Configuring Microsoft Authenticator for Active Directory-based actions
Microsoft Authenticator is an authentication method developed by Google that uses a time-based one-time-passcode (TOTP) in order to verify users' identities. It is often used as one of the multi-factor authentication (MFA) methods along with others in order to secure the login process into a service. Authentication using this method requires the Microsoft Authenticator app. After the users have provided valid login credentials, the service asks them for the 6-digit TOTP from the app. The users then have to run the app to obtain the TOTP and enter it in the service, and verify their identity.
Empowering Active Directory domain users with self-service password reset can benefit an organization in more ways than one.
- Users need not wait for admin intervention and can have seamless access to their machines.
- The help-desk admin will not be tasked with hundreds of password reset requests and can instead attend to other crucial tasks.
However, providing users with the ability to reset their passwords can be risky if proper security measures are not put in place. Since users won't have to provide any old credentials, it is important to verify their identities before they can reset their passwords. Using a multi-factor authentication (MFA) method like Microsoft Authenticator is a fail-safe way to authenticate them for Active Directory domain password resets.
ADSelfService Plus, an identity security solution, offers a self-service password reset and account unlock feature that is secured by MFA. The solution supports up to 19 methods of MFA including Google Authenticator, biometrics, and YubiKey Authenticator to verify users' identities during
- Windows, macOS, and VPN logins.
- Outlook Web Access logins
- Active Directory self-service password reset or account unlock actions via the ADSelfService portal, ADSelfService Plus mobile app, and native Windows/macOS/Linux login screen.
- Enterprise application logins through single sign-on (SSO).
- Self-update of Active Directory profile information, subscription to mail groups, and employee search using ADSelfService Plus.
Step to enable Microsoft Authentication for MFA in ADSelfService Plus:
- Download and install ADSelfService Plus.
- Configure your Active Directory domains.
- Navigate to Configuration > Self-Service > Multi-factor Authentication > Authenticators Setup.
- From the Choose the Policy drop-down, select a policy.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration > Self-Service > Policy Configuration > Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy. Only users belonging to OUs and groups in the policy can make use of the self-service feature(s) selected. - Click Microsoft Authenticator section.
- Click the Enable Microsoft Authenticator button.
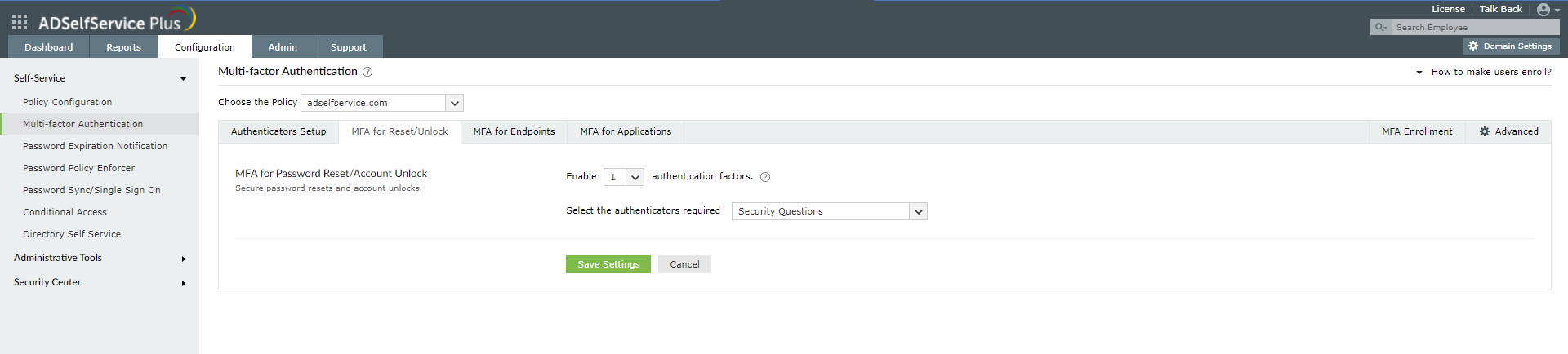
Enabling Microsoft Authenticator for Active Directory password resets
- Go to Configuration > Self-Service > Multi-factor Authentication > MFA for Reset/Unlock.
- Enter the number of authentication factors to be enforced, and select Microsoft Authenticator along with any other authentication techniques to be used.
- Click Save Settings.
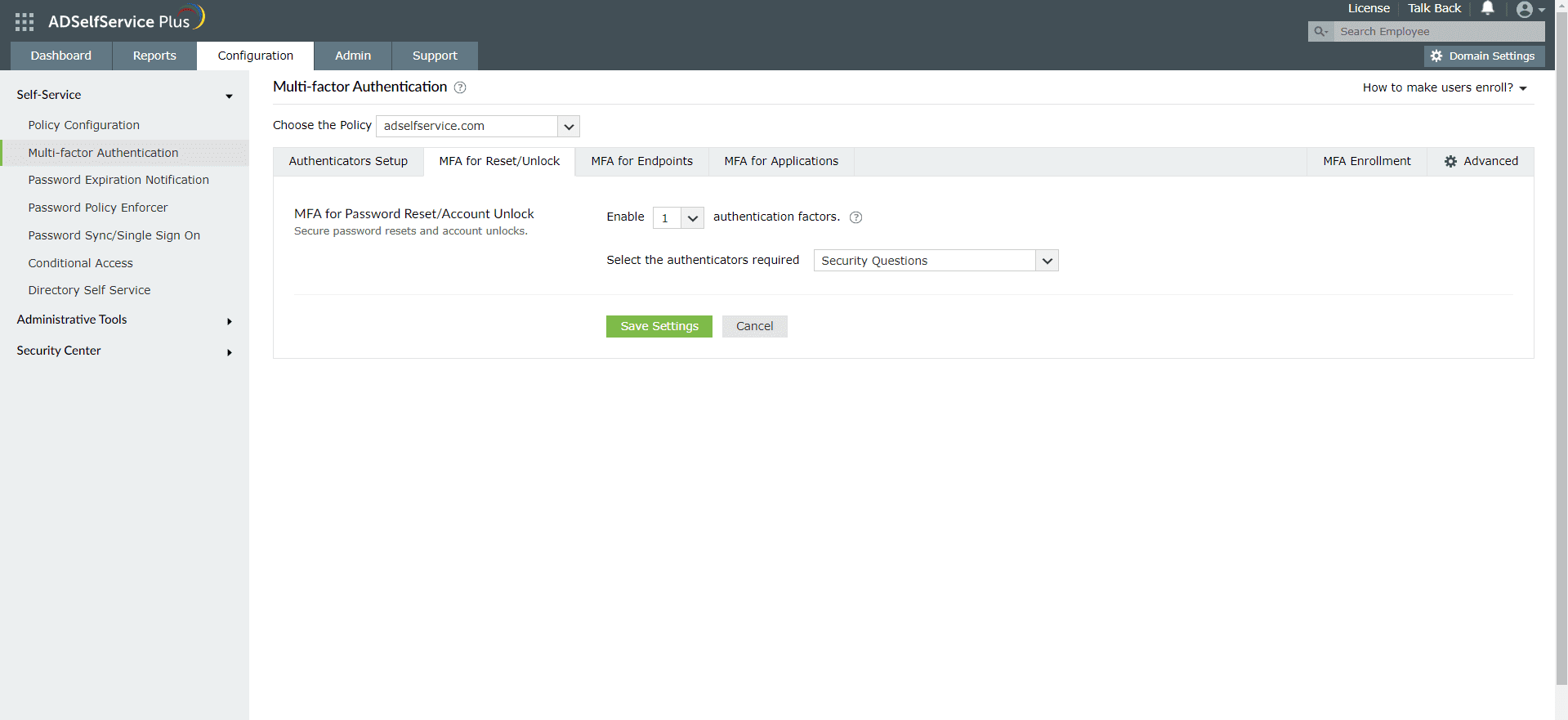
Enabling Microsoft Authenticator for Active Directory domain logins
- Go to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for which sets of users.
- Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration > Self-Service > Policy Configuration > Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- In the MFA for Machine Login section, check the Enable _ authentication factors box and select the Microsoft Authenticator from the drop-down.
- Click Save Settings.
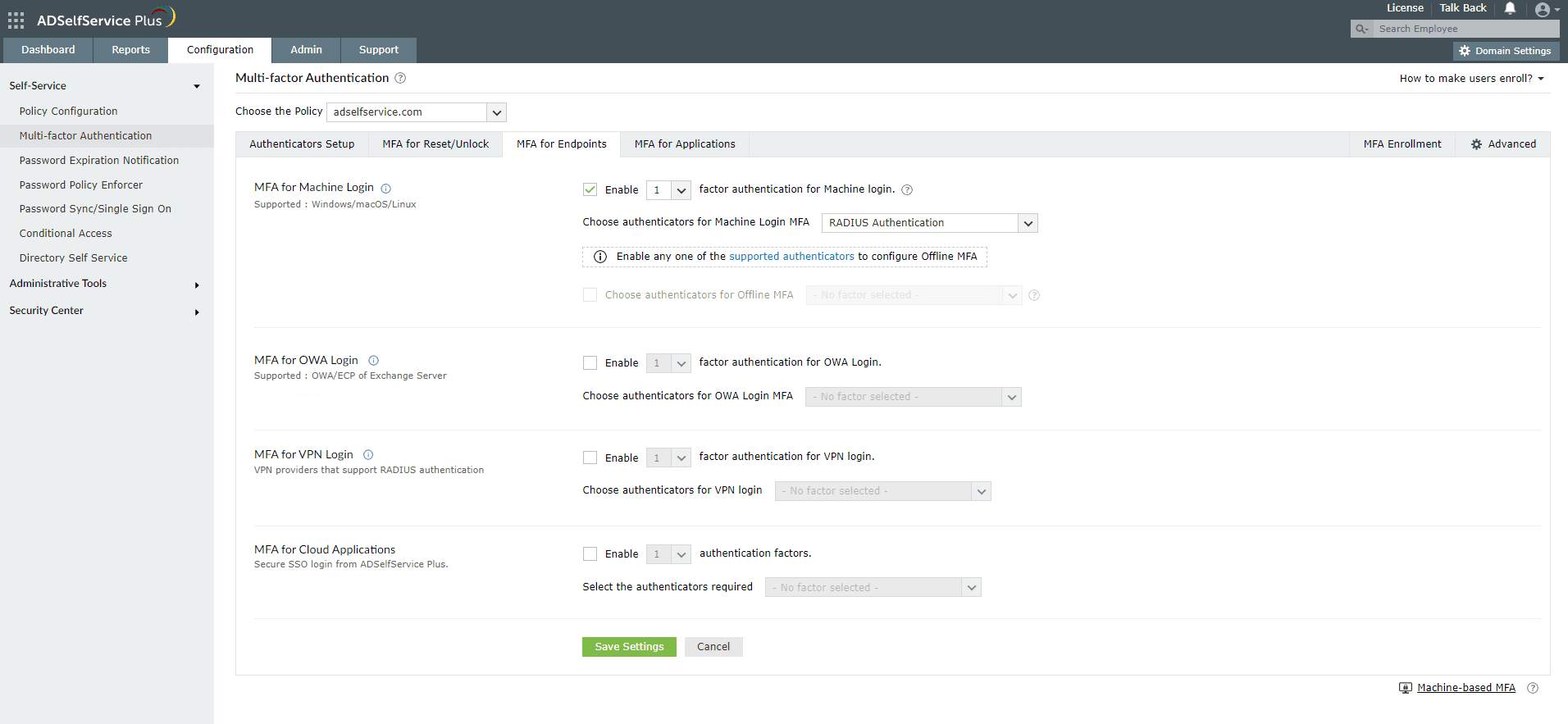

Note: To enable MFA for Active Directory domain logins:
- The ADSelfService Plus login agent must be installed on client machines. Click here for steps on login agent installation.
- SSL must be enabled: Log in to the ADSelfService Plus web console with admin credentials. Navigate to the Admin tab > Product Settings > Connection. Select the ADSelfService Plus Port [https] option.
Learn more about ADSelfService Plus and its Multi-factor Authentication feature.
New to ADSelfService Plus?
Related Articles
Configuring Google Authenticator for Active Directory password resets and logins
Google Authenticator is an authentication method developed by Google that uses a time-based one-time-passcode (TOTP) in order to verify users' identities. It is often used as one of the multi-factor authentication (MFA) methods along with others in ...Configuring QR code-based authentication for Active Directory-based actions
QR code-based authentication is a type of multi-factor authentication method that involves scanning a QR code with an app in order to verify one's identity. When authenticating into a service using MFA, users need to provide their account credentials ...Configuring MFA for FTD VPN using RADIUS
This guide provides steps for enabling multi-factor authentication (MFA) using RADIUS for Cisco's Firepower Threat Defense (FTD) product using ManageEngine ADSelfService Plus' MFA for VPN feature. To enable RADIUS-based authentication for Cisco FTD, ...Configuring MFA for Cisco ASA SSL VPN using RADIUS
This guide provides steps for enabling multi-factor authentication (MFA) using RADIUS for Cisco's Adaptive Security Appliance (ASA) product using ManageEngine ADSelfService Plus' MFA for VPN feature. To enable RADIUS-based authentication for VPN ...Multi-factor authentication techniques in ADSelfService Plus
Let's take a look into the various authentication methods supported by ADSelfService Plus for enterprise multi-factor authentication (MFA). Why should you use MFA? Authentication based solely on usernames and passwords is no longer considered secure. ...