Use-case 13: How Would You Tackle Compromised Employee Account In Your Active Directory
When a crook employee gets hold of crucial employee credentials, your Active Directory can go bogus. Compromised accounts can turn the privileges of your Active Directory upside down and access resources inside out.
Identifying compromised accounts is quiet challenging, if you don't have the right tools for the job. Monitoring logon activity, abnormal permission changes and frequent access to key resources can provide some heads-up to trailing a compromised account. With ADAudit Plus, speculating such attacks is easy as pie.
However, the universal first-approach would be a bulk password reset for account that bring second thoughts on its authenticity. .
Step 1: Kindly go to AD Mgmt --> User Modification --> Bulk User Modification --> Reset password.
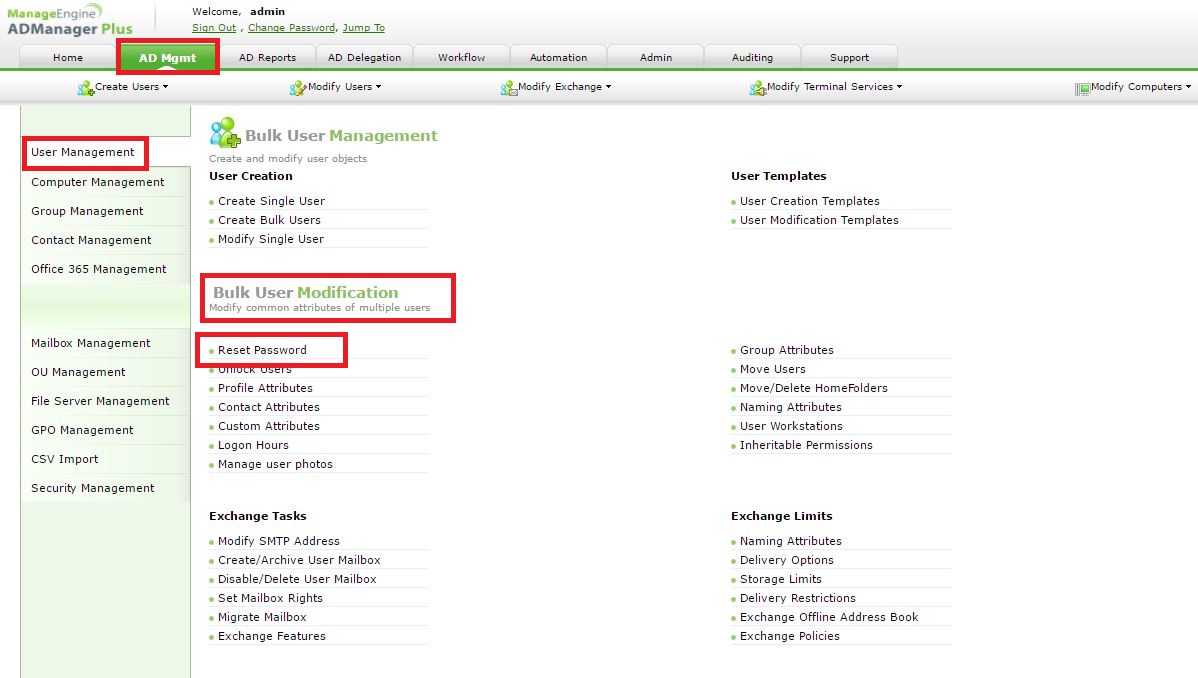
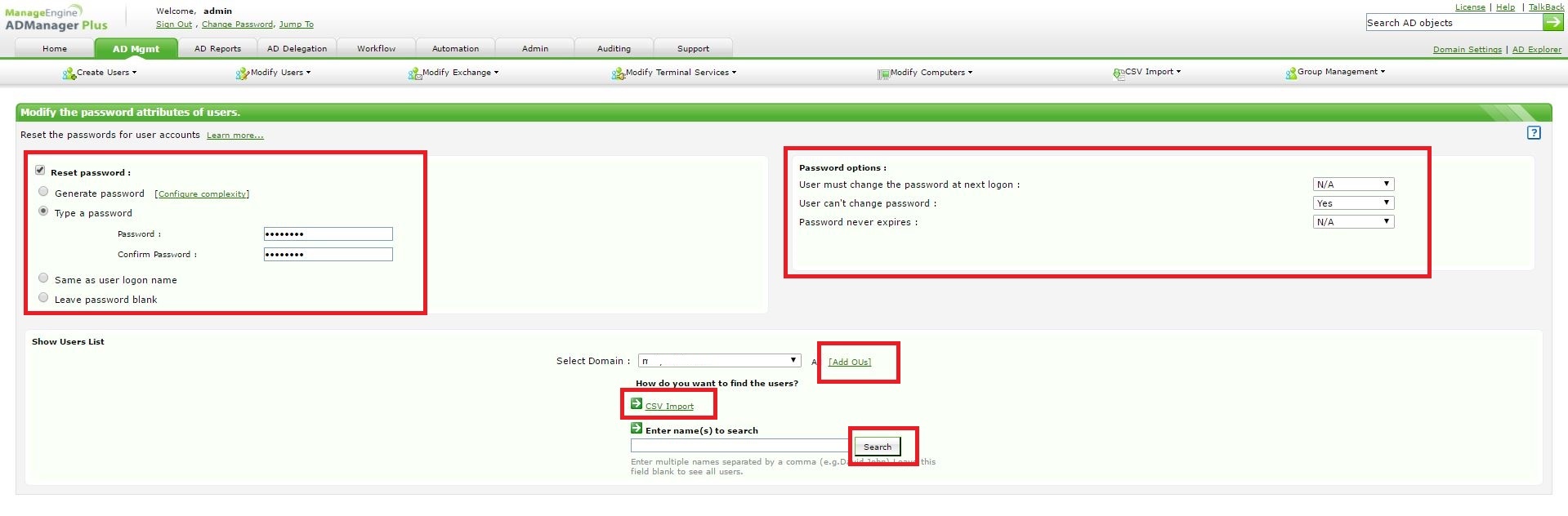
Step 2: You can select the users whose passwords need to be reset through two options,
a. Import the list of users through a CSV file.
b. If all the users belong to an OU, you can choose that specific OU and click on search.
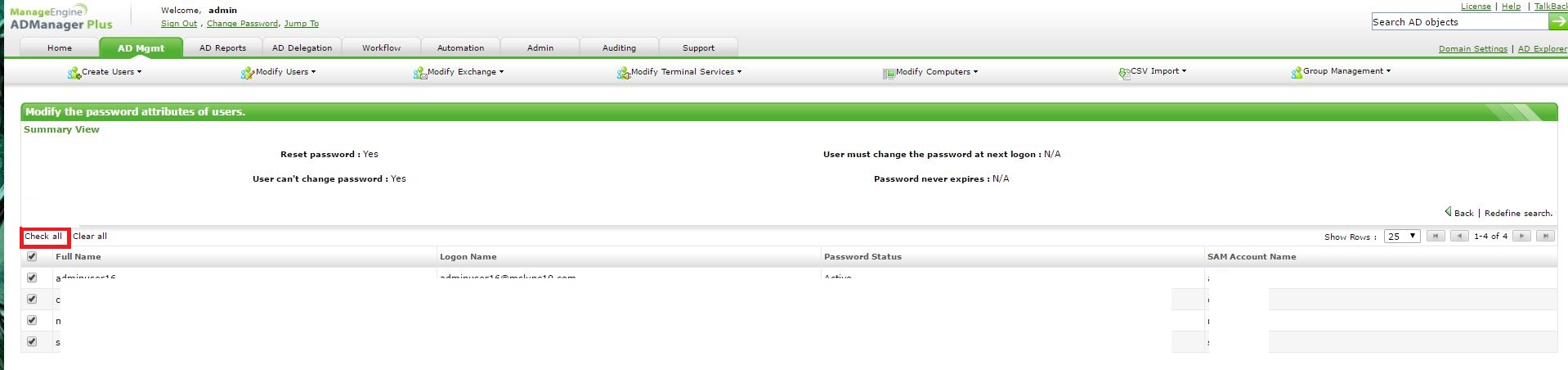
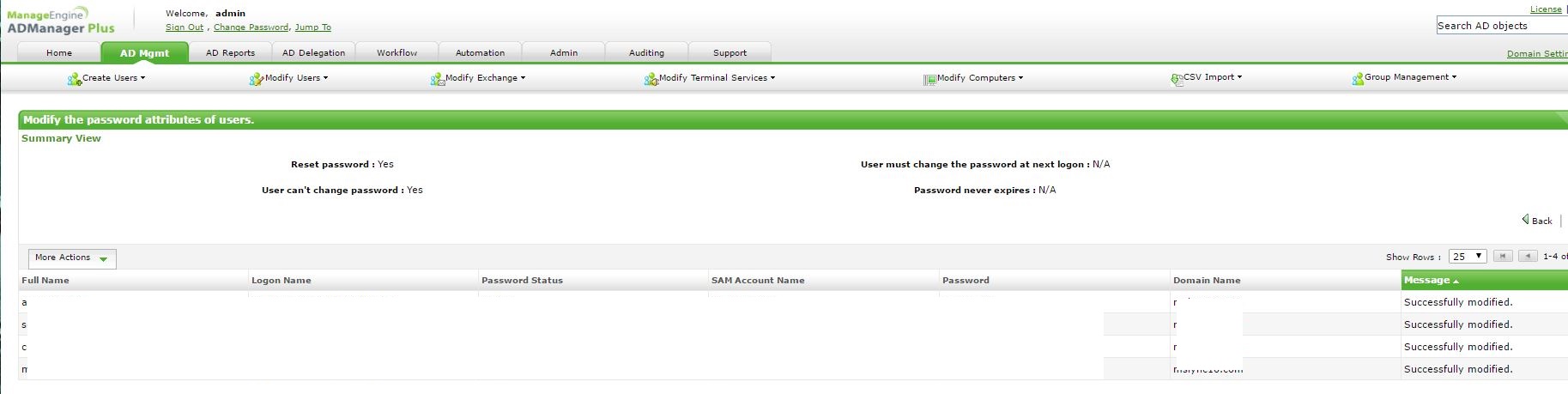
Step 3: Click on check all and then, apply.
#TheAD+Experience
| Shane Clinton |
||||||
| ManageEngine ADSolutions Team |
||||||
|
||||||
| How To | Forum | File Permission Management |
|
|||||
| ADManager Plus | ADAudit Plus | ADSelfService Plus | Exchange Reporter Plus | Recovery Manager Plus | AD360 | ||||||
Topic Participants
Shane Clinton
New to M365 Manager Plus?
New to M365 Manager Plus?
New to RecoveryManager Plus?
New to RecoveryManager Plus?
New to Exchange Reporter Plus?
New to Exchange Reporter Plus?
New to SharePoint Manager Plus?
New to SharePoint Manager Plus?
New to ADManager Plus?