How to configure multi-factor authentication with Duo Security
ADSelfService Plus wards off potential security threats by fortifying access to user accounts with multi-factor authentication (MFA), by adding an extra layer of security. When MFA is enabled, users are required to prove their identity through the enforced authenticators in addition to passwords.
MFA can be enforced for password self-service operations along with login attempts to the ADSelfService Plus end-user portal, endpoints, and applications. ADSelfService Plus supports fifteen advanced authentication techniques, including Duo Security, biometrics, YubiKey authenticator, SAML authentication, and RSA SecurID.
Multi-factor authentication via Duo Security
When multi-factor authentication using Duo Security is enabled, during every login, users will have to prove their identity through any one of the following methods:
- Approving a push notification through the Duo Security mobile app.
- Entering a security pass code received through a verification call.
- Entering a security pass code generated during the login process.
Configuration
Duo Security-based multi-factor authentication can be configured in just three simple steps.
Step 1: Integrate Duo Security with ADSelfService Plus
- Log in to your Duo Security account (i.e., https://admin-3d5d33c0.duosecurity.com), or if you're a new user, sign up and log in.
- Navigate to Applications.
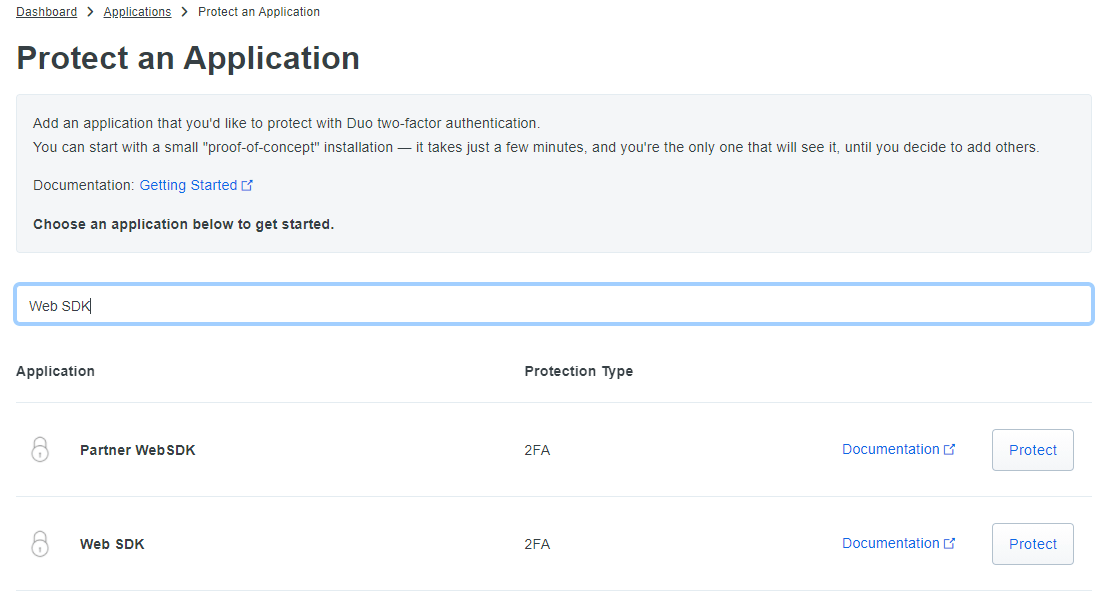
- Click Protect an Application.
- Search for Web SDK in the applications list.
- Click the Protect this Application link from the search result.
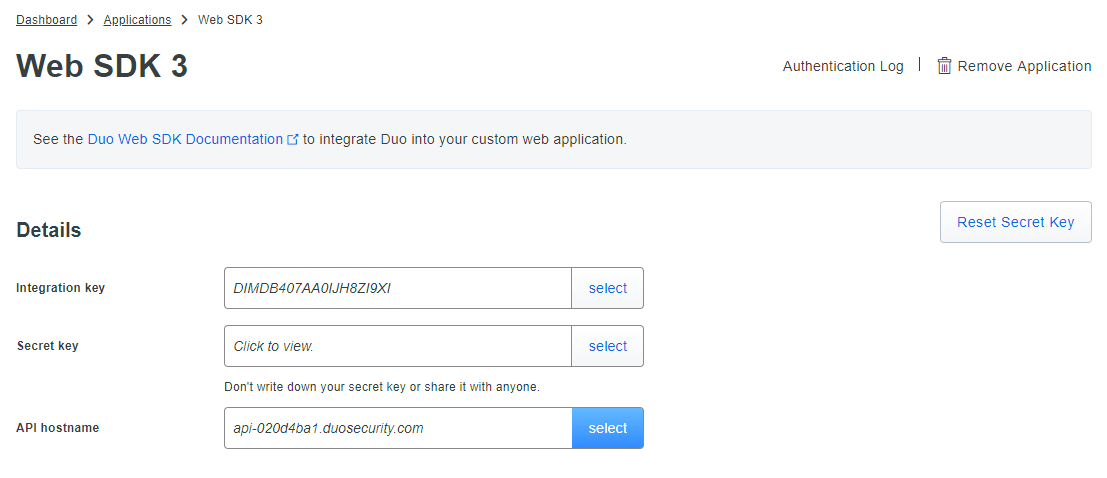
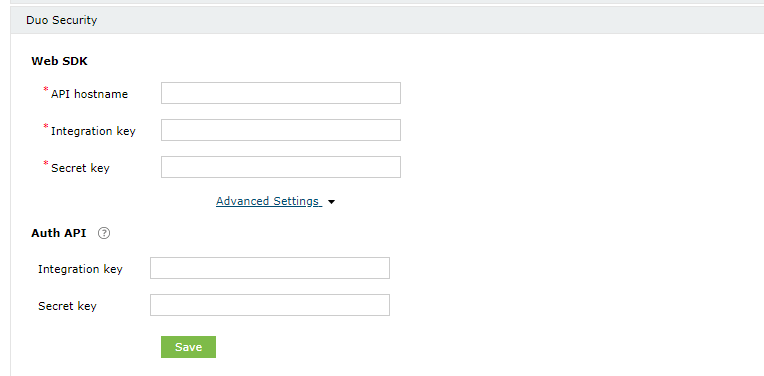
- Copy the values of Integration key, Secret key, and API hostname from the Web SDK page that opens up.
Configure Auth API (optional)
The Auth API configuration is used to verify a user's enrollment with Duo Security. If Auth API is not configured, it's mandatory to remove the user's enrollment in ADSelfService Plus on deleting a user's enrollment in Duo Security. If this isn't done, the user will be added back to Duo Security when it is used for authentication in ADSelfService Plus.
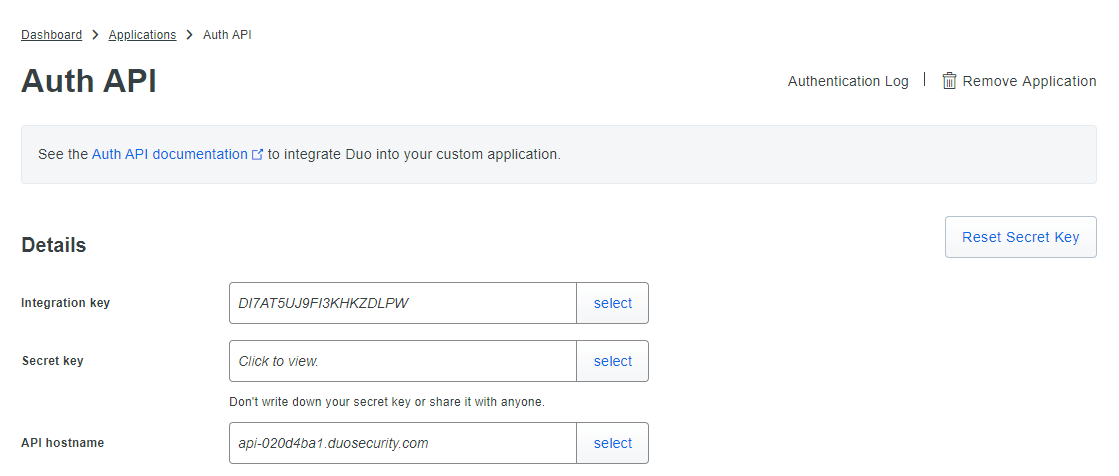
- If Auth API is configured, then go back to Applications → Protect an Application.
- Search for Auth API.
- Copy the values of the Integration key and Security key.
Step 2: Configure Duo Security in ADSelfService Plus
- Log in to the ADSelfService Plus console using administrator credentials.
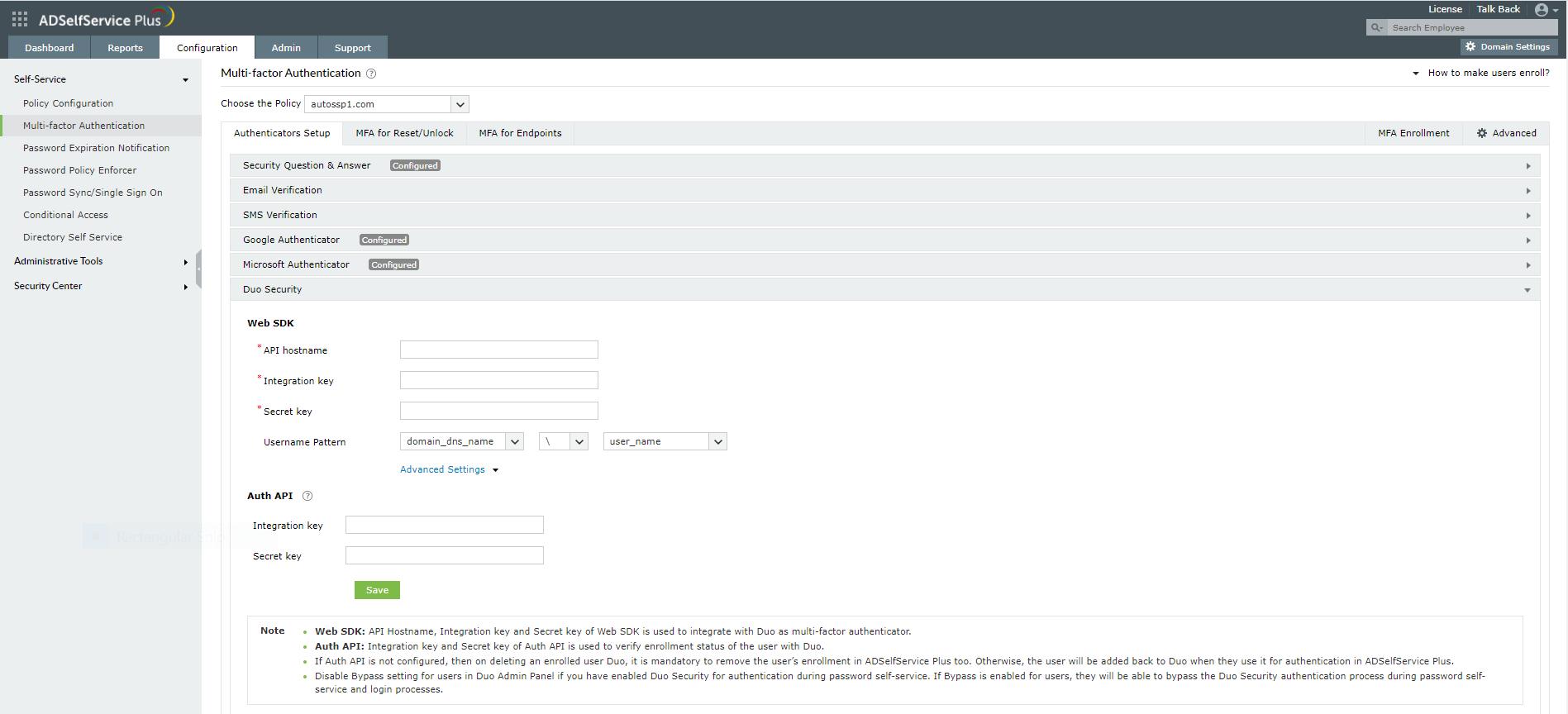
- Navigate to Configuration → Self-Service → Multi-factor Authentication → Authenticators Setup.
- Select Duo Security.
- Paste the values that you copied previously from the Web SDK page in the Integeration Key, Secret Key, and API hostname fields.
- If Auth API is configured, go to Advanced Settings and paste the values that you copied in this step from the Auth API page in the Integration key and Secret key fields.
- Click Save.
Steps to enable multi-factor authentication for ADSelfService Plus' end-user portal login
Prerequisite:
- SSL must be enabled: Log in to the ADSelfService Plus web console with admin credentials. Navigate to Admin → Product Settings → Connection. Select the ADSelfService Plus Port [https] option. Refer to this guide to learn how to apply a SSL certificate and enable HTTPS.
Steps to configure:
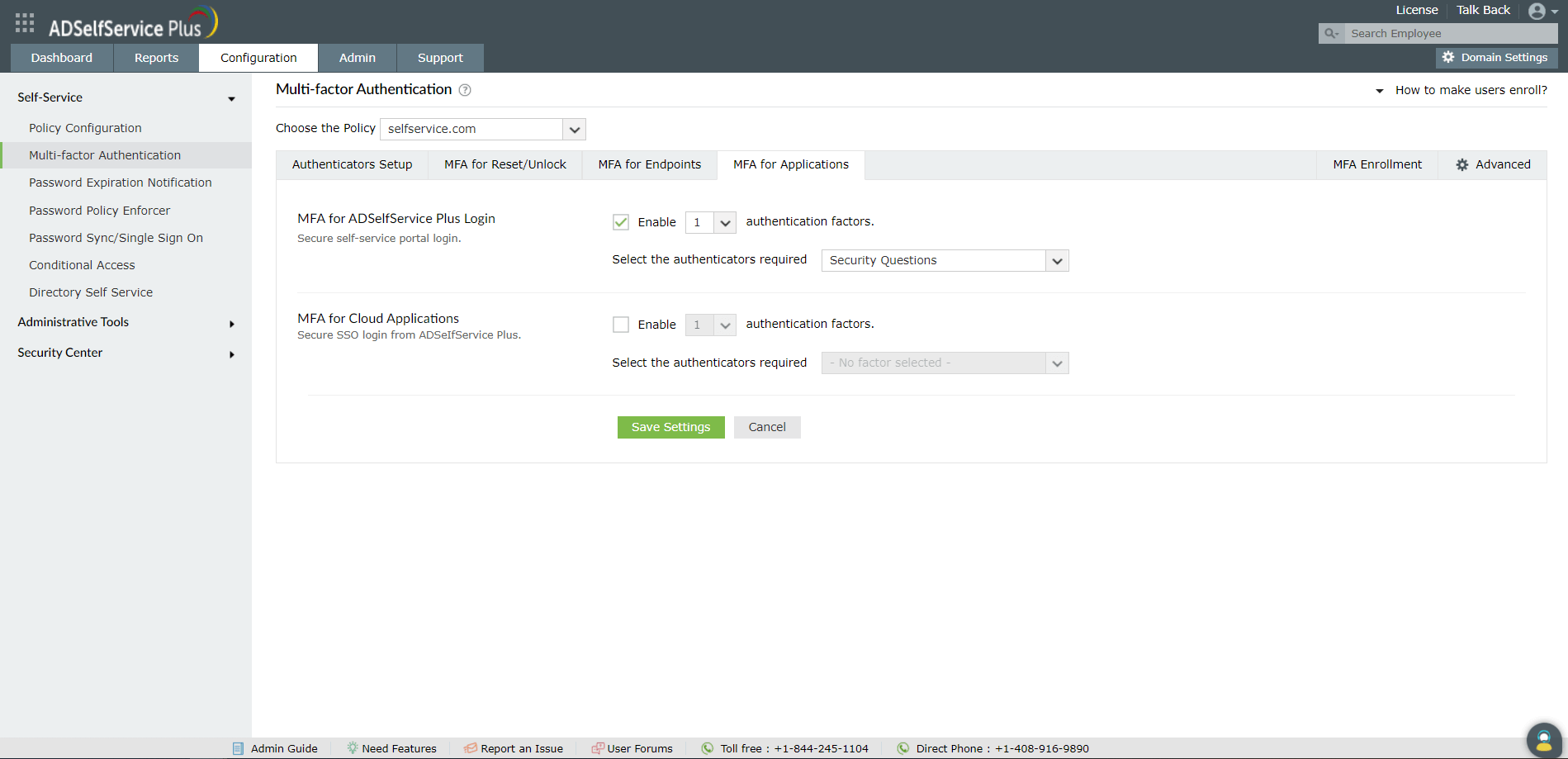
- Navigate to Configuration → Self-Service → Multi-factor Authentication → MFA for Applications..
- Choose the Policy from the drop-down.Note: ADSelfService Plus allows you to create OU- and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- Use the Enable _ authentication factors option next to MFA for ADSelfService Plus Login,
- Select Duo Security and other necessary authenticators from the Select the authenticators required drop-down.
- Click Save Settings.
Steps to enable multi-factor authentication for password reset/account unlock
Prerequisite:
- SSL must be enabled: Log in to the ADSelfService Plus web console with admin credentials. Navigate to Admin → Product Settings → Connection. Select the ADSelfService Plus Port [https] option. Refer to this guide to learn how to apply a SSL certificate and enable HTTPS.
Steps to configure:
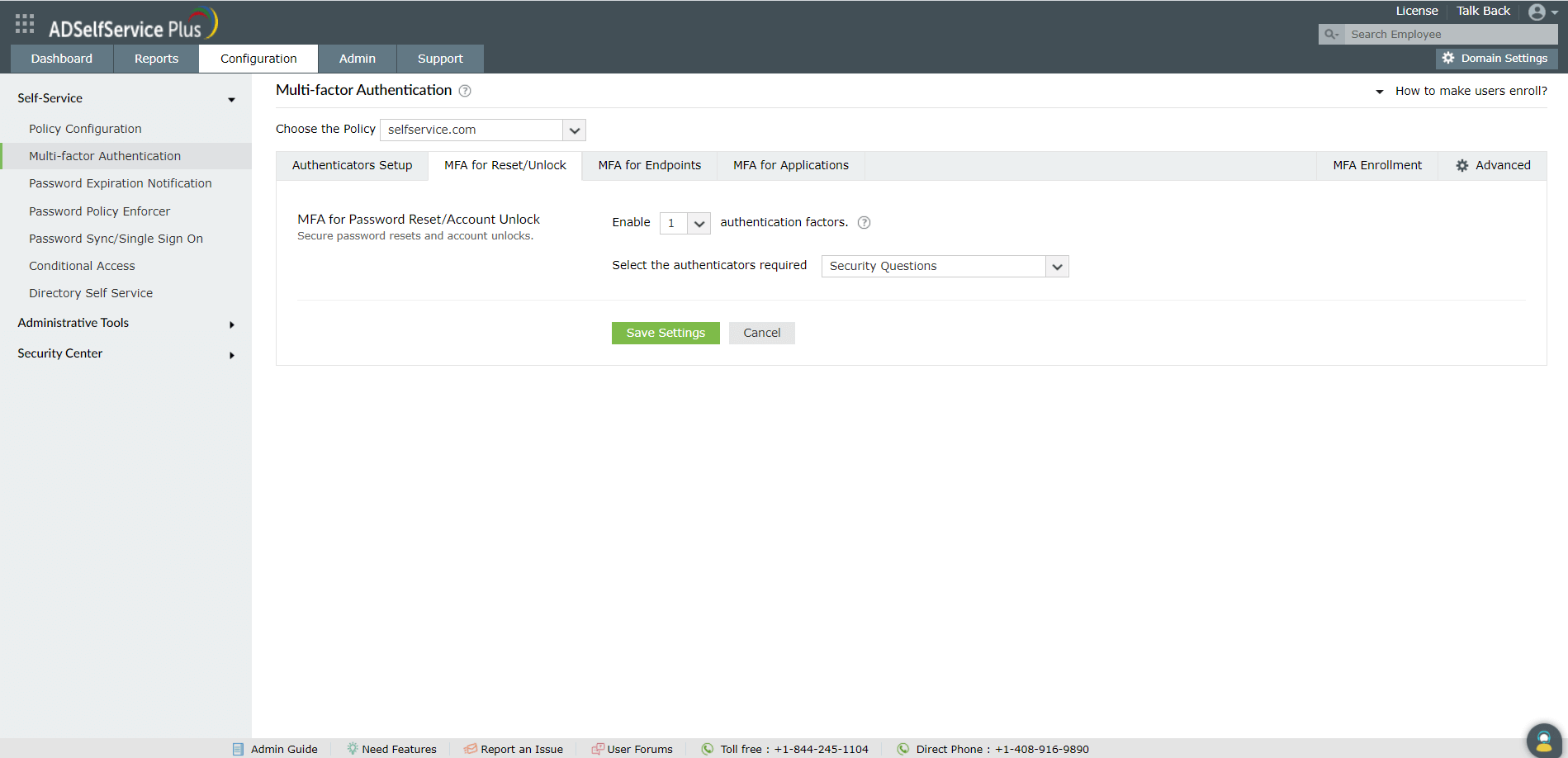
- Navigate to Configuration → Self-Service → Multi-factor Authentication → MFA for Reset/Unlock..
- Choose the Policy from the drop-down.Note: ADSelfService Plus allows you to create OU- and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- Enable the Select the authenticators required checkbox
- Use the Enable _ authentication factors option next to MFA for Password Reset/Account Unlock to select the number of authenticators
- Select Duo Security and other necessary configured authenticators from the drop-down.
- Click Save Settings.
Steps to enable multi-factor authentication for endpoints
Prerequisites:
- Utilize Endpoint MFA: Your ADSelfService Plus license must include Endpoint MFA. Visit the store to purchase it.
- SSL must be enabled: Log in to the ADSelfService Plus web console with admin credentials. Navigate to the Admin tab → Product Settings → Connection. Select the ADSelfService Plus Port [https] option. Refer to this guide to learn how to apply a SSL certificate and enable HTTPS.
- Access URL must be set to HTTPS: Navigate to Admin > Product Settings > Connection > Connection Settings > Configure Access URL and set the Protocol option to HTTPS.
- Applicable to MFA for machine logins: Install ADSelfService Plus client software for Windows, macOS, and Linux on the machines where you want to enable MFA. Click here for steps to install the ADSelfService Plus client software.
Configuration:
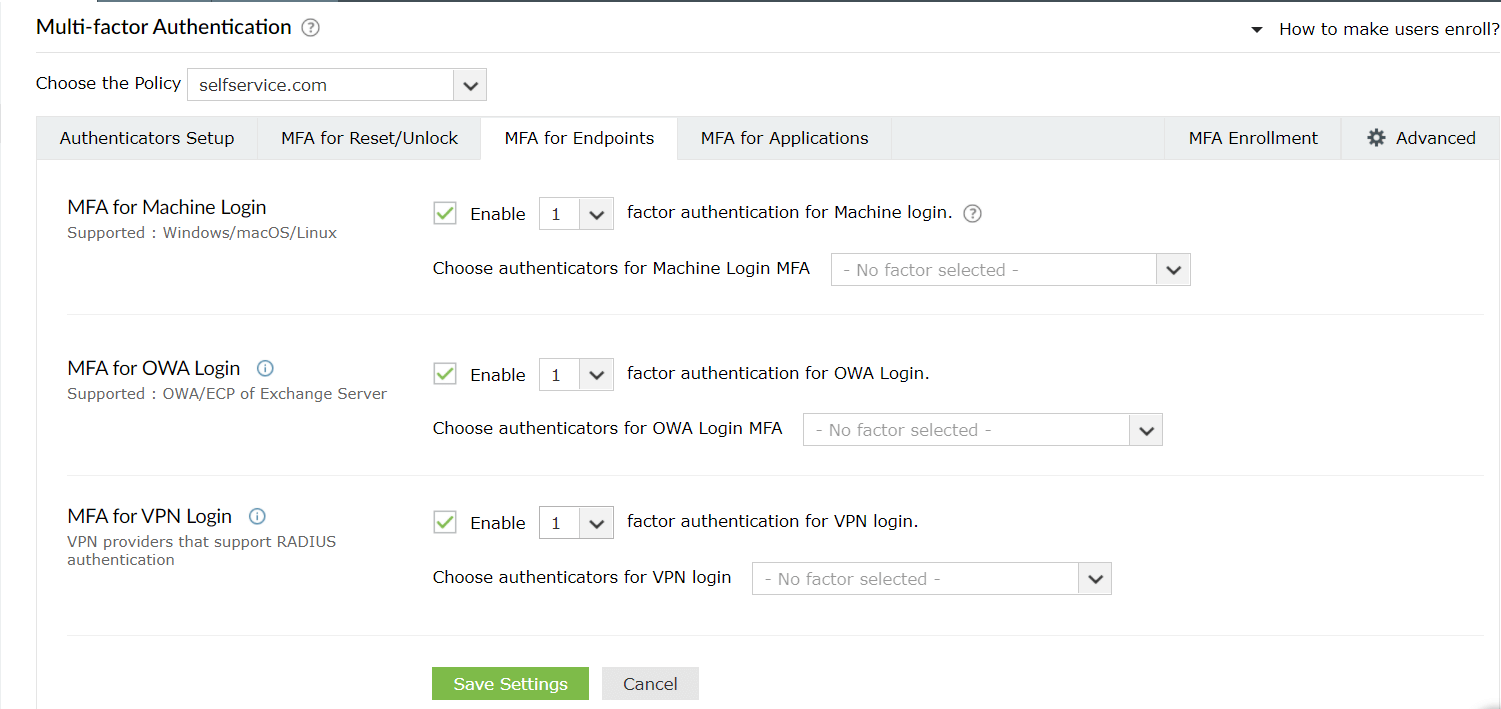
- Navigate to Configuration → Self-Service → Multi-factor Authentication → MFA for Endpoints.
- Choose the Policy from the drop-down.Note: ADSelfService Plus allows you to create OU- and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- MFA can be configured so additional factors of authentication are required at the login screens of Windows, macOS, and Linux machines or systems, during VPN or Outlook Web Access (OWA) logins.
- For machine logins:
- Navigate to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints > MFA for Machine Logins.
- Enable the Select the authenticators required checkbox
- Use the Enable _ authentication factors option next to MFA for Machine Login to select the number of authenticators
- Select Duo Security and other necessary configured authenticators from the drop-down.
- Click Save Settings.
- For OWA login:
- Navigate to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints > MFA for Machine Logins.
- Enable the Select the authenticators required checkbox.
- Select the Enable second factor authentication option next to MFA for OWA Login, and choose RSA SecurID from the drop-down.
- Click Save Settings.
- For machine logins:
- Click Save Settings.
New to ADSelfService Plus?
Related Articles
Configuring Duo Security for Active Directory password reset
Duo Security is an access security focused application that is primarily used for multi-factor authentication. One of the ways Duo Security can be used to verify users identities is using passcodes. Here, once the user has provided their username and ...Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...How to enable multi-factor authentication for privileged users
How can multi-factor authentication secure privileged user accounts? While all user accounts must be authenticated before gaining access to enterprise resources, privileged user accounts are of the utmost priority because they pose the greatest risk ...Bulk enrolling Duo Security-enabled users for password self-service
Enrollment is the only task that has to be completed before users can start enjoying the benefits of ADSelfService Plus password self-service. But many a time, administrators might have to constantly shoot out reminders urging users to enroll. Or ...How to configure multi-factor authentication with RSA SecurID
Setting up RSA SecurID authentication You can set up RSA SecurID as an authenticator in ADSelfService Plus in two steps: Include the ADSelfService Plus server in the SecurID SECURITY CONSOLE as an authentication agent. Configure ADSelfService Plus ...