Log4j vulnerability - Denial of Service (CVE-2021-45105)
Hello everyone,
Another vulnerability has been detected in the fixes rolled out for Apache Log4j (Logging Library for Java. This vulnerability is tracked as CVE-2021-45105 and Apache Log4j2 versions 2.0-alpha1 through 2.16.0 are vulnerable. This vulnerability causes Denial of Service (DoS) attacks in the Web Server and could even crash said Web Server if a threat actor with control over Thread Context Map (MDC), crafts a malicious input data that contains a recursive lookup. This vulnerability has been assigned 'High' in the severity scale.
Resolution:
This vulnerability is fixed in Log4j 2.17.0. If you're running any software, especially web server applications, that uses Log4j versions 2.0-alpha1 through 2.16.0, kindly contact the respective software vendor for a patch or mitigation. For more details on mitigation, refer to this document.
Note: The below steps are applicable only to Desktop Central setups with endpoint security add-on enabled.
To detect affected network systems as well as the vulnerable web server installations on those systems,
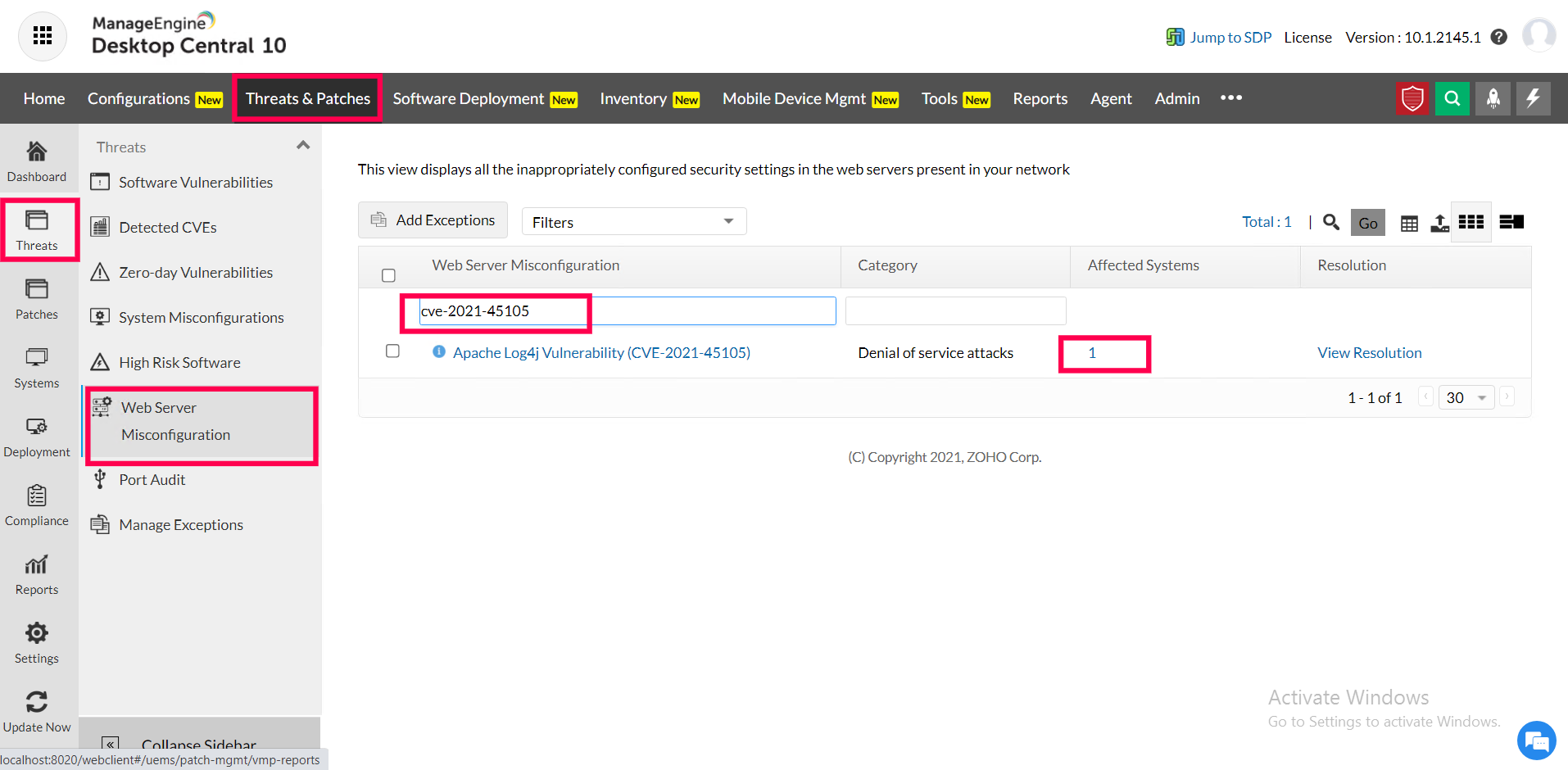
2) Navigate to Threats and patches> Threats > Web server misconfigurations
3) Search for "Apache Log4j Vulnerability (CVE-2021-45105)" to find affected Windows systems and "Apache Log4j Vulnerability (CVE-2021-45105) For Linux" to find affected Linux systems.
4) Under the affected systems column, you'll get a total count of systems affected by this vulnerability.
5) Clicking on it will reveal the affected systems.
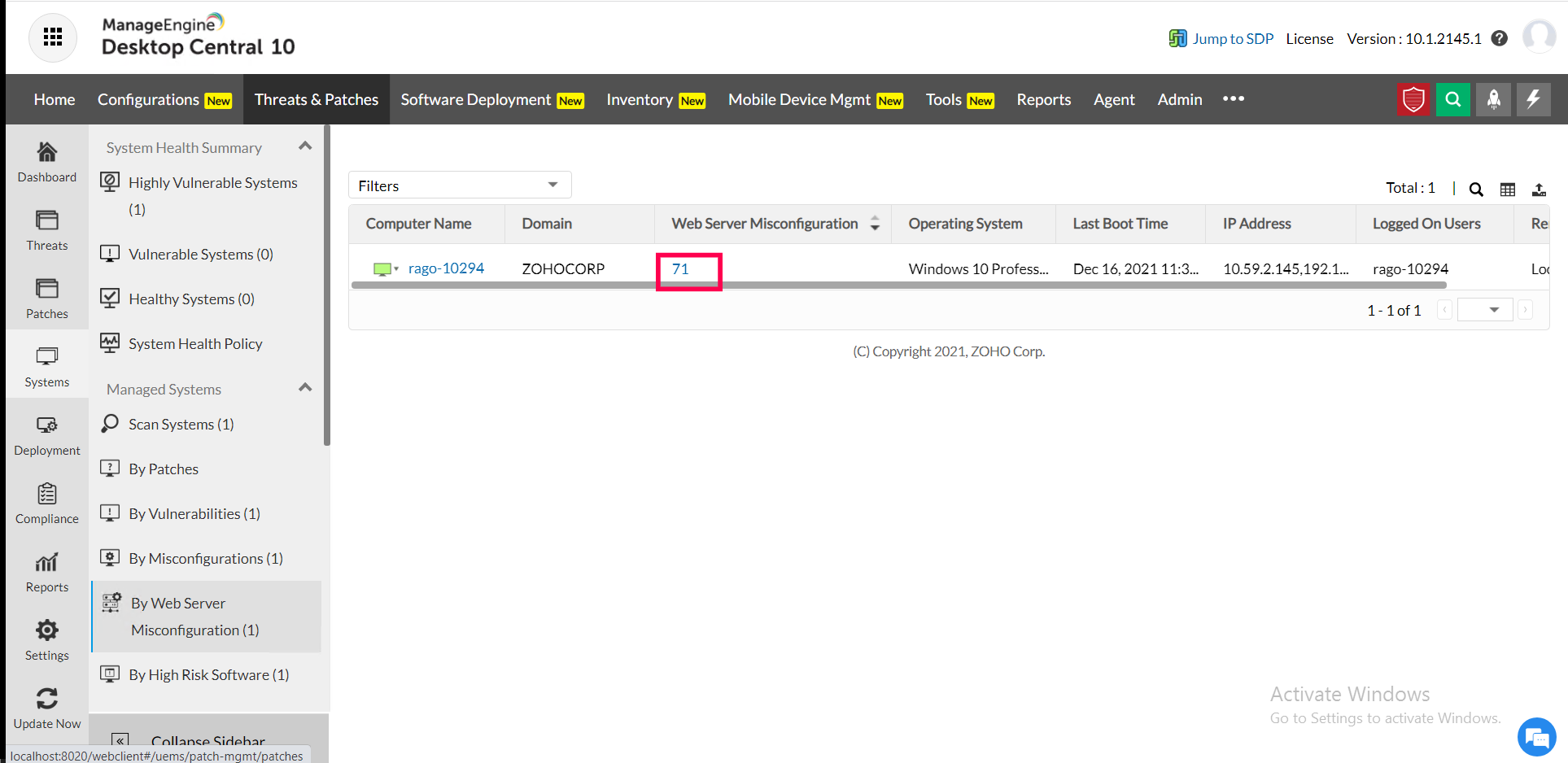
6) To view the exact web server installations on those systems that are affected by this vulnerability, click on the web server misconfiguration count available for each system.
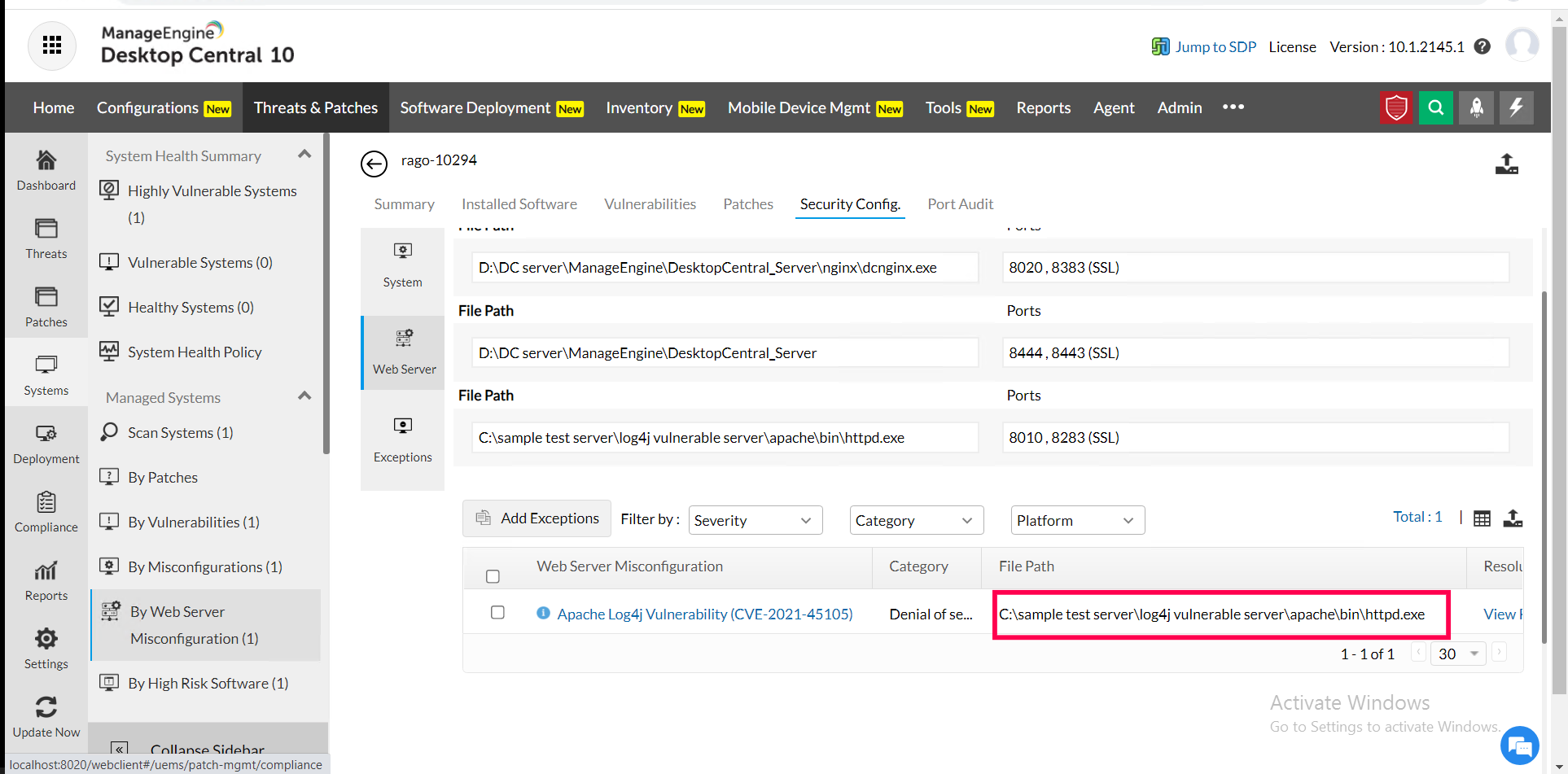
7) In the resulting table view, the "file path" column displays the home directory path or the exe path of the web servers affected by the Apache Log4j Vulnerability (CVE-2021-45105).
Alternatively, you can view all the affected systems in your network along with vulnerable web server installations on those systems in a report using a custom query. To do so,
1) Navigate to Reports > Query reports.
3) Use the below custom query based on your database type:
Select H.HARDENINGNAME as "Hardening Name",H.DESCRIPTION as "Description",H.FIXDESCRIPTION as "Resolution", hgd.name as "Category", STRING_AGG(distinct(rwh.FilePath),', ') as "File Path", pms.name as "Severity",STRING_AGG(distinct(Resource.name),', ') as Computer_Name from ResourceToWebHardening RWH inner join Hardening H on RWH.HardeningId=H.HardeningId inner join HardeningToGroupRel hgr on h.HardeningId=hgr.hardeningId inner join HardeningGroupDetails hgd on hgr.GroupId=hgd.GroupId inner join Resource on RWH.Resource_Id=Resource.Resource_Id inner join PMSeverity pms on H.Severity=pms.SeverityId where H.HardeningId in (381,1153) GROUP BY H.HARDENINGNAME,H.DESCRIPTION,H.FIXDESCRIPTION ,hgd.name,pms.name
For MSSQL setup:
Select H.HARDENINGNAME as "Hardening Name",H.DESCRIPTION as "Description",H.FIXDESCRIPTION as "Resolution", hgd.name as "Category",rwh.FilePath as "File Path", pms.name as "Severity",Resource.name as "Computer_Name" from ResourceToWebHardening RWH inner join Hardening H on RWH.HardeningId=H.HardeningId inner join HardeningToGroupRel hgr on h.HardeningId=hgr.hardeningId inner join HardeningGroupDetails hgd on hgr.GroupId=hgd.GroupId inner join Resource on RWH.Resource_Id=Resource.Resource_Id inner join PMSeverity pms on H.Severity=pms.SeverityId where H.HardeningId in (381,1153) GROUP BY H.HARDENINGNAME,H.DESCRIPTION,H.FIXDESCRIPTION ,hgd.name,pms.name,rwh.FilePath,Resource.name
Cheers,