TWTQ: The latest correlation rule builder
Hey all!
Here's This Week's Top Question (TWTQ):
Q: How do I create rules using the correlation rule builder?
A: We are constantly updating Log360's correlation module by adding new rules or features which make it easier to use. In build 11134 of the EventLog Analyzer component of Log360 (released in May), the correlation rule builder has gotten a revamped interface, which makes it even more user-friendly.
First, a quick refresher on what a correlation rule is: A correlation rule is simply a pattern which describes a security incident. Each rule consists of a sequence of distinct events, or actions. Simply put, correlation rules tell Log360 what to look for in your network logs.
Here's how you can use the new rule builder to easily create these rules:
- To open the rule builder, go to Correlation > Manage Rules.
- To update an existing rule, click on the pencil icon next to the required rule.
- To create a new rule, click +Create correlation rule.
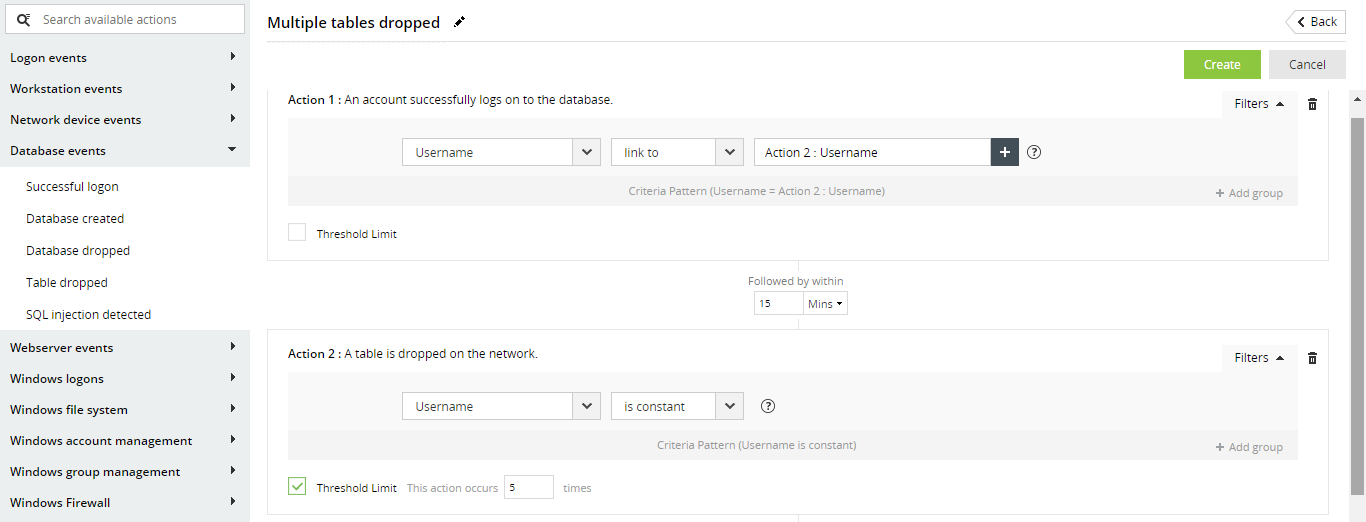
- You can see the complete list of actions on the left menu. To add an action to a rule, simply click on one from this list.
- Once you have added your desired actions, you can rearrange their order by dragging and dropping them into place.
- Now, specify the time windows between these actions.
- Next, you can use filters to add business context to your rule and make your rule more well-defined. To add filters for an action, click on Filters.
- You can use filters to place conditions on the values of fields within each action. For instance, you can create a filter like "Username starts with a K." You can add multiple filters, and relate them using logical operators like AND or OR.
- You can also group filters as needed and relate the groups with each other.
- There are also a couple of other filters you can use. If you choose Username Is constant, then the correlation module ensures that the username remains the same throughout repeated occurrences of the action. For instance, if you are looking for five "table dropped" actions within fifteen minutes, you can say Username is constant to ensure that it is the same user deleting multiple tables on your database.
- You can also compare the value of the username field to fields from other actions using the Link to option. For instance, if the "table dropped" action follows a "user logon" action, you can link the username field in both actions. This way, you only receive an alert if the same user logs on to your database and shortly starts dropping multiple tables.
If you do not see this interface for the correlation rule builder, you probably haven't upgraded the product yet. If you're using EventLog Analyzer, you can
upgrade to the latest version from here.
Topic Participants
Niyathi Bhat
New to M365 Manager Plus?
New to M365 Manager Plus?
New to RecoveryManager Plus?
New to RecoveryManager Plus?
New to Exchange Reporter Plus?
New to Exchange Reporter Plus?
New to SharePoint Manager Plus?
New to SharePoint Manager Plus?
New to ADManager Plus?