Use-case 18: How To Detect And Manage Account Lockout Efficiently In Your Active Directory
Account Lockout is a necessary-evil provided by Microsoft. The purpose behind account lockout is to temporarily disable the user account in-case of a brute force attack. When the attacker tries a combination of passwords, the account disables for a period of 30 minutes over 10 bad password attempts(Microsoft default). Depending on the complexity, the assailant may take weeks, months, years to crack the credentials. This encourages the user to use complex passwords through their password policy.
On the other hand, Let's say the employee returns after a long vacation and forgets his complex password. It would consume valuable business resource, both in the time expended to reset the credentials and loss of productivity. Another disadvantage is when the password expires and the user changes his password. The user will be able to logon to a certain DC only, as his password would have not been replicated to the others and also, issues with cached password while accessing resources would occur.
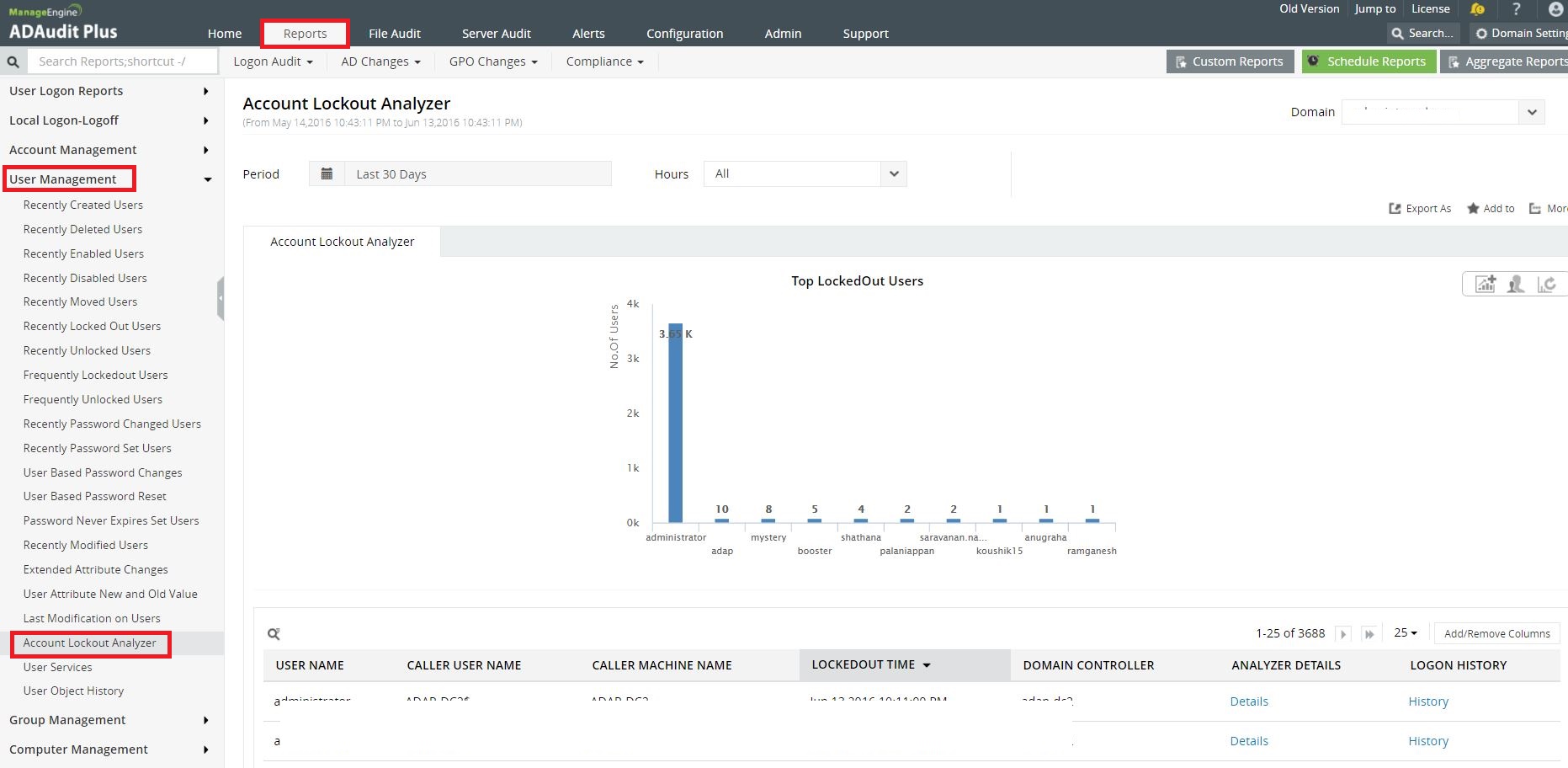
ADAudit Plus provides comprehensive reports on recently locked out users, frequently locked out users and a special report that provides you with the complete analysis of the source of frequent account lockout.
Step 1: Kindly go to Reports --> User Management --> Account Lockout Analyzer.
Select the Domain and the Period.
Click on Details to view the reason for lockout and click on History to view the logon history for that user.
#TheAD+Experience
| Shane Clinton |
||||||
| ManageEngine ADSolutions Team |
||||||
|
||||||
| How To | Forum | File Permission Management |
|
|||||
| ADManager Plus | ADAudit Plus | ADSelfService Plus | Exchange Reporter Plus | Recovery Manager Plus | AD360 |
||||||
Topic Participants
Shane Clinton
New to M365 Manager Plus?
New to M365 Manager Plus?
New to RecoveryManager Plus?
New to RecoveryManager Plus?
New to Exchange Reporter Plus?
New to Exchange Reporter Plus?
New to SharePoint Manager Plus?
New to SharePoint Manager Plus?
New to ADManager Plus?