TWTQ: Customizing correlation reports
Hey everyone!
Here's This Week's Top Question (TWTQ):
Q: How do I customize the correlation reports to suit my requirements?
A: As you know, every security incident is composed of a sequence of distinct events, or actions. For instance, if attackers try to steal data from your database, then they must first intrude into your network. They can do this by various means. For instance, they may use a VPN to get access to the network. They then log into your database by cracking the credentials or using known credentials. Finally, they copy or modify the data in the database. As you can see, this database breach involves distinct events:
- VPN logon.
- Windows logon.
- Database logon.
- Database read/write operation.
These actions, when they occur in this order, might be a threat and you should look into it and ensure that it's an authorized database operation. This is where correlation helps—connecting the dots between actions.
EventLog Analyzer's correlation engine works in real-time, includes predefined rules and actions that help detect security incidents with minimal effort. One of the best parts about the solution's correlation feature is the aggregated incident reports which give you a complete picture of any security incident that occurs in your network. You can even select the exact information you require to be displayed on the report. To do this, simply navigate to the required report in the correlation tab and click on the column selector icon on the top right of the table. The
Add/Remove Columns dialog box opens:
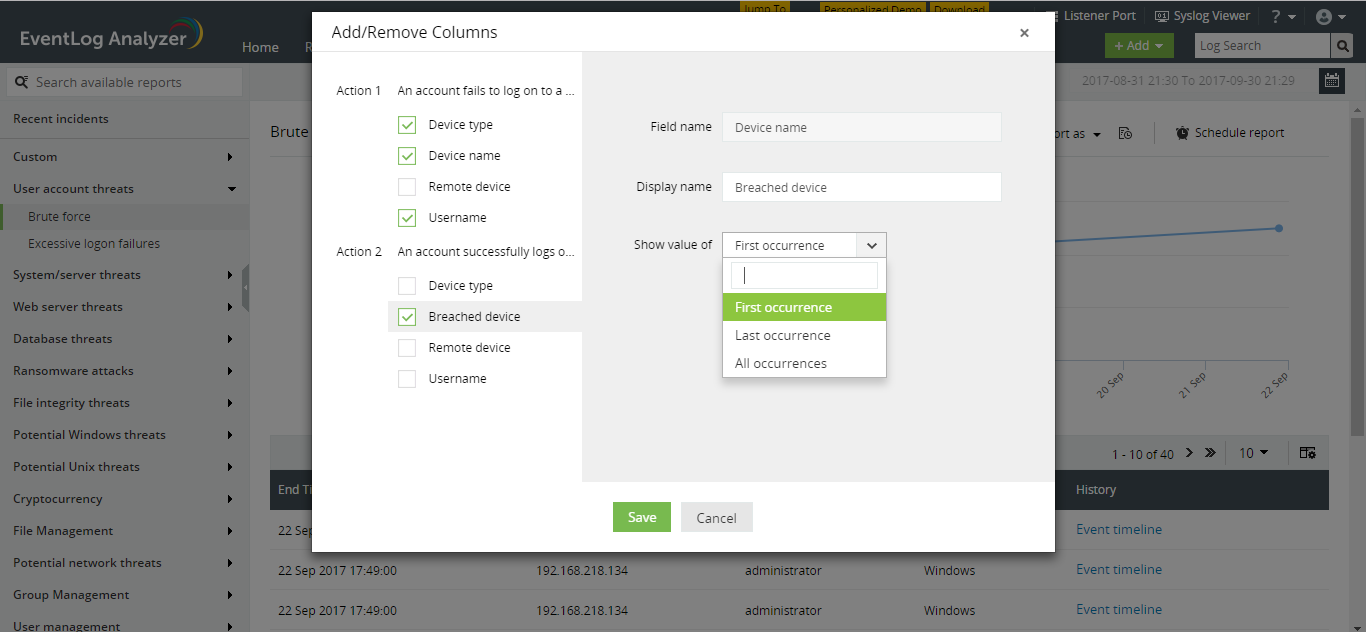
The
Add/Remove Columns dialog box displays the list of actions, and the information fields associated with each. Simply select the fields you require to be shown in your report.
You can also rename the fields as per your specific internal conventions. To do this, click on the pencil icon next to the desired field and provide a 'Display name'.
A certain action may occur more than once in the entire incident. For instance, a brute force logon attempt consists of multiple failed logon attempts, followed by a successful logon. For actions which occur multiple times, you can choose to display information from the first, last or all occurrences of the action, by using the 'Show value of' drop down for the required field.
With a range of options, you have complete control over the information in your report, and can review security incidents with ease.
Topic Participants
Niyathi Bhat
boyd
New to M365 Manager Plus?
New to M365 Manager Plus?
New to RecoveryManager Plus?
New to RecoveryManager Plus?
New to Exchange Reporter Plus?
New to Exchange Reporter Plus?
New to SharePoint Manager Plus?
New to SharePoint Manager Plus?
New to ADManager Plus?