Apache Log4Shell vulnerability (CVE-2021-44228)
The identified Log4Shell vulnerability (CVE-2021-44228) is classified as a Zero-Day Vulnerability. The name Log4Shell refers to the fact that this bug is present in a popular Java logging library called Log4j, which when exploited, can allow attackers to potentially carry out Remote Code Execution via Shell commands. This vulnerability is patched in Log4j version 2.15.0 and above. Log4j versions 2.0.0 to 2.14.1 (except 2.12.2) are affected by this vulnerability.
This vulnerability is mainly due to improper validation of input during logging with Log4j, and also by default, unpatched Log4j versions (below 2.15.0) permit logging requests to trigger general-purpose Lightweight Directory Access Protocol (LDAP) searches, as well as various other online lookups. This attack vector can be utilized to send requests to external servers, which can be used by attackers to execute malicious codes remotely.
It is worth noting that Java Development Kit (JDK) versions greater than 6u211, 7u201, 8u191, and 11.0.1 are not affected by this vulnerability.
Resolution:
Apache suggests upgrading to Log4j version 2.15.0 to fix this vulnerability. If you're running any software in your network, especially web server applications, that uses Log4j versions from 2.0.0 to 2.14.1, kindly contact the respective software vendor to confirm the vulnerability impact and obtain mitigation details. For further information on this vulnerability, refer to this security advisory.
To detect affected network systems as well as the vulnerable web server installations on those systems,
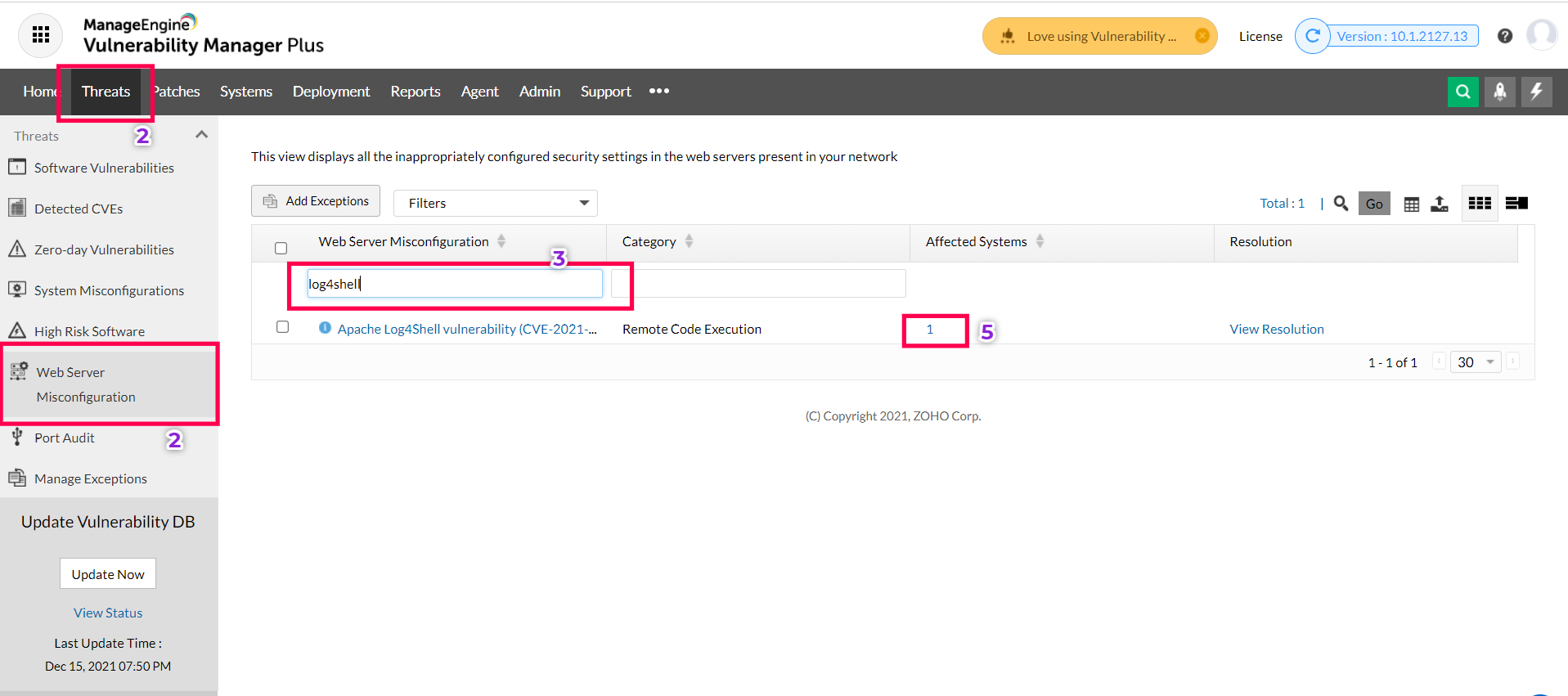
2) Navigate to Threats > Web server misconfigurations
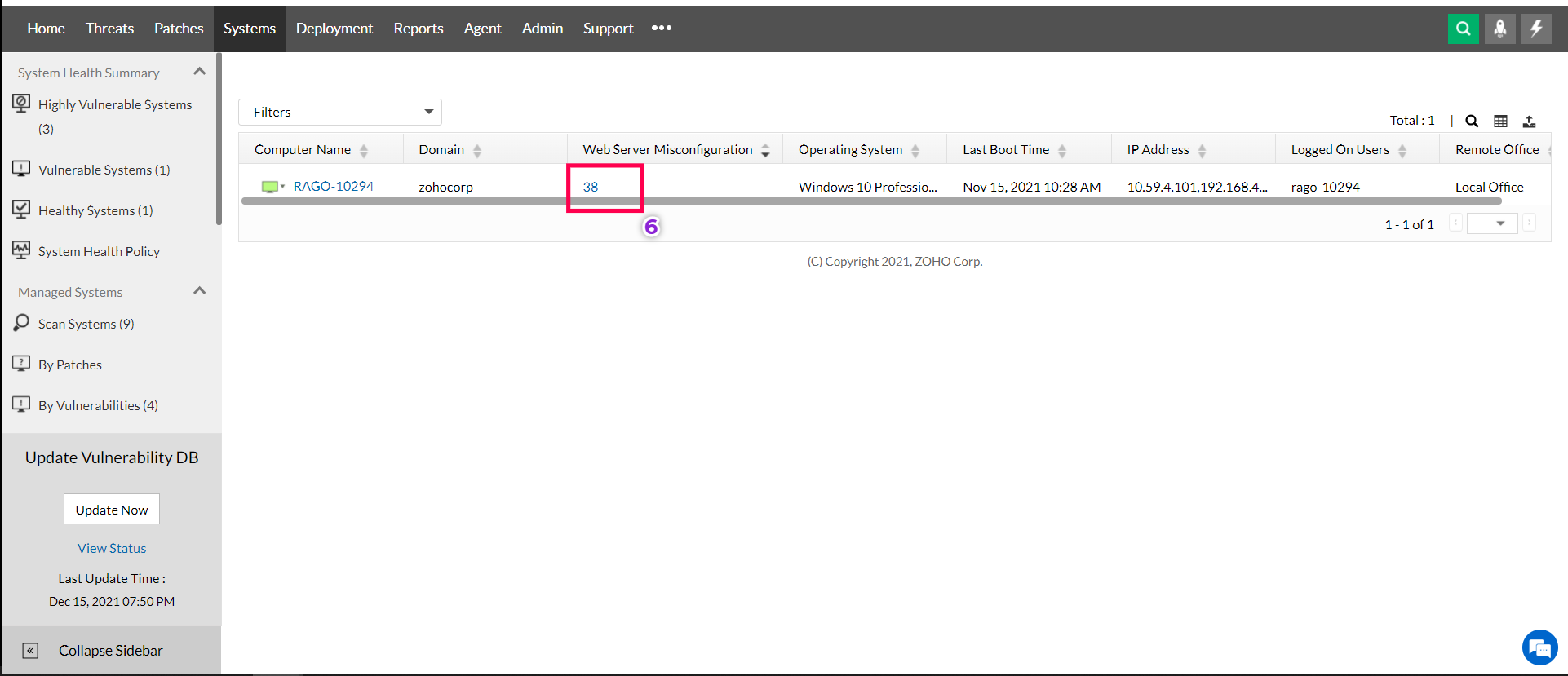
6) To view the exact web server installations on those systems that are affected by this vulnerability, click on the web server misconfiguration count available for each system.
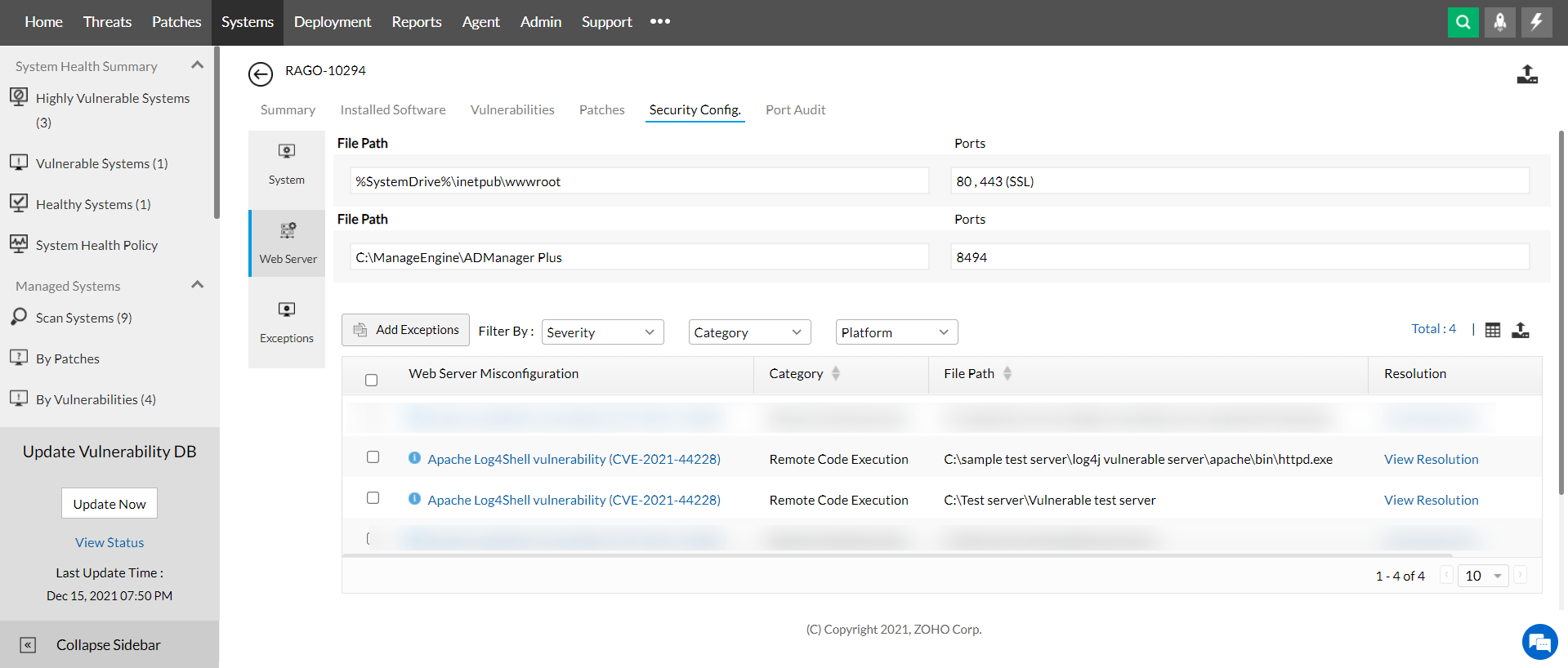
Alternatively, you can view all the affected systems in your network along with vulnerable web server installations on those systems in a report using a custom query. To do so,
1) Navigate to Reports > Query reports.
2) Click on New Query Report
3) Use the below custom query based on your database type:
For pgsql setup:
Select H.HARDENINGNAME as "Hardening Name",H.DESCRIPTION as "Description",H.FIXDESCRIPTION as "Resolution", hgd.name as "Category", STRING_AGG(distinct(rwh.FilePath),', ') as "File Path", pms.name as "Severity",STRING_AGG(distinct(Resource.name),', ') as Computer_Name from ResourceToWebHardening RWH inner join Hardening H on RWH.HardeningId=H.HardeningId inner join HardeningToGroupRel hgr on h.HardeningId=hgr.hardeningId inner join HardeningGroupDetails hgd on hgr.GroupId=hgd.GroupId inner join Resource on RWH.Resource_Id=Resource.Resource_Id inner join PMSeverity pms on H.Severity=pms.SeverityId where H.HardeningId in (379,1151) GROUP BY H.HARDENINGNAME,H.DESCRIPTION,H.FIXDESCRIPTION ,hgd.name,pms.name
For MSSQL setup: