Breaking Active Directory passwords with brute-force
With the exponential rise in the number of enterprise applications, users tend to fall into the habit of
using weak passwords to secure their accounts. Hackers use this to their
advantage by targeting user accounts with sophisticated credential-based
attacks like brute force. After all, hackers only need one set of valid credentials to gain access to
the organization’s network and cause havoc.
Wouldn't it be great if you could
protect your business from cyberattacks by ensuring that users create hard-to-crack passwords
for all their enterprise accounts? We thought so too.
Are your users' passwords strong enough to stop hackers?

How ADSelfService Plus handles credential-based cyberattacks
ADSelfService Plus' Password Policy
Enforcer feature offers advanced password policy settings.
Organizations can keep up with the
evolving cyber threat landscape by:
- Banning leaked
or weak passwords, keyboard sequences, and palindromes.
- Restricting
consecutively repeated characters from the username or old password as
well as common character types at the beginning or end of passwords.
- Allowing users to use
Unicode characters in their passwords.
- Displaying a Password
Strength Meter when users change or reset their AD passwords.
- Enforcing passphrases instead
of password complexity rules if the password length is above a set number.
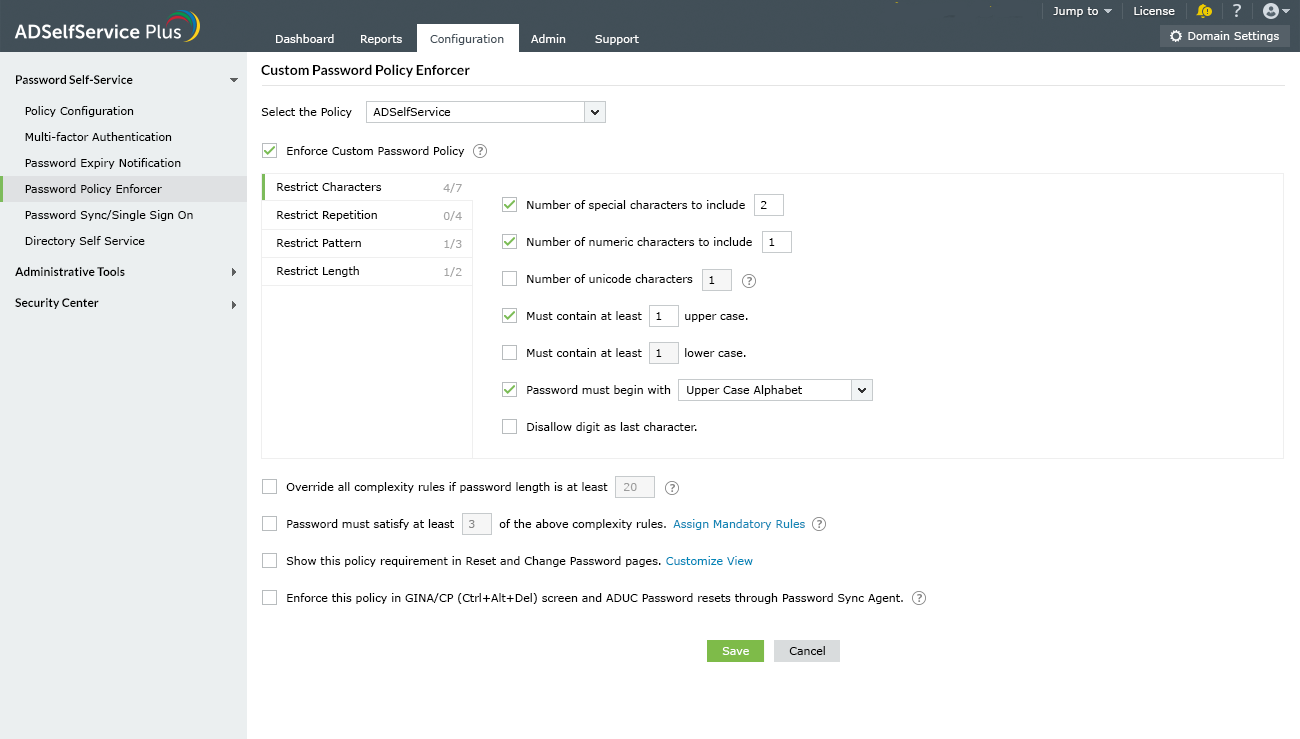
Fig 1: Password Policy Enforcer
Topic Participants
Vaishnavidevi