TWTQ: Enable and disable correlation rules, alerts, and reports
Hey everyone!
Here's This Week's Top Question (TWTQ):
Q: How do I enable/disable correlation rules, alerts, and reports?
A: As EventLog Analyzer processes millions of network logs, its correlation engine matches them against various known security incident patterns. When a sequence of logs from your network matches one of these patterns, it is a possible attack. It then notifies you immediately via email or SMS and generates a detailed incident report. For instance, a brute force attack occurs when multiple logon failures are followed by a successful logon. EventLog Analyzer's correlation engine checks for this pattern, using the threshold values set by you, across all network logs and notifies you in case of such an incident.
The correlation module is flexible enough to fit all your needs - at any given time, you control which rules are enabled, whether you want a report for the rule within the product, or a notification to be raised, and if so what type of notification is sent out to whom.
You'll find all these options on the Manage Rules page:
Correlation > Manage Rules
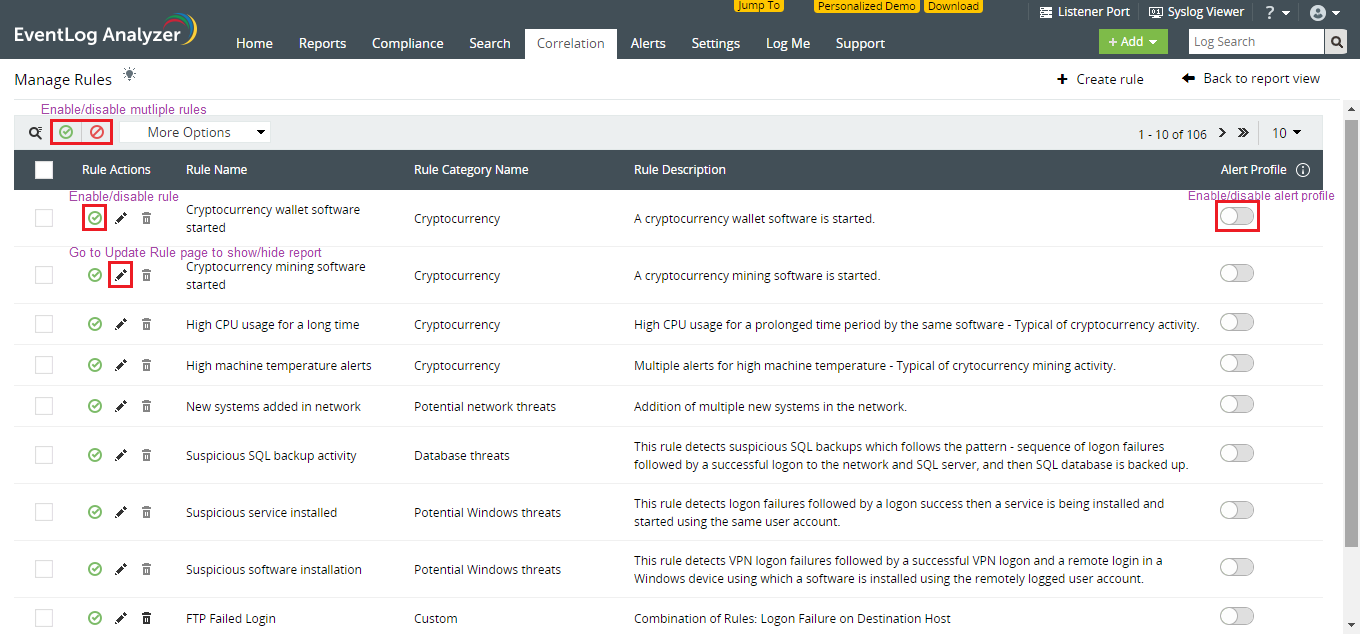
Enable or disable rules
You can enable/disable singular rules by using the icon next to the respective rule name, or multiple rules by using the icon on top of the table. Initially, no rule is enabled by default. You can select and enable those needed for your business requirements.
You can disable rules when they are not needed. When a rule is disabled, newly collected logs are not checked for the events that are specified in that rule. However, all information related to previously detected incidents will still be available in the respective report. Let's say you're conducting security checks on your database servers. You can temporarily disable all data breach related correlation rules to avoid false positives, and re-enable them when needed.
Note: Please enable rules with care, as correlation is a memory intensive process.
Enable or disable notifications
You can enable or disable alerts by using the slider icon next to the respective rule names. You can modify notification settings by going to the Manage Alert Profiles page in the Alerts tab.
For some incidents, you may simply need to conduct periodic reviews and may not require instant alerts. In such cases, you can disable alerts for the corresponding rule and simply make use of the aggregated incident reports which show you all occurrences of the incident for a selected time period.
For instance, consider a rule to track new machine account creation. You might not need notifications for this particular rule because multiple new machine accounts are created in an account for various purposes. However, you would like to regularly review this event to check nothing goes out of hand. In such cases, you can disable the notification, generate and review the report for this rule every fortnight or month for your IT auditing purposes.
Show or hide reports
To show or hide the report for a specific rule:
- Click on the 'Update rule' pencil icon next to the respective rule name.
- On the rule builder page which opens, click on the 'Update rule profile' pencil icon next to the rule name.
- Select/deselect the 'Show a report for this rule on the correlation dashboard' checkbox.
If you are tracking any incidents that warrant immediate action but do not require in-depth forensic investigation, you can choose to hide the report. In such cases you only receive real-time alerts for the rule but the incidents are not included on your correlation dashboard. For instance, you have a watchlist of users banned from accessing certain servers. You set up a rule for this scenario. When you receive alerts for the rule, you immediately block the users and do not need to conduct any further investigation. You can thus choose to hide the report from your correlation dashboard.
In this way, you can track various security incidents only when needed, and in the manner you want.