Critical vulnerability CVE-2024-3094 in XZ Utils: Everything you need to know!
Hello everyone!
This forum talks in detail about the critical vulnerability CVE-2024-3094 which affects the XZ Utils, a widely used library found in both Mac and Linux distributions.
About the critical vulnerability
Tracked as CVE-2024-3094, this vulnerability in XZ Utils versions 5.6.0 and 5.6.1 poses a critical supply chain security issue and has been assigned a critical severity rating of 10/10.
XZ Utils is a command line tool that contains functionality for both compression and decompression of XZ files and liblzma. It is a widely used package present in Mac and major Linux distributions. As of now, it has been reported that the malicious code has infected Homebrew, Fedora Rawhide, Fedora 40 Beta, Fedora 41, Debian, OpenSUSE, Kali and Arch Linux.
Impact caused by this vulnerability
According to Red Hat, the malicious code modifies specific functions within the liblzma code, which is part of the XZ Utils package. This vulnerability may create a backdoor for unauthorized access, posing a threat to Mac and Linux platforms.
Under specific conditions, it could enable a threat actor to bypass sshd authentication, thereby facilitating unauthorized entry into a vulnerable system. Consequently, this allows an attacker to remotely execute code, gain unauthorized system privileges and potentially lead to data breaches.
Leverage ManageEngine Endpoint Central for detection
Endpoint Central simplifies vulnerability detection and provides a comprehensive insight into the affected systems. Curious about detecting vulnerabilities through Endpoint Central? Deploying a custom script from the product console is all it takes. To deploy the script,
- Login to the Endpoint Central web console.
- To deploy script to the Linux endpoints, navigate to the Configurations tab > Configuration > Linux > Custom Script. You can then deploy the script Linux_CVE-2024-3094_vulnerability_detector directly from the repository.
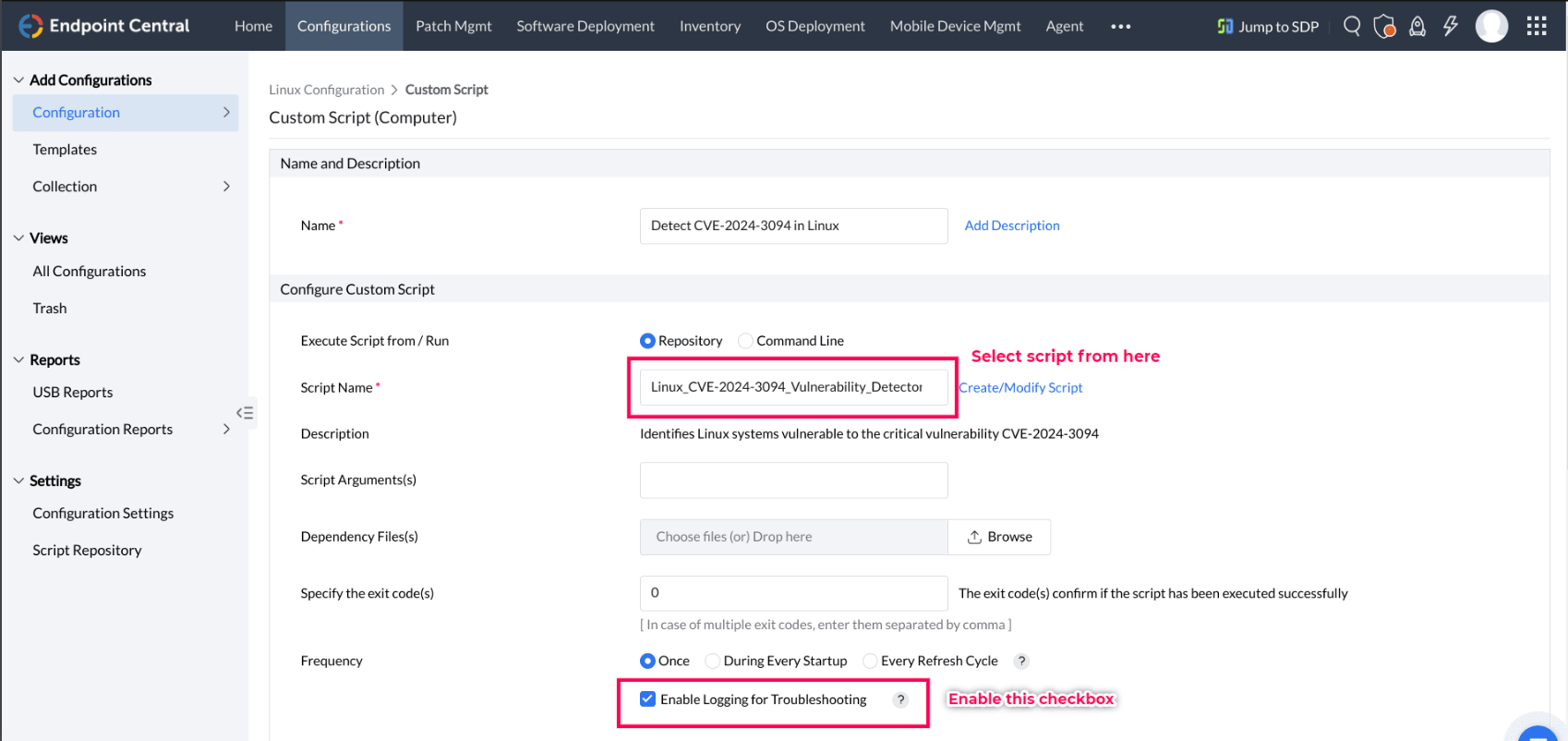
- Then to deploy script to the Mac endpoints, navigate to the Configurations tab > Configuration > Mac > Custom Script. You can then deploy the script Mac_CVE-2024-3094_vulnerability_detector directly from the repository.
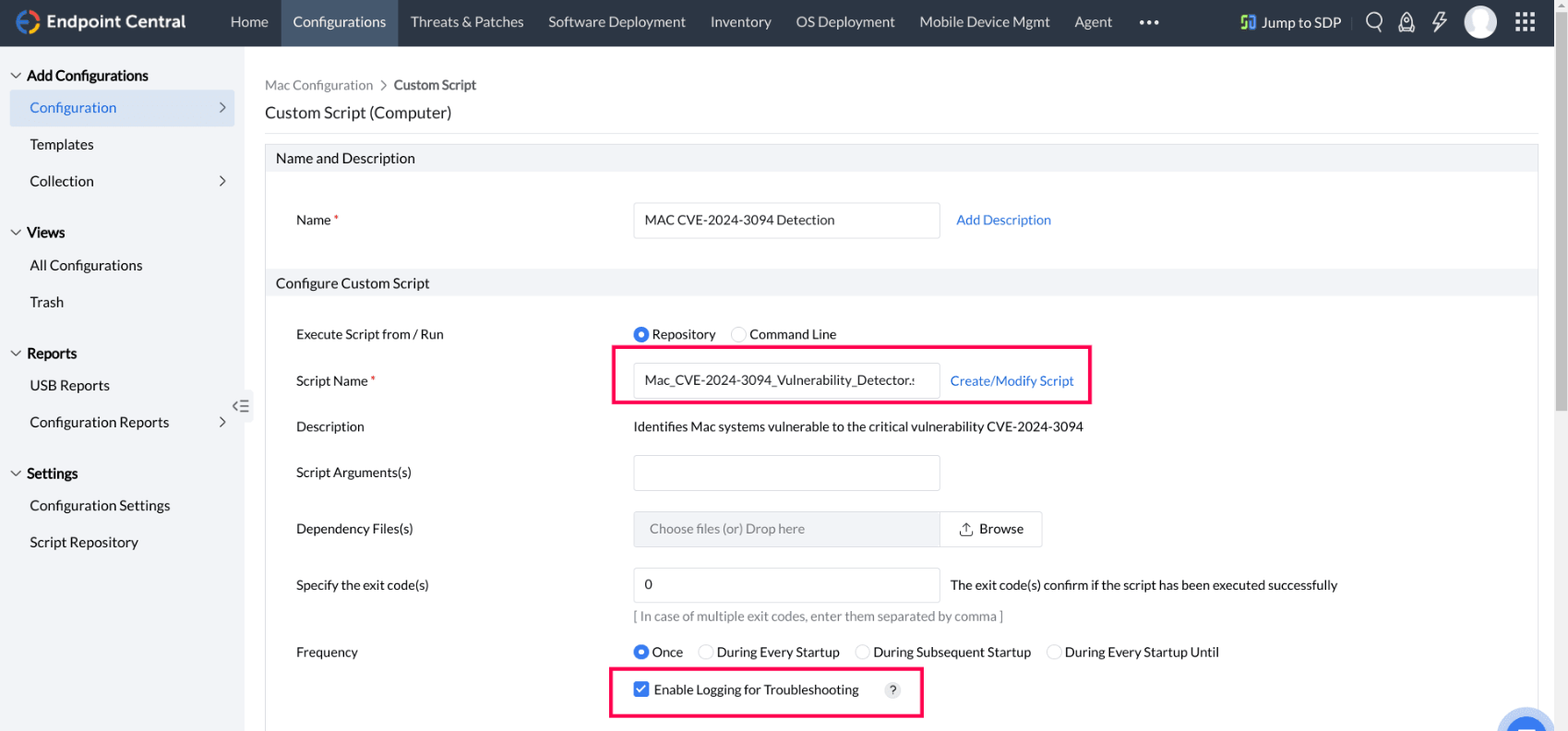
- Enable logging for troubleshooting to access the affected system details. Then select the required target for deploying the custom script.
- Navigate to the left pane and click on All Configurations to view the recent configurations you have created.
- You can then select the configuration you created to view the systems affected by this vulnerability within the Execution Status section.
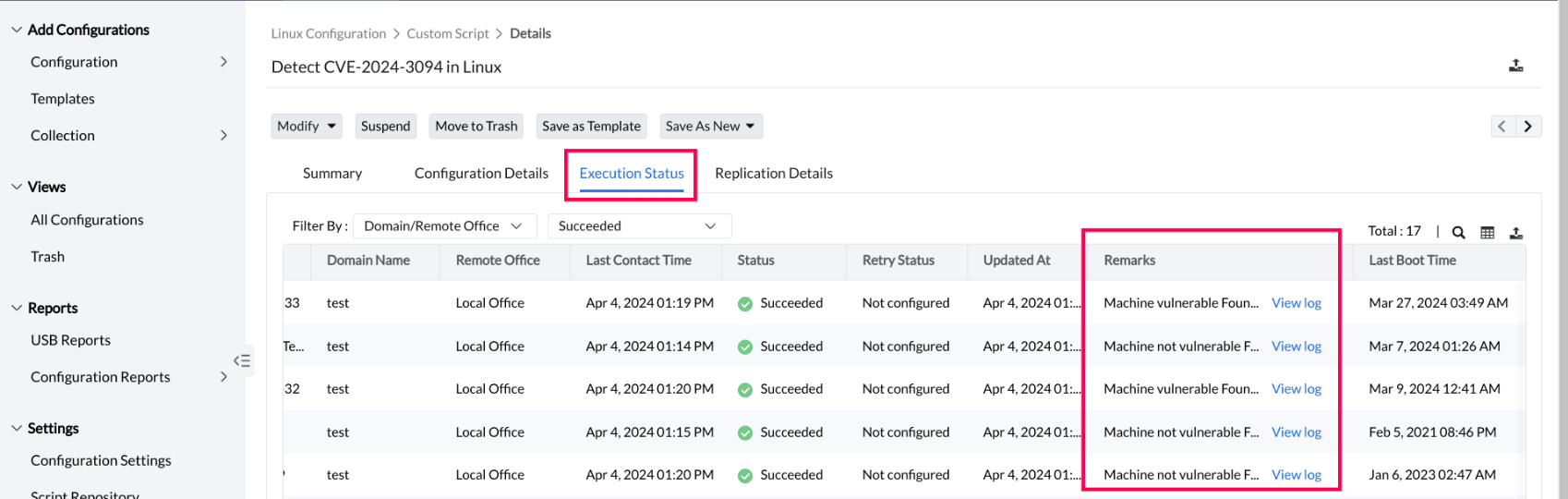
- In order to view the existing XZ Utils tool path and version details, click on View log.
Suggested mitigation from CISA
CISA has recommended users take immediate action to downgrade to the earlier version of xz (such as XZ Utils 5.4.6 Stable). Following the downgrade, it is advised to either reboot the systems or restart the OpenSSH server.
Stay vigilant while awaiting patches
It's important to stay vigilant while the official patches are yet to be released for the identified vulnerability. In the meantime, leverage ManageEngine Endpoint Central to proactively identify the systems impacted by this critical vulnerability by following the above-mentioned steps.
If you have any questions, feel free to comment below the post or contact us directly at endpointcentral-support@manageengine.com. We're here to help!
Cheers,
The ManageEngine Team