TWTQ: How the STIX/TAXII feed processor works
Hey everyone,
Here's This Week's Top Question (TWTQ):
Q: What are STIX and TAXII? How does EventLog Analyzer's STIX/TAXII feed processor work?
A: The Structured Threat Information eXpression (STIX) protocol describes a structured language for describing threats, and the Trusted Automated Exchange of Indicator Information (TAXII) protocol describes how this threat information can be communicated. Simply put, STIX and TAXII are global standards for identifying and sharing threat information. Together, they provide a collaborative threat sharing platform for organizations across the globe. Threat feeds based on these protocols are widely used and always provide the latest, most reliable threat information.
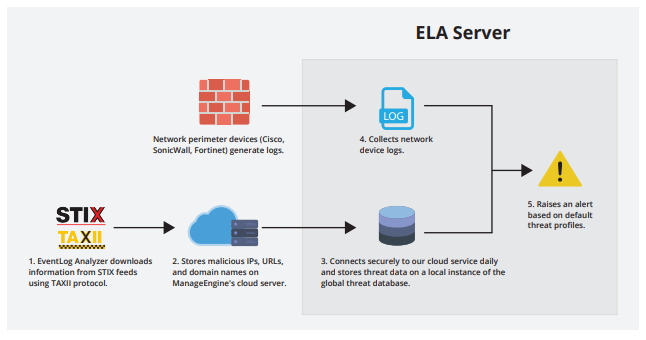
EventLog Analyzer processes data from prominent STIX/TAXII threat feeds and monitors your network for globally blacklisted IP addresses, URLs, and domains. You can thus detect any incoming traffic from malicious servers, or attempts to contact external callback servers.
The best part is, this feature is preconfigured - EventLog Analyzer starts monitoring your devices as soon as you add them within the product. The threat information is also automatically updated, so all alerts are based on the latest information.
EventLog Analyzer processes threat data from the following STIX based feeds:
- AlienVault OTX
- Hail a TAXII
These feeds are highly popular and contain reliable, up-to-date threat data.
EventLog Analyzer dynamically collects the latest data from these feeds, every 24 hours. This way, you don't have to perform any extra configurations, and yet be sure that the alerts you receive for malicious IPs, URLs, or domains are based on the latest threat data.
The below architecture diagram explains how the STIX/TAXII feed processor works:
Learn more about the feature here.
Topic Participants
Niyathi Bhat
New to M365 Manager Plus?
New to M365 Manager Plus?
New to RecoveryManager Plus?
New to RecoveryManager Plus?
New to Exchange Reporter Plus?
New to Exchange Reporter Plus?
New to SharePoint Manager Plus?
New to SharePoint Manager Plus?
New to ADManager Plus?