TWTQ: Conducting forensic investigations with correlation reports
Hey everyone!
Here's This Week's Top Question (TWTQ):
Q: How can I conduct effective log forensic investigations with correlation reports?
A: When any incident is detected, the first course of action to be taken is a forensic investigation. This involves combing through your logs to identify a log trail, which tells you how an attacker breached your network and accessed your critical data and resources, and any other actions he/she might have taken.
The correlation module of EventLog Analyzer vastly simplifies this process. The correlation engine detects security incidents which comprise a sequence of multiple events. It then aggregates them into a single incident report.
So when you discover a security incident in your network, a single report can tell you when it happened, on which device it was discovered, who was involved, and also break it down into the sequence of events that led up to it.
To access a report for any incident, go to:
Correlation tab -> Select the required incident from the left menu.
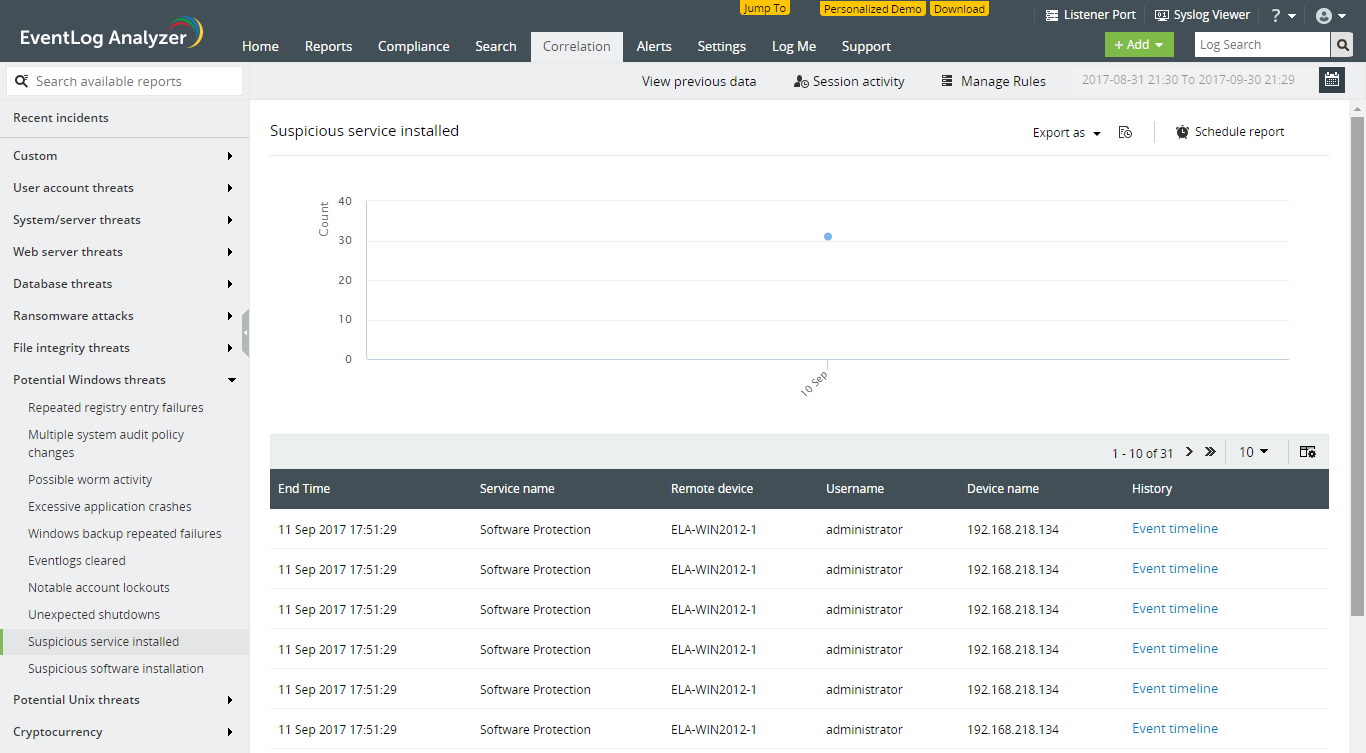
The above report helps you detect potentially malicious service installations, by looking for brute force Windows logons, followed by a service being installed, and then started. Each entry in the table denotes an individual occurrence of the incident. Clicking on 'Event timeline' next to the required incident, gives you a complete log trail of the events that led up to the incident:
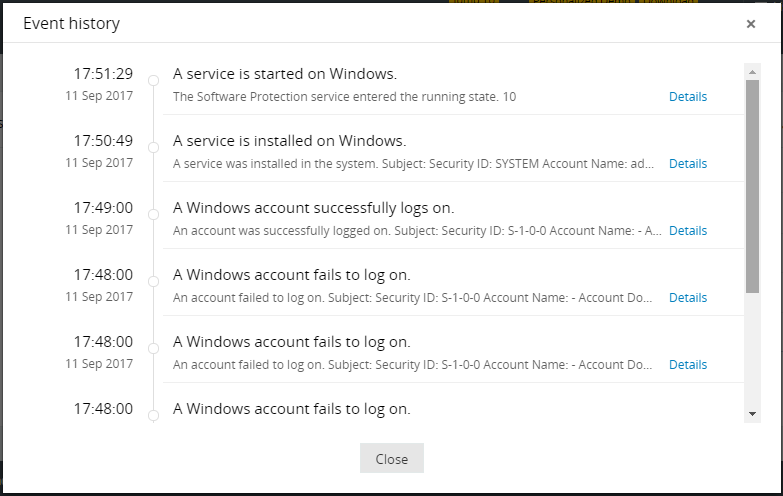
You can even click on 'Details' to look at the raw log contents. As you can see, with a single click, you're able to answer the question—How did this happen?
Apart from the specific log trail which led to the incident, you may also like to check all other logs generated by the affected user and machine. This could give you an idea of any other activity carried out by an attacker during the time of the incident. The correlation module allows you to do this as well, with a single click. Simply click on the forensics icon ([icon image]) which appears when you hover over the incident in the correlation report.
In this way, the correlation report allows you to conduct in-depth forensic investigations into any security incident.
Topic Participants
Niyathi Bhat
New to M365 Manager Plus?
New to M365 Manager Plus?
New to RecoveryManager Plus?
New to RecoveryManager Plus?
New to Exchange Reporter Plus?
New to Exchange Reporter Plus?
New to SharePoint Manager Plus?
New to SharePoint Manager Plus?
New to ADManager Plus?