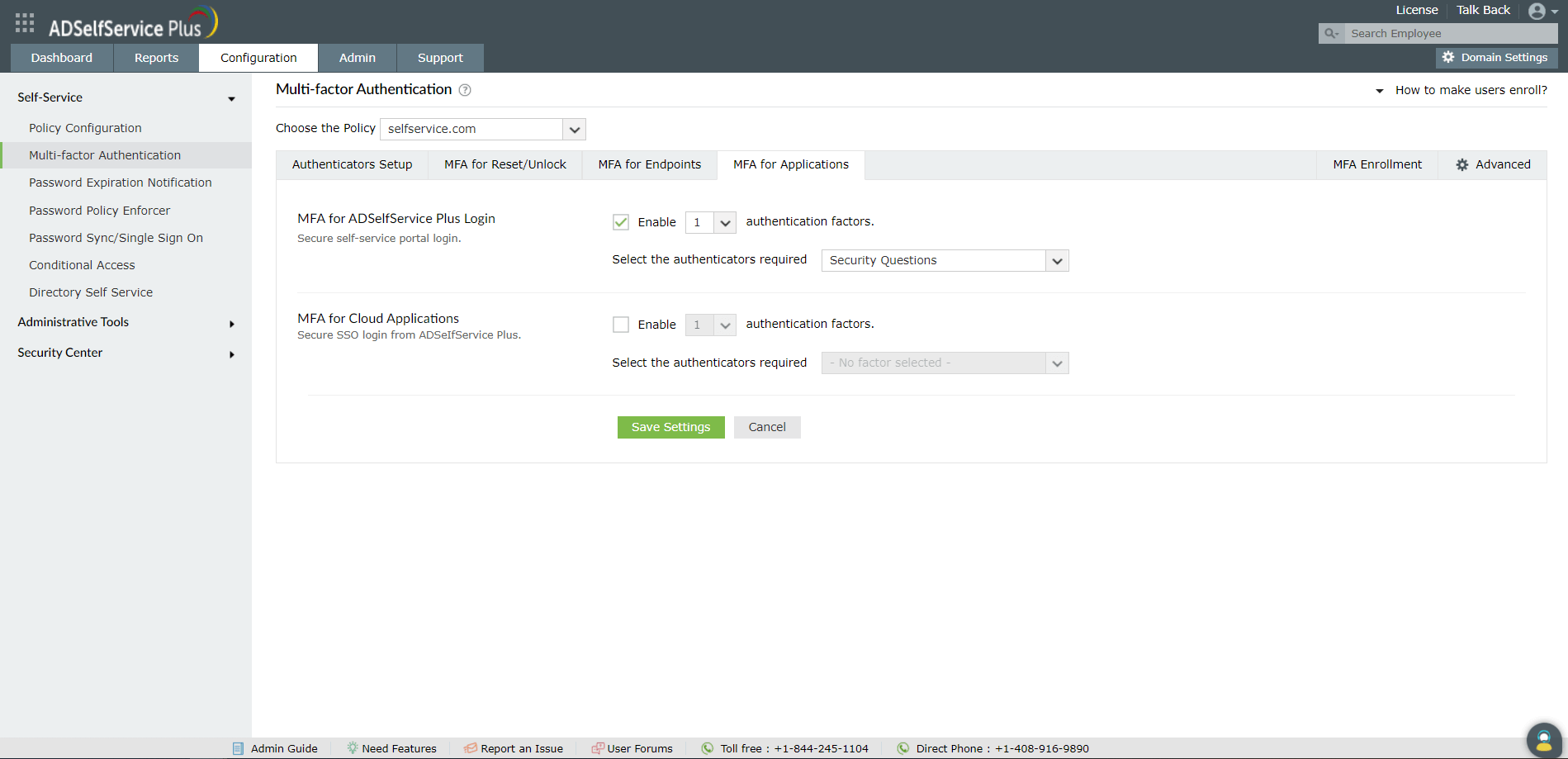
Steps to enable multi-factor authentication for ADSelfService Plus' end-user portal login
- Navigate to Configuration → Self-Service → Multi-factor Authentication → MFA for Reset/Unlock.
- Choose the Policy from the drop-down.Note: ADSelfService Plus allows you to create OU- and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- Use the Enable _ authentication factors option next to MFA for ADSelfService Plus Login,
- Select RSA SecurID and other necessary authenticators from the Select the authenticators required drop-down.
- Click Save Settings.
Once configured, RSA SecurID will be one of the authenticators that verifies a user's identity when they login to ADSelfService Plus.
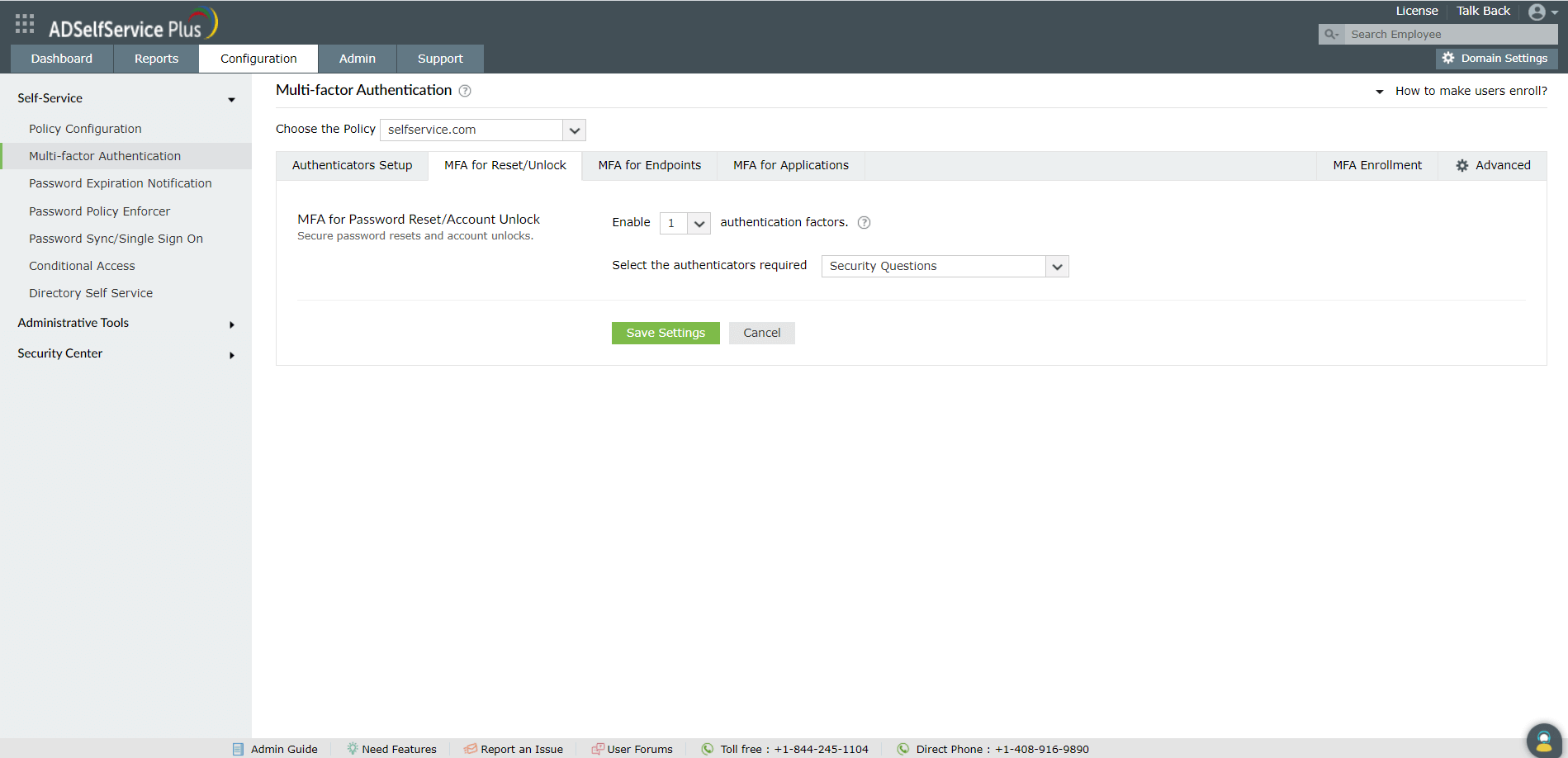
Steps to enable multi-factor authentication for password reset/account unlock
- Navigate to Configuration → Self-Service → Multi-factor Authentication → MFA for Reset/Unlock.
- Choose the Policy from the drop-down.Note: ADSelfService Plus allows you to create OU- and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- Enable the Select the authenticators required checkbox
- Use the Enable _ authentication factors option next to MFA for Password Reset/Account Unlock to select the number of authenticators
- Select RSA SecurID and other necessary configured authenticators from the drop-down.
- Click Save Settings.
Once configured, RSA SecurID will be one of the authenticators that verifies a user's identity when they try to reset their password, or unlock their account in ADSelfService Plus.
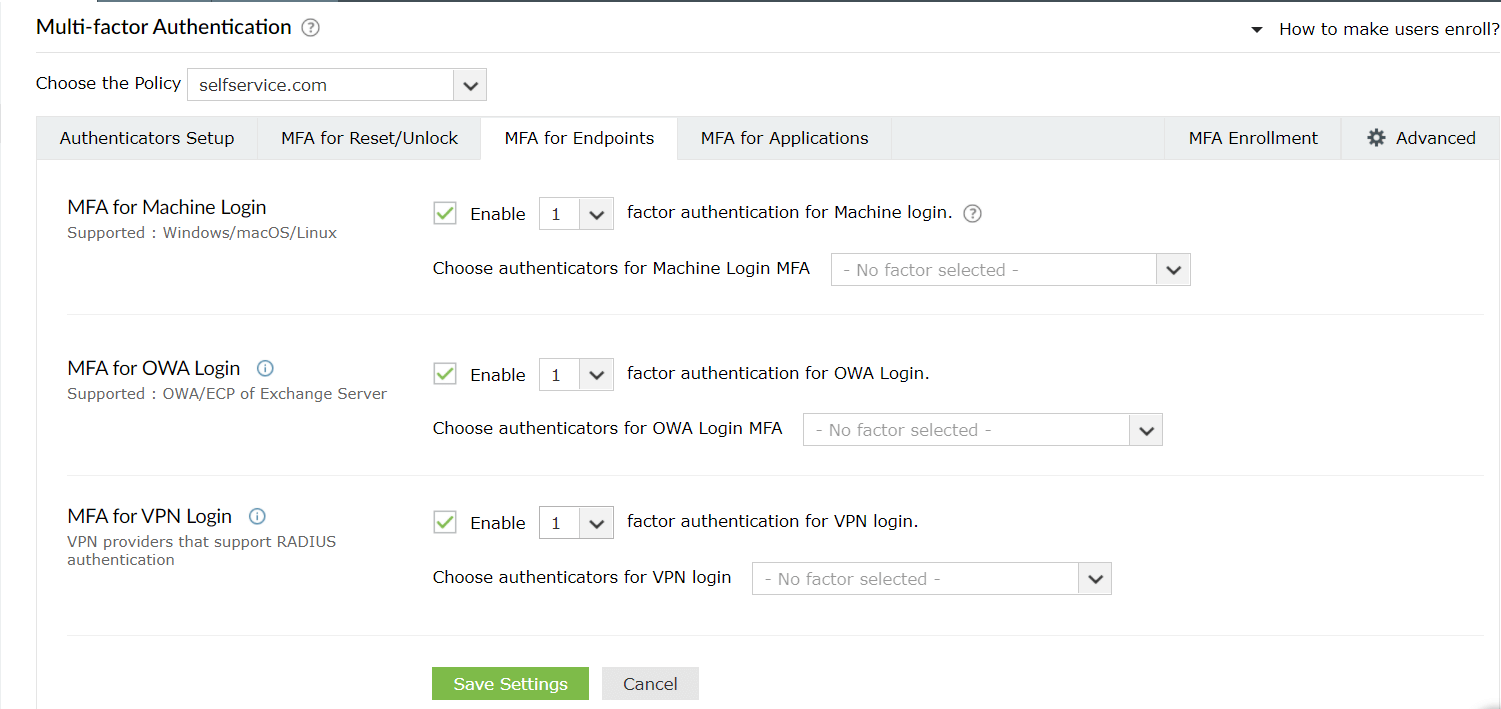
Steps to enable multi-factor authentication for endpoints
- Navigate to Configuration → Self-Service → Multi-factor Authentication → MFA for Endpoints..
- Choose the Policy from the drop-down.Note: ADSelfService Plus allows you to create OU- and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- MFA can be configured so additional factors of authentication are required at the login screens of Windows, macOS, and Linux machines or systems, during VPN or Outlook Web Access (OWA) logins.
- For machine logins:
- Go to MFA for Endpoints.
- Enable the Select the authenticators required checkbox.
- Use the Enable _ authentication factors option next to MFA for Machine Login to select the number of authenticators.
- Select RSA SecurID and other necessary configured authenticators from the drop-down.
- Click Save Settings.
- For OWA logins:
- Select the Enable second factor authentication option next to MFA for OWA Login, and choose RSA SecurID from the drop-down.
- Click Save Settings.
- For machine logins:
New to ADSelfService Plus?
Related Articles
How to configure multi-factor authentication with Duo Security
ADSelfService Plus wards off potential security threats by fortifying access to user accounts with multi-factor authentication (MFA), by adding an extra layer of security. When MFA is enabled, users are required to prove their identity through the ...Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...Configuring MFA for FTD VPN using RADIUS
This guide provides steps for enabling multi-factor authentication (MFA) using RADIUS for Cisco's Firepower Threat Defense (FTD) product using ManageEngine ADSelfService Plus' MFA for VPN feature. To enable RADIUS-based authentication for Cisco FTD, ...Configuring MFA for Cisco ASA SSL VPN using RADIUS
This guide provides steps for enabling multi-factor authentication (MFA) using RADIUS for Cisco's Adaptive Security Appliance (ASA) product using ManageEngine ADSelfService Plus' MFA for VPN feature. To enable RADIUS-based authentication for VPN ...How to safeguard local and remote Windows logons via ADSelfService Plus' endpoint multi-factor authentication
With cyberattacks on the rise, having only passwords as a defense mechanism is no longer safe. An additional filter is required to restrict unauthorized users. ADSelfService Plus handles this situation by supporting multi-factor authentication (MFA) ...